ISO 9001:2015 Certified by BSI
ISO 9001:2015 Certified by BSI ISO 27001:2022 Certified by SGS
ISO 27001:2022 Certified by SGS Accredited Training Center
Accredited Training Center Authorized Test Center
Authorized Test Center Authorized Partner
Authorized Partner Empanelled Security Audit Firm
Empanelled Security Audit FirmGet Taught By Professional Hackers
Indian School of Ethical Hacking
Courses
Duration
Fees
I am interested in Software Development
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
or
or
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
Ethical Hacking (Advance Level)
Level V
Level V
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
WAPT Level I (Web Application Penetration Testing)
Level VI
Level VI
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,750/-
Inclusive of all taxes
Inclusive of all taxes
WAPT Level II (Web Application Penetration Testing)
Level VII
Level VII
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,750/-
Inclusive of all taxes
Inclusive of all taxes
I wish to become a Network Engineer
CCNA (Cisco Certified Network Associate)
Level I
Level I
40 hours
(2 classes / week)
(2 classes / week)
Rs. 13,000/-
Inclusive of all taxes
Inclusive of all taxes
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
or
or
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
Ethical Hacking (Advance Level)
Level II
Level II
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
NPT (Network Penetration Testing)
Level III
Level III
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,750/-
Inclusive of all taxes
Inclusive of all taxes
I want to get an overview on Hacking & Security
I want Short-term Training / Internship
Courses
Duration
Fees
CCNA (Cisco Certified Network Associate)
Level II
Level II
40 hours
(2 classes / week)
(2 classes / week)
Rs. 13,000/-
Inclusive of all taxes
Inclusive of all taxes
Ethical Hacking (Advance Level)
Level III
Level III
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
Courses
Duration
Fees
I am interested in Software Development
Linux 8.0 (RHCSA & RHCE)
Level I
Level I
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
Level II
Level II
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
I am a Network Professional
Linux 8.0 (RHCSA & RHCE)
Level I
Level I
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
CCNA (Cisco Certified Network Associate)
Level II
Level II
40 hours
(2 classes / week)
(2 classes / week)
Rs. 13,000/-
Inclusive of all taxes
Inclusive of all taxes
CCNP - Switch (Cisco Certified Network Professional - Switch)
Level III
Level III
40 hours
(2 classes / week)
(2 classes / week)
Rs. 9,000/-
Inclusive of all taxes
Inclusive of all taxes
CCNP - Router (Cisco Certified Network Professional - Router)
Level IV
Level IV
40 hours
(2 classes / week)
(2 classes / week)
Rs. 9,000/-
Inclusive of all taxes
Inclusive of all taxes
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
Level V
Level V
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
I am a Security Professional
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
I am a Police/Lawer/Detective/Forensic Expert
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
CHFI v11 (Computer Hacking Forensic Investigator - EC Council - Global Certification)
40 hours
(2 classes / week)
(2 classes / week)
Rs. 47,999/-
Inclusive of all taxes
Inclusive of all taxes
Courses
Duration
Fees
CCNA (Cisco Certified Network Associate)
Level I
Level I
40 hours
(2 classes / week)
(2 classes / week)
Rs. 13,000/-
Inclusive of all taxes
Inclusive of all taxes
CCNP - Switch (Cisco Certified Network Professional - Switch)
Level II
Level II
40 hours
(2 classes / week)
(2 classes / week)
Rs. 9,000/-
Inclusive of all taxes
Inclusive of all taxes
CCNP - Router (Cisco Certified Network Professional - Router)
Level III
Level III
40 hours
(2 classes / week)
(2 classes / week)
Rs. 9,000/-
Inclusive of all taxes
Inclusive of all taxes
CEH v13 - AI Powered (Certified Ethical Hacker - EC Council - Global Certification)
or
or
40 hours
(2 classes / week)
(2 classes / week)
Rs. 51,999/-
Inclusive of all taxes
Inclusive of all taxes
Ethical Hacking (Advance Level)
Level IV
Level IV
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
Firewall Administration
Level V
Level V
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
Linux 8.0 (RHCSA & RHCE)
Level VI
Level VI
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
NPT (Network Penetration Testing)
Level VII
Level VII
40 hours
(2 classes / week)
(2 classes / week)
Rs. 14,500/-
Inclusive of all taxes
Inclusive of all taxes
I want to get an overview on Hacking & Security
Know Your Faculty
All courses Available Online with LAB
(Uses Google Meet & TeamViewer)
Enroll Now!
(Uses Google Meet & TeamViewer)
Branches
Details
Exclusive Blog
Exclusive Blog
Latest cyber security news, trends and researches discussed in detail
Latest cyber security news, trends and researches discussed in detail
Verified Student List
If you're a student of ISOEH, your name should show up on alumni page. We've come to know that there are few fake institutions providing certificates in our name. If your name doesn't pop up on alumni page, please write to us at [email protected] or send a whatsapp message to 9830310550. If you are a valid student of ours, we will add your name thereafter. HR personnel & recruiters are requested to check the student name and each course name from alumni page for authenticity.
View AllBreaking News
Breaking News
Be the first to know
Be the first to know
Tools
Tools
Your one stop place for best hacking tools on the web
Your one stop place for best hacking tools on the web
Tutorials
Tutorials
Learn it yourself
Learn it yourself
Original Articles & Findings
Original Findings
Original articles straight from our R&D Lab
Original articles straight from our R&D Lab
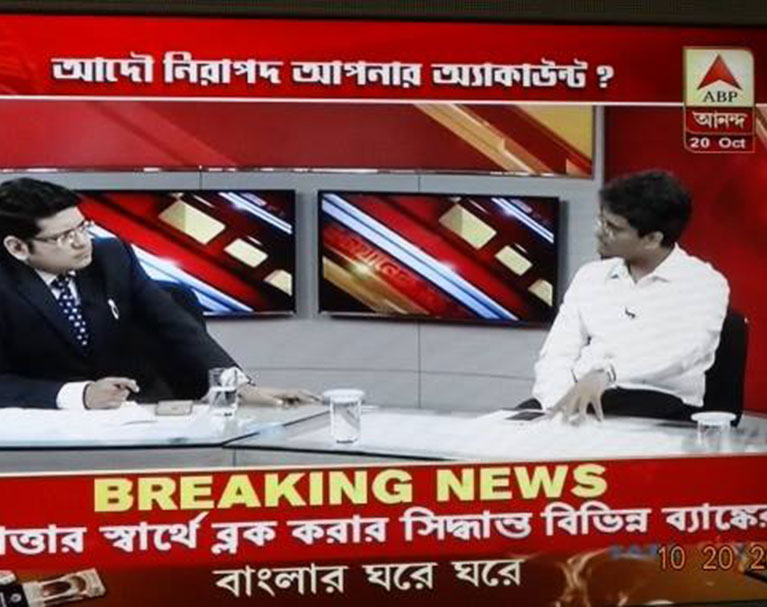
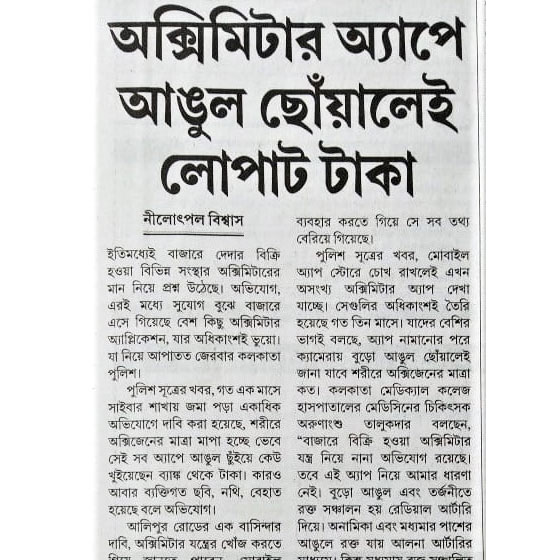
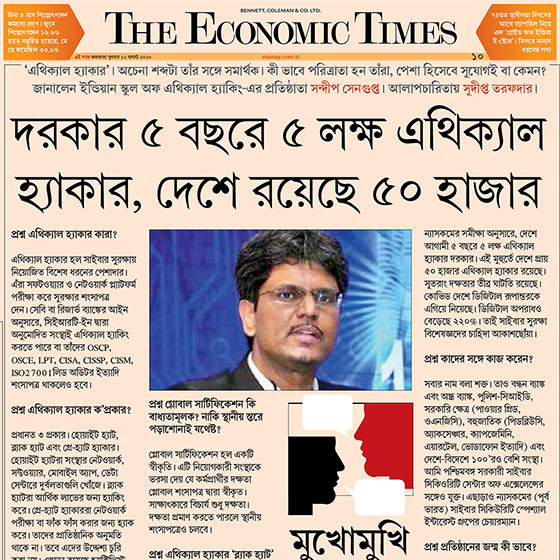
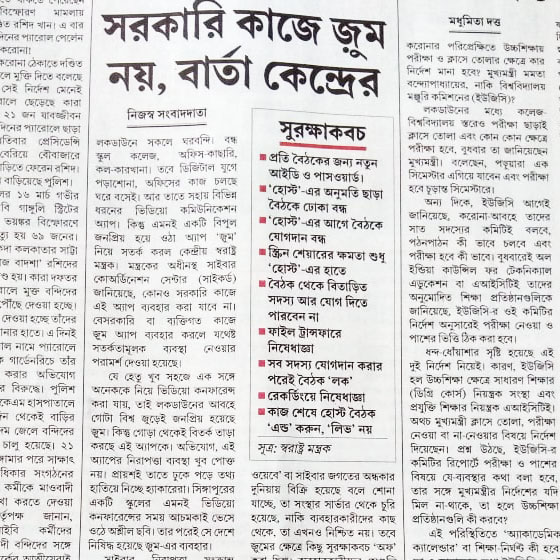
Cyber Fraud - ফেসবুক চ্যাট এ ব্ল্যাকমেল এর ফাঁদ! Mr. Sandeep Sengupta Live on ABP Ananda Exclusive.
Our Clients




















































































































































































| Course | Batch | Reg. Date | Class Start | Class End | Day & Time | Fee | |
|---|---|---|---|---|---|---|---|
| Course: Certified Ethical Hacker - CEH v13 - AI Powered | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 5th March 2026 | Class Start: 7th March 2026 | Class End: 16th May 2026 | Day & Time: Saturday 3:00pm - 7:00pm |
Fee: Rs.51,999/- Inclusive of all taxes |
Enroll Now | |
| Reg. Date: 2nd April 2026 | Class Start: 4th April 2026 | Class End: 13th June 2026 | Day & Time: Saturday 10:00am - 2:00pm |
||||
| Course: CHFI v11 - Computer Hacking Forensic Investigator | |||||||
| Batch: Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 6th March 2026 | Class Start: 8th March 2026 | Class End: 17th May 2026 | Day & Time: Sunday 3:00pm - 7:00pm |
Fee: Rs.57,999/- Rs.47,999/- Inclusive of all taxes |
Enroll Now | |
| Course: C Programming | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekday batches) | Reg. Date: 6th April 2026 | Class Start: 8th April 2026 | Class End: 24th June 2026 | Day & Time: Wednesday & Friday 10:00am - 12:00pm |
Fee: Rs.18,750/- Rs.8,750/- Inclusive of all taxes |
Enroll Now | |
| Course: Advance Database (Oracle, RDBMS) | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekday batches) | Reg. Date: 6th April 2026 | Class Start: 8th April 2026 | Class End: 24th June 2026 | Day & Time: Wednesday & Friday 5:00pm - 7:00pm |
Fee: Rs.18,750/- Rs.8,750/- Inclusive of all taxes |
Enroll Now | |
| Course: Ethical Hacking | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 5th March 2026 | Class Start: 7th March 2026 | Class End: 16th May 2026 | Day & Time: Saturday 3:00pm - 7:00pm |
Fee: Rs.24,500/- Rs.14,500/- Inclusive of all taxes |
Enroll Now | |
| Reg. Date: 2nd April 2026 | Class Start: 4th April 2026 | Class End: 13th June 2026 | Day & Time: Saturday 10:00am - 2:00pm |
||||
| Course: Computer Forensic | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 6th March 2026 | Class Start: 8th March 2026 | Class End: 17th May 2026 | Day & Time: Sunday 3:00pm - 7:00pm |
Fee: Rs.25,000/- Rs.15,000/- Inclusive of all taxes |
Enroll Now | |
| Course: SOC Analyst Fundamental | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekday batches) | Reg. Date: 11th March 2026 | Class Start: 13th March 2026 | Class End: 29th May 2026 | Day & Time: Wednesday & Friday 5:00pm - 7:00pm |
Fee: Rs.29,000/- Rs.19,000/- Inclusive of all taxes |
Enroll Now | |
| Course: Linux 8.0 (RHCSA & RHCE) | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekday batches) | Reg. Date: 7th March 2026 | Class Start: 9th March 2026 | Class End: 18th May 2026 | Day & Time: Monday & Wednesday 12:00pm - 2:00pm |
Fee: Rs.24,500/- Rs.14,500/- Inclusive of all taxes |
Enroll Now | |
| Course: CCNA Essential | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 6th March 2026 | Class Start: 8th March 2026 | Class End: 17th May 2026 | Day & Time: Sunday 10:00am - 2:00pm |
Fee: Rs.23,000/- Rs.13,000/- Inclusive of all taxes |
Enroll Now | |
| Reg. Date: 3rd April 2026 | Class Start: 5th April 2026 | Class End: 14th June 2026 | Day & Time: Sunday 3:00pm - 7:00pm |
||||
| Course: Core Python Programming | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 5th March 2026 | Class Start: 7th March 2026 | Class End: 16th May 2026 | Day & Time: Saturday 3:00pm - 7:00pm |
Fee: Rs.18,750/- Rs.8,750/- Inclusive of all taxes |
Enroll Now | |
| Reg. Date: 2nd April 2026 | Class Start: 4th April 2026 | Class End: 13th June 2026 | Day & Time: Saturday 10:00am - 2:00pm |
||||
| Course: Web Application Penetration Testing Level I | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 9th April 2026 | Class Start: 11th April 2026 | Class End: 20th June 2026 | Day & Time: Saturday 10:00am - 2:00pm |
Fee: Rs.24,750/- Rs.14,750/- Inclusive of all taxes |
Enroll Now | |
| Course: Web Application Penetration Testing Level II | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekday batches) | Reg. Date: 9th March 2026 | Class Start: 11th March 2026 | Class End: 22nd May 2026 | Day & Time: Wednesday & Friday 3:00pm - 5:00pm |
Fee: Rs.24,750/- Rs.14,750/- Inclusive of all taxes |
Enroll Now | |
| Course: Network Penetration Testing Level I | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 3rd April 2026 | Class Start: 5th April 2026 | Class End: 14th June 2026 | Day & Time: Sunday 10:00am - 2:00pm |
Fee: Rs.24,750/- Rs.14,750/- Inclusive of all taxes |
Enroll Now | |
| Course: Network Penetration Testing Level II | |||||||
| Batch: Offline/Online Interactive and Classroom Training with dedicated Faculty (Weekend batches) | Reg. Date: 5th March 2026 | Class Start: 7th March 2026 | Class End: 16th May 2026 | Day & Time: Saturday 3:00pm - 7:00pm |
Fee: Rs.24,750/- Rs.14,750/- Inclusive of all taxes |
Enroll Now |