Penetration testing, also called pen testing or ethical hacking, is the practice of testing a computer system, network or web application to find security vulnerabilities that a hacker could target. Penetration testing can be automated with software applications or performed manually.
Why learn Network Penetration Testing?
Meeting
Monitoring Necessities
and avoiding penalties
Circumventing the rate of
Network Downtime
Duration
40 hours - 2 classes per week
Eligibility
- Good Knowledge of Networking on Windows and Linux
- MCSE/CCNA/RHCSA & RHCE are preferred
Course Fees
Class Room Training
Rs.14,750/-
Inclusive of all taxes
Online Training
Rs.24,750/-
Rs.14,750/-
Inclusive of all taxes
What You Will Get?
40 Hours
of in depth training by the best cyber security experts
Study Materials
Network Penetration Testing Level I
Certificate of Completion after examination and alumni status
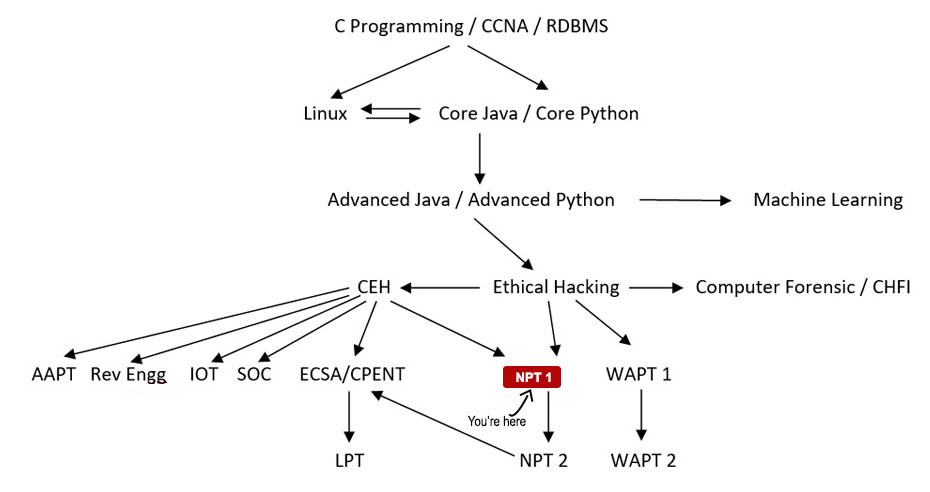
Your Course Path
Course Details
- The duration of the course is 40 hours - 2 classes per week
- The course fee is Rs.14,750/- for classroom and Rs.24,750/- Rs.14,750/- for online
- The course is taught in theory as well as practice
- Purpose and Scope of Penetration Testing (Day 1)
- Penetration Testing Methodologies (Day 1)
- Legal and Ethical Considerations (Day 1)
- Reporting and Documentation (Day 1)
- Setting Up Virtualization Environments (e.g., VMware, VirtualBox) (Day 2)
- Creating and Configuring Network Segments (Day 2)
- Deploying Target Machines (e.g., Windows, Linux) (Day 2)
- Tools Installation and Configuration (Day 2)
- Understanding SNMP Versions (SNMPv1, SNMPv2c, SNMPv3) (Day 3)
- SNMP Walk and SNMP Get Methods (Day 3)
- Community String Guessing (Day 3)
- MIB (Management Information Base) Analysis (Day 3)
- SNMP Community String Attack (e.g., SNMP Dictionary Attack) (Day 4)
- Exploiting Vulnerable SNMP Services (Day 4)
- Introduction to Brute Forcing (Day 5)
- Tools for Protocol Brute Forcing (Day 5)
- HTTP Basic/Digest Authentication Brute Forcing (Day 5)
- SSH/FTP/Telnet Brute Force Attacks (Day 5)
- Understanding HTTP Tunneling Concepts (Day 6)
- Tools for HTTP Tunneling (Day 6)
- Using HTTP Tunneling for Data Exfiltration (Day 6)
- Evading Firewalls and IDS/IPS with HTTP Tunneling (Day 6)
- Port Scanning Techniques (e.g., TCP Connect Scan, SYN Scan) (Day 7)
- Full Port Scanning vs. Top Ports Scanning (Day 7)
- Service Version Detection (Day 7)
- Firewall Evasion Techniques (Day 7)
- Understanding DLL Search Order Hijacking (Day 8)
- Identifying DLL Hijacking Vulnerabilities (Day 8)
- Exploiting Applications with DLL Hijacking (Day 8)
- Mitigating DLL Hijacking Attacks (Day 8)
- Introduction to NetBIOS and SMB Protocols (Day 9)
- Enumerating NetBIOS Information (e.g., nbtstat, smbclient) (Day 9)
- SMB Version Detection and Enumeration (Day 9)
- Extracting User and Share Information (Day 9)
- Enumerating SMB Shares (e.g., smbclient, smbmap) (Day 10)
- NFS Enumeration (showmount, nfsstat) (Day 10)
- Finding Vulnerabilities in SMB and NFS Implementations (Day 10)
- Accessing and Interacting with Shared Resources (Day 10)
- Basic Privilege Escalation Techniques (Day 11)
- Exploiting Unquoted Service Paths (Day 11)
- DLL Hijacking for Privilege Escalation (Day 11)
- Exploiting Weak Registry Permissions (Day 11)
- Maintaining Access After Exploitation (Day 12)
- File System Navigation and Data Extraction (Day 12)
- Privilege Escalation Beyond Initial Access (Day 12)
- Basic Linux Privilege Escalation Techniques (Day 13)
- Exploiting Weak File Permissions (Day 13)
- Exploiting Shell Escape Vulnerabilities (Day 13)
- Exploiting Cron Jobs and Weak File Permissions (Day 13)
- Advanced Linux Privilege Escalation Techniques (Day 14)
- Exploiting Capabilities and Kernel Vulnerabilities (Day 14)
- Exploiting Sudo Misconfigurations (Day 14)
- Exploiting SUID/GUID Binaries (Day 14)
- Removing Evidence of Compromise (EOC) (Day 15)
- Modifying Logs and Timestamps (Day 15)
- Deleting Backdoors and Persistence Mechanisms (Day 15)
- Techniques to Evade Forensic Analysis (Day 15)
- Introduction to Pivoting in Penetration Testing (Day 16)
- Using Proxychains and SSH Tunnels for Pivoting (Day 16)
- Port Forwarding Techniques (Day 16)
- Exploiting Internal Network Vulnerabilities from Compromised Hosts (Day 16)
- Introduction to Mimikatz (Day 17)
- File Transfer (Day 17)
- Introduction to PowerShell (Day 17)
- WMIC (Day 17)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensics - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
As per IT industrial study penetration testers have been bracketed with information security analysts. A very high rate of job growth is expected for penetration testing professionals in this field. From 2016 to 2026, as per studies, a 28% rate of growth will be seen in the field of penetrating testing, which is four times the national average job growth rate for all occupations.
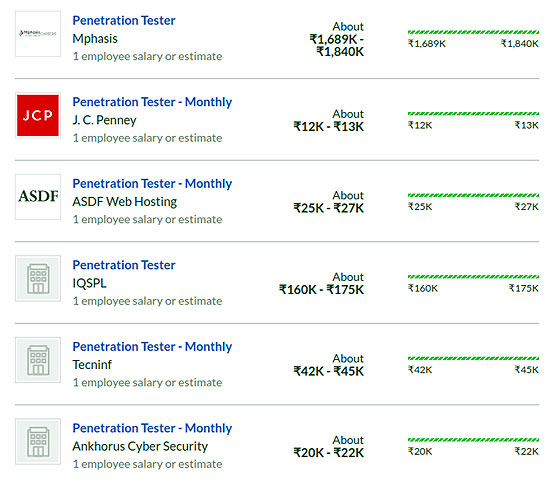
The average salary for a Penetration Tester is Rs.6,06,118 per year in India.
A company wise break down of the salary quotient is as follows,
FAQs
Types of Penetration Testing, Vulnerability vs Penetration Testing, Metasploit Basics, Intelligence gathering (Passive and Active), Port scanning in depth, Scanning Server Message Block, FTP Scanning, Scanning a network, Basics of Exploitation, Exploiting Windows and Linux OS, Brute Forcing Ports, Privilege Escalation, Creating Stand alone binaries with MSF payload, Evading Antivirus, Exploitation using Client side attack, Browser based attack, File format exploit, Social Engineering Toolkit, Web attack vectors, Client side web exploits, Simulated Penetration Testing, Exploiting web servers for Basic.
The duration of the course is 40 hours at 2 classes per week.
The course is taught in theory as well as practice.
The course prerequisites are Good Knowledge of Networking on Windows and Linux. MCSE/CCNA/RHCSA & RHCE is preferred for Basic.
As per IT industrial study penetration testers have been bracketed with information security analysts. A very high rate of job growth is expected for penetration testing professionals in this field. From 2016 to 2026, as per studies, a 28% rate of growth will be seen in the field of penetration testing, which is four times the national average job growth rate for all occupations.
You can go for Network Penetration Testing Level II after this.
Course Fees
Rs.24,750/-Rs.14,750/-
Inclusive of all taxes
Batches
Weekday Batches for Bhubaneswar Center:
Feb, 2026
Feb, 2026
Apr, 2026
Weekend Batches for Kolkata Center:
Feb, 2026
Feb, 2026
Apr, 2026
Member of: