
When a hash becomes as dangerous as a password.
Read Details
Every time you send a message, log in, or buy something online, TLS is your digital bodyguard. It's simple, powerful, and everywhere.
Read Details
ISOAH is here to make your journey smooth, supported, and successful. The question is: Will you take the first step now, or regret missing the wave later?
Read Details
CompTIA PenTest+ is the cybersecurity industry's latest and greatest certification, designed to provide professionals with the ability to perform penetration testing tasks.
Read Details
Obtaining CompTIA Server+ knowledge and expertise is beneficial for professionals seeking to enhance their career. With this certification, servers can be securely installed and troubleshooting IT management skills properly deployed.
Read Details
CompTIA Cloud+ is the key to unlocking a world of opportunities in the dynamic realm of cloud computing. For aspiring beginners and career enthusiasts who want to work in the cloud platform, this certification offers a solid foundation to embark on a rewarding career in the cloud industry.
Read Details
Taking a CompTIA course in Linux provides numerous benefits for system administrators who are looking to advance their careers or stay up-to-date with changing technologies.
Read Details
CompTIA A+ is not just a certification; it's your ticket to the cutting-edge world of modern technology. In a digital landscape that evolves by the minute, A+ stands as the ultimate badge of proficiency for IT enthusiasts and professionals alike.
Read Details
For IT professionals who wish to take their career to the next level, having a globally recognized certification such as CompTIA Network+ is essential.
Read Details
The CompTIA Cybersecurity Analyst (CySA+) Certification is an internationally recognised cyber professional certification designed to help individuals stand out from the competition when looking to advance their careers in cybersecurity.
Read Details
Gaining a CompTIA Security+ certification is an important milestone for professionals looking to establish their credibility in the industry.
Read Details
A Bachelor's degree in Digital Forensics offers students a unique blend of technical skills, legal knowledge, and investigative techniques that are in high demand in today's digital landscape.
Read Details
Embarking on a career as a SOC Analyst is an exciting journey into the heart of cybersecurity. It's a path that offers continuous learning, a dynamic work environment, and the satisfaction of knowing you're protecting vital digital assets.
Read Details
The key is getting the necessary experience and certifications to land that first role. With hard work and persistence, you'll be well on your way to becoming a penetration tester and joining the front lines of cyber defence. The future is yours for the hacking!
Read Details
Web scraping has become a potent weapon in the wide digital realm, bridging the information and innovation divide. It's comparable to an explorer exploring the depths of the internet in search of priceless information nuggets that may be used to unlock countless opportunities.
Read Details
Bug bounty hunting is more than just a job—it's an exciting quest with limitless opportunities and unmatched rewards.
Read Details
The AWS Cloud Architecture course is a game-changer in the world of technology. With its comprehensive curriculum and hands-on approach, it equips individuals with the skills needed to design and manage scalable, reliable, and cost-effective cloud solutions using AWS services.
Read Details
With the increasing threat of cyberattacks, traditional methods of securing our networks and systems are no longer sufficient. Bug bounty programs offer a proactive and innovative approach to identifying vulnerabilities before they can be exploited by malicious actors.
Read Details
In today's digital age, cybercrime is becoming increasingly common and sophisticated, creating a growing demand for skilled professionals in the field of Computer forensics. Cyber forensics is an exciting and rapidly evolving field that requires a unique set of skills and knowledge to help solve complex cybercrime cases.
Read Details
From automating repetitive tasks to continuously testing and monitoring applications, DevOps practices can help teams achieve their goals while maintaining a culture of collaboration, innovation, and continuous improvement. DevOps has something to offer everyone.
Read Details
Join the millions of satisfied customers and experience the power of AWS EC2 today and easily access a plethora of services to meet your computing needs and accelerate your digital transformation!
Read Details
In today's increasingly connected world, networking skills are in high demand, and the CCNA certification is an excellent way to demonstrate your expertise in this area.
Read Details
Python is a high-level programming language that is widely used in various fields such as web development, data science, machine learning, scientific computing, and more. It is known for its readability, simplicity, and versatility, making it a popular choice for both beginners, intermediate and experienced developers.
Read Details
Cyber security is such a topic that will never end but will continue to improve as fraud increases. If you are grasping for career development as a cyber security analyst, then start learning now. Win against digital hostility. Are you still thinking?
Read Details
SysJoker is an Undetectable Malware affecting Multi Platform which is used for establishing access on a target machine. Once installed, it can execute code as well as additional commands, through which malicious hackers can carry out different attacks or pivot to move further into other network.
Read Details
Wi-Fis can be really open to attack if not the vulnerability is not assessed at the right moment. Know more about the technical tools on how to make the Wi-Fi more secured and check its vulnerability.
Read Details
Google provides time to time updates for all it's android os based users to provide best user experience and facilities. Android 12 is also part of it where we can expect more advanced features and security enhancements.
Read Details
Get Learn, what's new in the CHFI v10, a new version launched by Ec-Council for Computer Hacking Forensic Investigator global certification course. To join the global certification course, enroll yourself at ISOEH now!
Read Details
If you are thinking you are safe internet user and your digital assets, digital presence is secured because you are using two-factor authentication, hold on…
Read Details
Organizations use web applications with dynamic databases for providing better and various services to their customers. The services could be online banking which holding very sensitive data, universities that uses countless students' results, and different other government web applications. There are many attacks that cause a threat to database security such as Cross-Site Scripting Attack (XSS), phishing, Denial of Service (DoS), and SQL injection attack.
Read Details
A certified SOC analyst is the cyber security watcher of any company. They manage multiple SOC processes as well as collaborate with CSIRT (a Computer Security Incident Response Team) if need be. Our future is in the arms and on the lap of technology. It has already become an integral part of our personal as well as professional life.
Read Details
Certain ground rules are to be taken into consideration while working from home at the time of this pandemic crisis.
Read Details
As Facebook turns sixteen, let us check out some of the ways to safeguard your privacy at the same time be at the top of the game on it.
Read Details
The pace at which cyber crimes are rising, there has to be someone to catch the breaches and stop the nuisance. Cyber Forensic Experts are needed here to detect, analyze and mitigate the threat. Here, know about required skills, career opportunities if you want to become a Cyber Forensic Expert.
Read Details
Hackathons provide a unique environment where you can polish your skills and learn new technologies and work on your problem solving skills. Hackathons benefit both the participant and the organizer.
Read Details
Flutter is Google's evolutionary development platform that will allow programmers to write in one, simple language for both iOS and android phones. But before you embrace it, let's have a look at the pros and cons involved with Flutter.
Read Details
Think of a company who just tweeted something they shouldn't have - what would be the consequence? The company may face monetary as well as reputational damage. But how will you know if your twitter account is a victim of spammer attack? There are some warning signs you should be careful about.
Read Details
We often come across various hyperlinks that lead us to another page on the internet. But how can we understand if the destination is reliable or not? Here's how you can spot malicious link.
Read Details
A detailed analysis of the latest ATM Fraud that duped 78 customers of leading private and public sector banks who allegedly lost 20 Lac Rupees. Read to know how to avoid being duped.
Read Details
Cyber criminals are gaining access to confidential information, building, systems without any technical involvement but just by exploiting human psychology. Here, learn how Social Engineering works.
Read Details
Crypto-jacking is the unauthorized use of computing resources to mine cryptocurrencies. The trickiest aspect of cryptomining is it occurs in the background and shows no sign of it except overheating of the computer or slowing down. If you want to stop hackers from crypto-jacking your computer or avoid cryptomining altogether, here find a couple of options.
Read Details
Artificial Intelligence and Machine Learning - both the terms have become an integral part of many businesses but are often used interchangeably. To avoid the confusion, here is a guide to differentiate them.
Read Details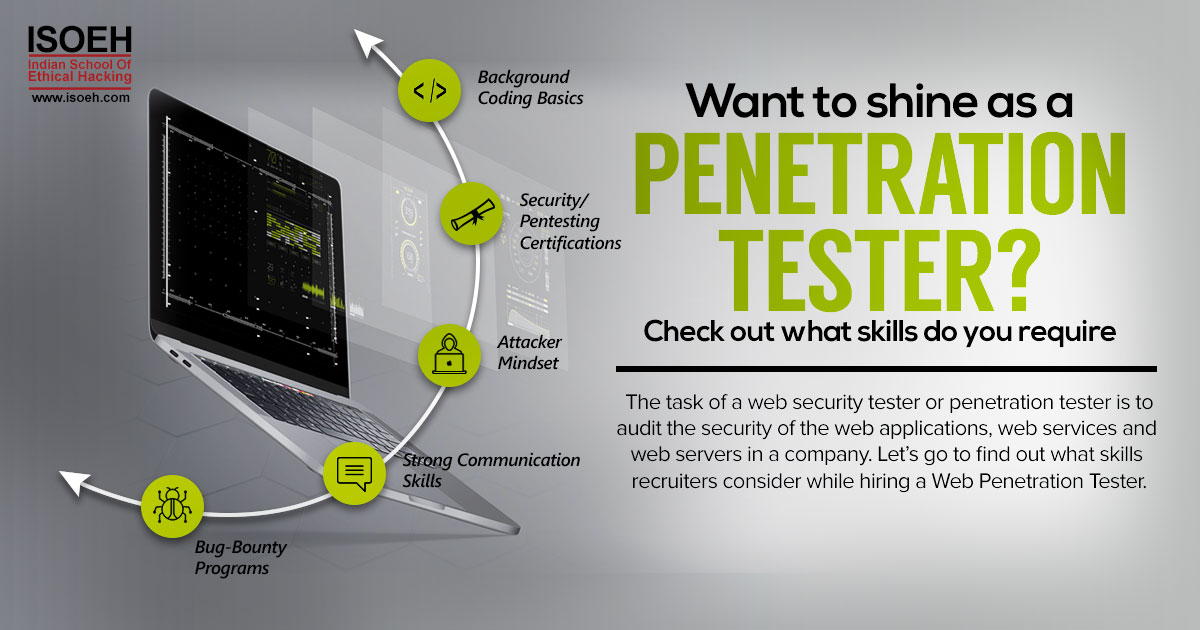
Penetration testing is the practice of testing a computer system, network or web application to find vulnerabilities that an attacker could exploit. The task of a web security tester or penetration tester is to audit the security of the web applications, web services and web servers in a company.
Read Details
This year will see a sharp increase in demand for professionals with skills in emerging technologies such as Artificial Intelligence (AI) and Machine Learning. Jobs related to Machine Learning are growing rapidly as companies try to get the most out of emerging technologies.
Read Details
A certified ethical hacker is appointed to handle the security issues of any network. To become one, candidates can take the CEH v9 bootcamp.
Read Details
Cyber-bullying is more dangerous than traditional bullying. In this case, the victim has no place to hide as the bullying takes place through communication tools including social media platforms, text messages, chat, and websites.
Read Details
In the last few decades, we have developed the habit of relying too much on our mobile devices. All our personal details along with social communication history are now within our devices which can be available to anyone who gets hold of the device, easily.
Read Details
If you are inquisitive by nature and dream to become a successful bug bounty hunter, the first thing you need is consistent, if not constant, attention.
Read Details
Wondering about the top tools for Wifi hacking? Here we are listing our favorites.
Read Details
How to disable ads from uTorrent? Here are some quick tips for those annoyed with uTorrent ads.
Read Details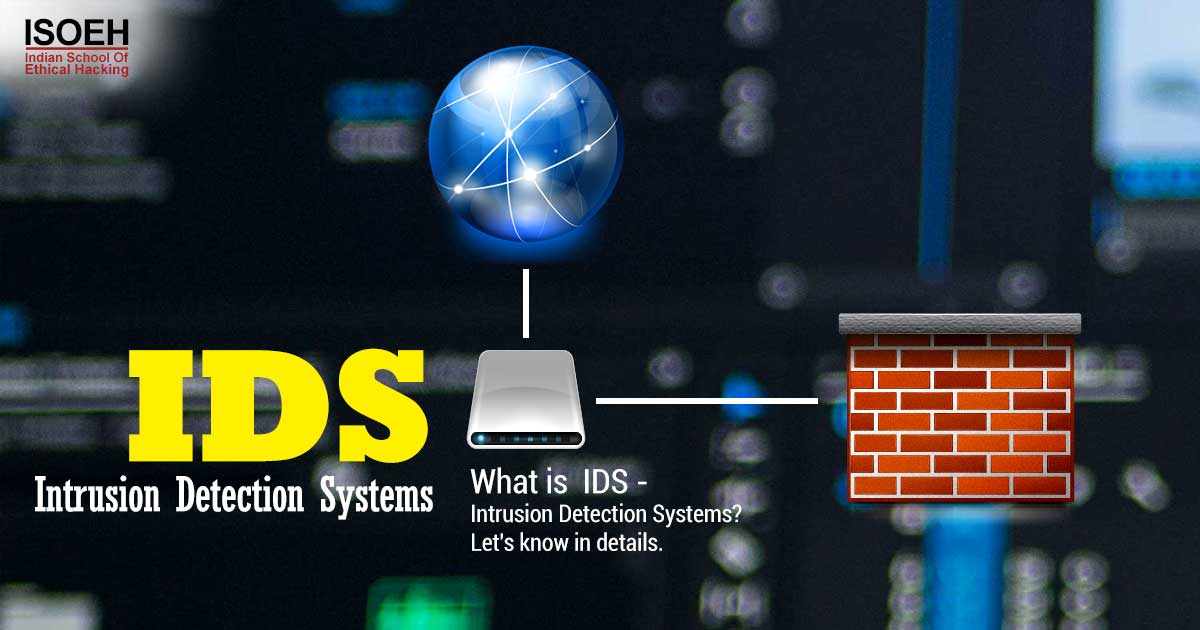
What is IDS - Intrusion Detection Systems? Let's know in details.
Read Details
What are the Data Security Standard for Payment Card Industry? Know here.
Read Details
Want to make a career as Web Pentesting consultant? Learn what skills and experience you need to become one.
Read Details

