Computer forensics (also known as computer forensic science) is a special stream of digital forensic science relating to evidence found in computers and digital storage media. The intention of computer forensics is to check the digital media in a forensically sound manner for identifying, preserving, recovering, analyzing and presenting facts and opinions about digital data.
Why become a Computer Forensic expert?
Comparative Ability
to study related data from different sources
Trending Ability
for related data
Duration
40 hours - 2 classes per week
Eligibility
The prerequisite of the course is 10+2 and a basic knowledge of computer & internet.
Course Fees
Class Room Training
Rs.15,000/-
Inclusive of all taxes
Online Training
Rs.25,000/-
Rs.15,000/-
Inclusive of all taxes
What You Will Get?
40 Hours
in-depth training by best faculties from cyber security industry
Study Materials
Computer Forensic
Certificate of Completion after examination and alumni status
Course Benefits:
- Risk identification
- Ability to identify industry trends
Your Course Path
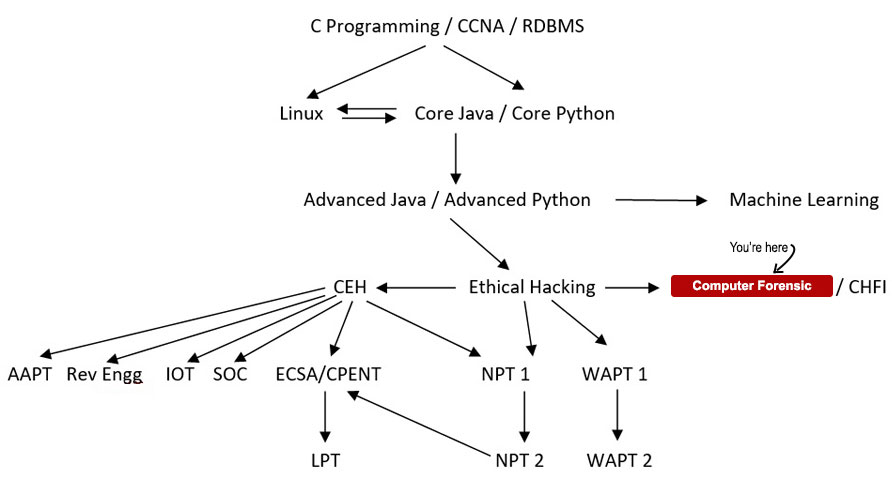
Course Details
- The duration of the course is 40 hours at 2 classes per week
- The course fee is Rs.15,000/- (Classroom Training) & Rs.25,000/- Rs.15,000/- (Online Training)
- The course is conducted on both theory and practical basis with a little more emphasis on practical sessions.
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensic - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
Scope of computer forensics in India is on an all time rise. Most corporate now-a-days are in urgent need for cyber security and cyber forensics experts to combat cyber crimes and safeguard their confidential data. Some of the designations of a computer forensic expert are Computer Forensics Investigator, Computer Forensics Analyst, Computer Forensics Technician, Computer Forensics Specialist, Digital Forensic Specialist, etc. Computer forensics professionals are also needed majorly at the Central Forensic Science Laboratories all over India.
The computer forensic science jobs which belong to the government sector pay according to the structure and pay scale. In private sector, a qualified computer forensic science expert starts with Rs. 3 Lac to Rs. 4 Lac per annum which can rise up to 6 to 8 Lac later.
FAQs
The syllabus includes introduction to Computer Forensics, Volatile Data, Live Slide Collections, Volatile Data Collections using APIs, Bootable Side Collections, Remote Investigation and Collection, MS Windows System Analysis, Linux File System, Password Breaking, Network Forensics, Investigating Steganography, Cyber Crime and Law and Tool based Forensic Training.
The duration of the course is 40 hours at 2 classes per week.
The course is conducted on both theory and practical basis with a little more emphasis on practical sessions.
The duration of the course is 40 hours at 2 classes per week.
Scope of computer forensics in India is on an all time rise. Most corporate now-a-days are in urgent need for cyber security and cyber forensics experts to combat cyber crimes and safeguard their confidential data. Some of the designations of a computer forensic expert are Computer Forensics Investigator, Computer Forensics Analyst, Computer Forensics Technician, Computer Forensics Specialist, Digital Forensics Specialist, etc. Computer forensics professionals are also needed majorly at the Central Forensic Science Laboratories all over India.
Advanced Network Forensics: Threat Hunting, Analysis and Incident Response, is the name and code of the course and examination which can be studied after this course.
Course Fees
Rs.15,000/-
Inclusive of all taxes
Batches
Weekend Batches for Kolkata Center:
Mar, 2026
Mar, 2026
May, 2026
Weekday Batches for Siliguri Center:
Mar, 2026
Mar, 2026
May, 2026
Member of: