Penetration testing is the practice of testing a computer system, network or web application to find vulnerabilities that an attacker could exploit. The task of a web security tester or penetration tester is to audit the security of the web applications, web services and web servers in a company. Though it might seem to be a very glamorous job in the cyber security field, but let us break the myth. One of the challenges of this profession is fighting "boredom". You have to deal with the same tools, techniques, procedures over and over again. Often, you will get the same findings. But, if you are passionate enough it will become a hobby. The satisfaction you'll feel after finding critical vulnerabilities is unparalleled.
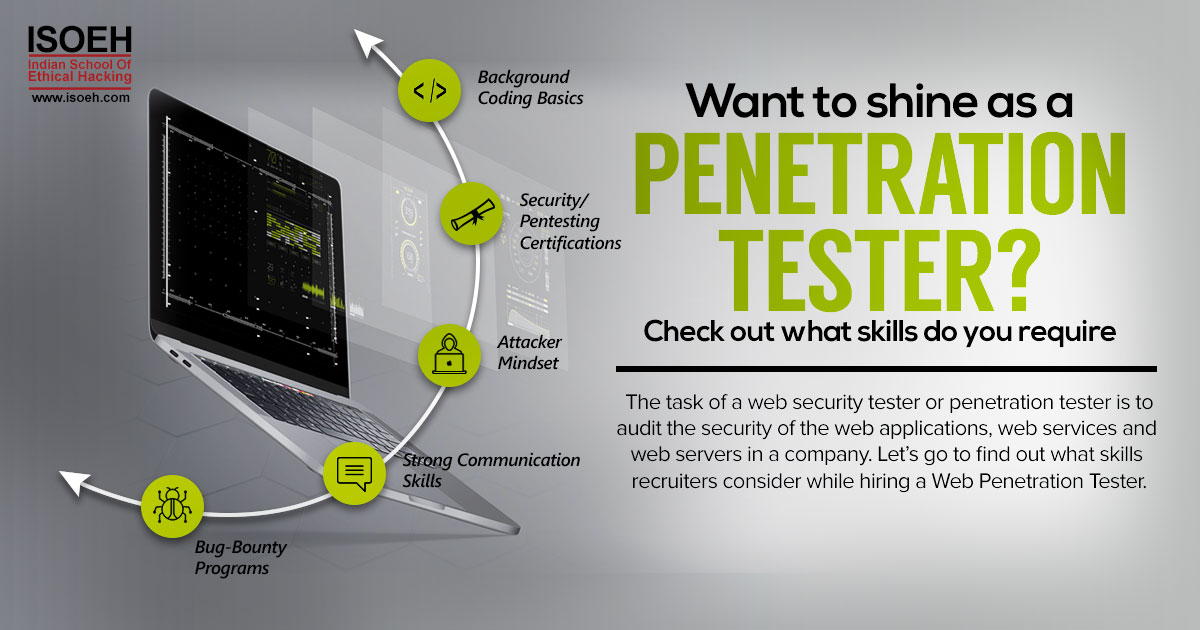
If you still feel hooked, let's go to find out what skills recruiters consider while hiring a Web Penetration Tester.
Today's attackers are very smart and innovative and not held back by anything. Hiring for Pentesting involves giving professional pentesters the permission to test and verify that new and existing systems, networks, applications and safeguards don't provide unauthorized access to malicious hackers. For that, hiring sharp, practical, trustworthy and innovative professionals is quite a task.
1. Decent Development Background Coding Basics
Of course, a mere script kiddie won't be hired who shoots out his licensed web application vulnerability scanners like firing a cannon or laser. People often start out by working as system administrators or programmers and become so knowledgeable about how their systems work that finding flaws becomes easy for them. The more you know about the systems, security, and penetration testing aspects will come naturally to you. Companies often prefer to train a developer to become a pen tester. It is easier for developers to adapt to testing as they have a good understanding of computing operating systems- Windows, Linux and network technologies.
2. Security/Pentesting Certifications
Though you necessarily do not need a formal technical degree but it becomes difficult to prove your expertise without any degree or experience. Having security related certificates like OSCP, CEH, ECSA will get you more interviews and will result in a higher salary level. Certifications show someone is willing to invest time to learn concepts and build his foundations. Good penetration testers also have a strong foundation in networking, OS, and programming so technical certifications related to these areas will be beneficial and will vary based on the specific company. Also, look for companies who are offering internship. It will add some value to your resume because there are very few companies who are willing to hire pentesters without experience.
3. Attacker Mindset
Hiring consultants who are not passionate about their area of expertise will lead to disasters. A hacker mindset is needed to be motivated and inquisitive in nature to explore new possibilities. Having good technical skills are added benefits if someone has the ability to think out of the box. A good penetration tester must think like a bad guy; how an attacker would try to get into a system. A hacker is someone who innovates and does things out of curiosity. It is always better to hire someone who is always hungry for knowledge and willing to learn than a person who has many security certifications and has a lot of experience in the information security field but have not applied what they have learned from the training.
4. Strong Communication Skills
Good penetration testers are a little creative and come up with new ways of testing security that the company may not have thought up. Show your creative side, and if you have experience, explain how you've used that to solve security problems in the past. "The most valuable skill a penetration tester can have, in my opinion, is the ability to easily switch from deep, technical discussions to high-level concepts depending on the audience", said Ronnie Flathers, associate security consultant at Neohapsis. We need to understand that Penetration testing results are only useful if they are acted upon, and clear communication, both written and spoken, is one of the most critical skills that a tester can have. Pentesters should be able to produce quality reports and explain their findings in detail in the simplest terms so that any non-technical person can understand that.
5. Participation in Bug-Bounty Programs
For those unaware of, Bug Bounty is a program initiated by companies that reward hackers if ever they found a security flaw in their applications and then have reported it through responsible disclosure. Bug bounty programs allow skilled hackers to hack into their systems as long as any security holes are reported to the company before disclosing them publicly. If a candidate has participated in such programs and is a passionate bug bounty hunter then he/she must have encountered and reported unusual bugs aside from SQL Injection, Cross-Site Scripting, RCE, etc. (the usual ones) which are usually duplicated. This is a good thing because he or she can find some good flaws in your company. Bug Bounties and Disclosures indicate research-oriented bent of mind showing the candidate as an exceptional researcher and learner.
It is good to hire exploit developers, vulnerability researchers and bug hunters who have publicly disclosed their security findings on open source software and enterprise products especially if their bugs landed a CVE (Common Vulnerabilities and Exposures) ID or OSVD (Open Source Vulnerability Database) ID. Most of these kinds of applicants are also skilled reverse engineers and static source code auditors so yeah you shouldn't have some problem with them unless if they are lazy. A Penetration Tester earns an average salary of Rs 412,802 per year in India. A skill in Security Testing and Auditing is associated with high pay for this job.
Enroll for Web Application Penetration Testing course »Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details