Ethical Hacking is also called Penetration Testing. It is the best practice to penetrate the system or network to discover threats and vulnerabilities that a hacker may find and exploit leading to loss of data, money etc. The activity of an Ethical Hacker is the same as that of criminal hackers but with the authorities' permission. In simple language, "Ethical hacking involves an authorised attempt to gain unauthorised access to a computer system, application, or data."
What is the purpose of Ethical hacking?
- Secure digital assets: Ethical hacking protects data from cyber threats
- Identify vulnerabilities: It helps find and fix system weaknesses
- Compliance: Ensures adherence to industry standards and regulations
- Enhance security posture: Strengthens overall cybersecurity defences
- Career opportunities: Offers lucrative job prospects and growth potential
Why learn Ethical Hacking?
Regulatory compliance in terms of
Corporate Data Breaches
Professional
Development
Duration
40 hours - 2 classes per week
Eligibility
- Basic Knowledge of Database, Server-side Programming (PHP or JSP or ASP.net) and Basic knowledge of Networking.
- If you do not have the above knowledge, please complete our "INDUSTRY READY" Course to be eligible.
Course Fees
Class Room Training
Rs.14,500/-
Inclusive of all taxes
Online Training
Rs.24,500/-
Rs.14,500/-
Inclusive of all taxes
What You Will Get?
40 Hours
of in depth training by the best cyber security experts
Study Materials
Ethical Hacking
Certificate of Completion after examination and alumni status
Course Completion Certificate Example

Course Benefits:
- Comprehensive knowledge of cybersecurity threats
- Hands-on experience from Industry experts with cutting-edge tools
- Use the High-end Lab of the audit firm
- Certification enhancing job prospects and credibility
- Contribution to global cybersecurity defence
- Lucrative career opportunities with high-paying jobs
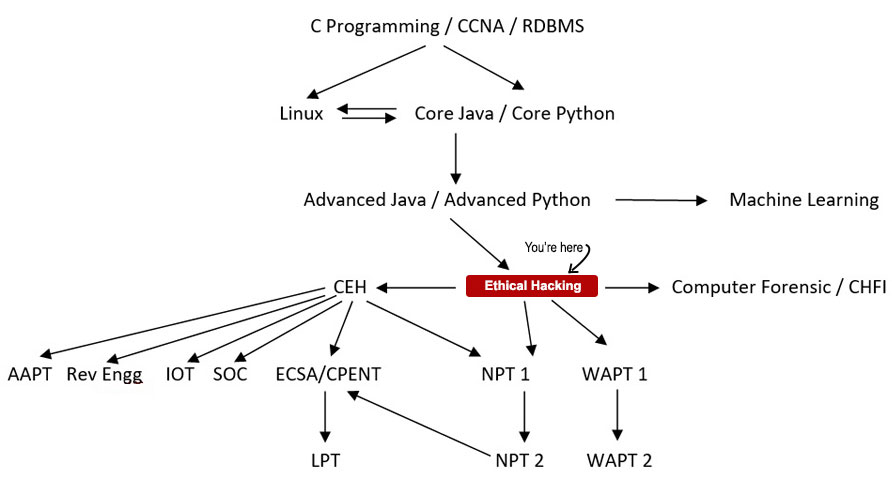
Roadmap to be an Ethical Hacker
Course Details
- The duration of the course is 40 hours at 2 hours per week
- The course fee is Rs.14,500/- for classroom and Rs.24,500/- Rs.14,500/- for online
- The curriculum is taught combining theory and practice
- What is Ethical Hacking (Day 1)
- What are the different types of hackers (Day 1)
- Five phases of hacking (Day 1)
- Scope of Ethical Hacking (Day 1)
- Passive Information Gathering (Day 2)
- Active Information Gathering (Day 2)
- Foot-Printing (Day 2)
- OSINT (Day 2)
- Port Scanning (Day 3)
- Network Sweeping (Day 3)
- Vulnerability Scanning (Day 3)
- Service Version Detection (Day 3)
- OS Fingerprinting (Day 3)
- Introduction to Metasploit Framework (Day 4)
- Introduction to Exploits & Payloads (Day 4)
- Type of Connections (Day 4)
- Exploit MS17-010 Vulnerability (Day 4)
- Introduction to Privilege Escalation (Day 5)
- Types of Privilege Escalation (Day 5)
- Bypassuac and getsystem (Day 5)
- Android Hacking (Day 6)
- Software based vulnerabilities (Day 6)
- Introduction to Active Directory Components (Day 7)
- LDAP in Active Directory (Day 7)
- Active Directory Functionality (Day 7)
- Service Principal Name (SPN) (Day 7)
- Kerberos Basics and Overview (Day 8)
- Components of Kerberos (KDC, Ticket Granting Ticket, etc.) (Day 8)
- Kerberos Authentication Process (Day 8)
- Kerberos Tickets and Encryption (Day 8)
- Introduction to Kerberos Attacks (Day 8)
- Introduction to Malware (Day 9)
- Types of Malwares (Viruses, Worms, Trojans, etc.) (Day 9)
- Malware Analysis Techniques (Day 9)
- Common Malware Distribution Methods (Day 9)
- Malware Detection and Prevention (Day 9)
- Introduction to Network Sniffing (Day 10)
- Passive vs. Active Sniffing (Day 10)
- Common Network Sniffing Tools (Day 10)
- Man-in-the-Middle (MITM) Attacks and Techniques (Day 10)
- Introduction to Cryptography (Day 11)
- Symmetric vs. Asymmetric Encryption (Day 11)
- Common Cryptographic Algorithms (e.g., AES, RSA) (Day 11)
- Steganography Techniques and Applications (Day 11)
- Introduction to Wireless Networks (Day 12)
- Types of Wireless Security Protocols (e.g., WEP, WPA, WPA2) (Day 12)
- Wireless Network Scanning and Enumeration (Day 12)
- Exploiting Wireless Vulnerabilities (Day 12)
- Introduction to Website Attacks (Day 13)
- How Website Attacks Work (Day 13)
- Types of Vulnerabilities Exploited (Day 13)
- Enumeration Techniques (Day 13)
- Introduction to Cross-Site Scripting (XSS) (Day 14)
- Understanding How XSS Works (Day 14)
- Types of XSS Attacks (Reflected XSS, Stored XSS, DOM-based XSS) (Day 14)
- Techniques for Detecting and Exploiting XSS Vulnerabilities (Day 14)
- Introduction to SQL Injection (SQLi) (Day 15)
- Mechanism of SQL Injection (Day 15)
- Common Types of SQL Injection Attacks (Union-Based, Blind SQLi, Error-Based) (Day 15)
- Techniques for Exploiting SQL Injection Vulnerabilities (Day 15)
- Introduction to Cross-Site Request Forgery (CSRF) (Day 16)
- How CSRF Attacks Work (Day 16)
- Examples of CSRF Exploitation (Day 16)
- Prevention and Mitigation Strategies (Day 16)
- Understanding Cookie Stealing and Session Hijacking (Day 17)
- Techniques for Cookie Stealing and Session Hijacking (Day 17)
- Data Tampering Attacks on Websites (Day 17)
- Phishing Attacks: Methods and Impacts (Day 17)
- File Upload Vulnerabilities: Risks and Exploitation (Day 17)
- Introduction to IoT Security (Day 18)
- IoT Device Identification and Enumeration (Day 18)
- Exploiting IoT Communication Protocols (Day 18)
- Webcam Attacks on IoT Devices (Day 18)
- Introduction to DDoS Attacks (Day 19)
- Types of DDoS Attacks (Day 19)
- DDoS Attack Techniques (Day 19)
- Cloud Security Fundamentals (Day 19)
- Introduction to IDS/IPS (Day 20)
- Types of IDS (Network-based, Host-based) (Day 20)
- Types of IPS (Network-based, Host-based) (Day 20)
- Honeypots (Day 20)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensics - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
Internet security and networking are the two sunshine industries where ethical hackers are employed. They can join government and private organizations as cyber-security experts. IT firms are the real recruiters of ethical hackers additionally needed by financial service providers, airlines, retail chains and hotels also. Government agencies such as various wings of the military and law enforcement, defence organisations, forensic laboratories, detective companies and investigative services also have interesting careers for ethical hackers. Some skilled hackers work for investigative agencies like the Central Bureau of Investigation, the National Security Agency and the Federal Bureau of Information. Some large organizations employ security testers and others use contractors to audit their systems.
A fresher may work as an intern for some time before finally starting job with 2.5 lakh per annum. With one year of experience, one can expect up to 4.5 lakh per annum. Those with work experience five years or more can rake in anything between 10-12 lakh per annum.
FAQs
- Introduction to Ethical Hacking
- Legality and Ethics
- Networking & Basics
- Foot Printing
- Google Hacking
- Scanning
- Enumeration
- System Hacking
- Windows Hacking
- Trojans & Backdoors
- Virus & Worms
- Sniffers
- Social Engineering
- Proxy Server & Packet Filtering
- Denial of Service Attack
- Phishing
- Session Hijacking
- Penetration Testing
- Vulnerability Assessment
- Linux Hacking
- Physical Security
- Hacking Web servers
- Web Application Vulnerabilities
- Web Based password Cracking Techniques
- SQL Injection Vulnerabilities
- Cryptography
- Wireless Network Hacking and Countermeasures
- Evading IDS, Firewalls and Detecting Honey Pots
- Buffer Overflows
- Reverse Engineering
- Hacking Database Servers
- Steganography
- Spying Technologies
- Hacking Routers and Firewalls
- Computer Forensics and Incident Handling
- Botnets
- Hacking emails
- Privacy on the Internet
- Creating Security Policies
- Exploit Writing
- Patch Management
- Covering Tracks
The duration of the course is 40 hours at 2 classes per week.
The course is administered in theory as well as practice.
The pre requisites of the course are Basic knowledge of Database, Server side Programming (PHP or JSP or ASP.net) and basic knowledge of Networking.
The top organizations like such as Infosys, Wipro, TCS, Tech Mahindra, IBM etc. are seeking good ethical hackers. The profiles that are on offer include Security Executive, Web Security Manager/Administrator, Network Security Administrator, Network Security Systems Manager and much more.
The courses are NPT, WAPT, AAPT, IOS Application Penetration Testing etc which can be followed after this course.
Course Fees
Rs.24,500/-Rs.14,500/-
Inclusive of all taxes
Batches
Weekend Batches for Bhubaneswar Center:
Mar, 2026
Mar, 2026
May, 2026
Weekend Batches for Kolkata Center:
Mar, 2026
Mar, 2026
May, 2026
Weekday Batches for Siliguri Center:
Mar, 2026
Mar, 2026
May, 2026
Member of: