CompTIA Security+ is a global certification that validates the baseline skills necessary to perform core security functions and pursue an IT security career.
Covering risk management, incident response, security controls and more.
CompTIA Security+ Opens the Door to Your Cybersecurity Career!
Chosen by more corporations and defense organizations
than any other certification on the market to validate baseline security skills and for fulfilling the DoD 8570 compliance.
Get hands-on cybersecurity experience.
The only foundational cybersecurity certification emphasizing hands-on practical skills.
CompTIA Security+ ensures the
security professional is better prepared to problem solve
a wider variety of today’s complex issues.
Learn the latest trends and techniques.
Gain core cybersecurity knowledge applicable across more of today’s job roles
to secure systems, software and hardware.
About the exam
CompTIA Security+ is the first cybersecurity certification a candidate should earn. It establishes the core knowledge required in the field and provides a springboard to intermediate-level cybersecurity jobs. Security+ incorporates best practices in hands-on troubleshooting, ensuring you have the practical security problem-solving skills required to:
- Assess the security of an organization and recommend and implement appropriate solutions
- Monitor and secure hybrid environments, including cloud, mobile and IoT
- Operate with an awareness of applicable laws and policies, including principles of governance, risk and compliance
- Identify, analyze and respond to security events and incidents
CompTIA Security+ is compliant with ISO 17024 standards and approved by the U.S. DoD to meet directive 8140/8570.01-M requirements. Regulators and government rely on ANSI accreditation because it provides confidence and trust in the outputs of an accredited program. Over 2.3 million CompTIA ISO/ANSI-accredited exams have been delivered since January 1, 2011.
CompTIA Security+ validates certified professionals have the skills required to be more proactive in preventing the next attack.
Duration
42 hours - 2 classes per week
Eligibility
- CompTIA Network+ and two years of experience in IT administration with a security focus
- CompTIA Network+ and two years of experience working in a security/ systems administrator job role
Course Fees
Class Room Training
Rs.37,500/-
+ 18% GST
Online Training
Rs.47,500/-Rs.37,500/-
+ 18% GST
What You Will Get?
42 Hours
in-depth training by best faculties from cyber security industry
Study Materials
and examination voucher
CompTIA Security+ Certificate
of completion after examination and alumni status
Course Benefits:
What Skills Will You Learn?
Attacks, Threats and Vulnerabilities
More threats, attacks and vulnerabilities from newer custom devices that must be mitigated, such as IoT and embedded devices, newer DDoS attacks and social engineering attacks based on current events.
Architecture and Design
Enterprise environments and reliance on the cloud, which is growing quickly as organizations transition to hybrid networks.
Implementation
Administering identity, access management, PKI, basic cryptography, wireless and end-to-end security.
Operations and Incident Response
Organizational security assessment and incident response procedures, such as basic threat detection, risk mitigation techniques, security controls and basic digital forensics.
Governance, Risk and Compliance
Organizational risk management and compliance with regulations, such as PCI-DSS, SOX, HIPAA, GDPR, FISMA, NIST and CCPA.
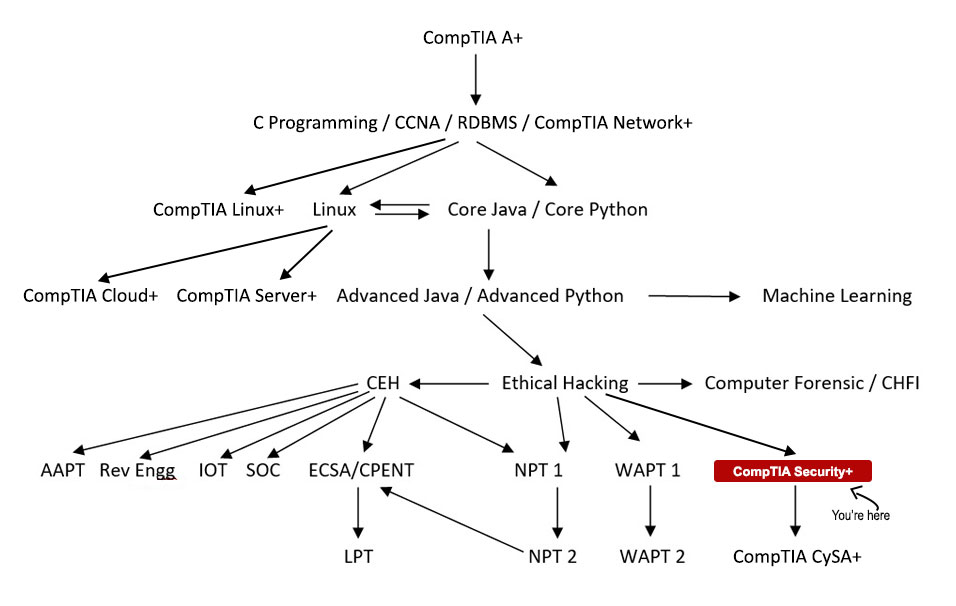
Your Course Path
Course Details
- Exam Code: SY0-701
- Launch Date: November 7, 2023
- Exam Description: The CompTIA Security+ certification exam will verify the successful candidate has the knowledge and skills required to assess the security posture of an enterprise environment and recommend and implement appropriate security solutions; monitor and secure hybrid environments, including cloud, mobile, and IoT; operate with an awareness of applicable laws and policies, including principles of governance, risk, and compliance; identify, analyze, and respond to security events and incidents.
- Number of Questions: Maximum of 90 questions
- Type of Questions: Multiple choice and performance-based.
- Length of Test: 90 Minutes
- Passing Score: 750 (on a scale of 100-900)
- Recommended Experience: CompTIA Network+ and two years of experience working in a security/ systems administrator job role.
- Retirement: TBD – Usually three years after launch
- Testing Provider: Pearson VUE
- Topic 1A: Compare and Contrast Information Security Roles (Day 1)
- Topic 1B: Compare and Contrast Security Control and Framework Types (Day 1)
- Topic 2A: Explain Threat Actor Types and Attack Vectors (Day 2)
- Topic 2B: Explain Threat Intelligence Sources (Day 2)
- Topic 3A: Assess Organizational Security with Network Reconnaissance Tools (Day 3)
- Topic 3B: Explain Security Concerns with General Vulnerability Types (Day 3)
- Topic 3C: Summarize Vulnerability Scanning Techniques (Day 3)
- Topic 3D: Explain Penetration Testing Concepts (Day 3)
- Topic 4A: Compare and Contrast Social Engineering Techniques (Day 4)
- Topic 4B: Analyze Indicators of Malware-Based Attacks (Day 4)
- Topic 5A: Compare and Contrast Cryptographic Ciphers (Day 5)
- Topic 5B: Summarize Cryptographic Modes of Operation (Day 5)
- Topic 5C: Summarize Cryptographic Use Cases and Weaknesses (Day 5)
- Topic 5D: Summarize Other Cryptographic Technologies (Day 5)
- Topic 6A: Implement Certificates and Certificate Authorities (Day 6)
- Topic 6B: Implement PKI Management (Day 6)
- Topic 7A: Summarize Authentication Design Concepts (Day 7)
- Topic 7B: Implement Knowledge-Based Authentication (Day 7)
- Topic 7C: Implement Authentication Technologies (Day 7)
- Topic 7D: Summarize Biometrics Authentication Concepts (Day 7)
- Topic 8A: Implement Identity and Account Types (Day 8)
- Topic 8B: Implement Account Policies (Day 8)
- Topic 8C: Implement Authorization Solutions (Day 8)
- Topic 8D: Explain the Importance of Personnel Policies (Day 8)
- Topic 9A: Implement Secure Network Designs (Day 9)
- Topic 9B: Implement Secure Switching and Routing (Day 9)
- Topic 9C: Implement Secure Wireless Infrastructure (Day 9)
- Topic 9D: Implement Load Balancers (Day 9)
- Topic 10A: Implement Firewalls and Proxy Servers (Day 10)
- Topic 10B: Implement Network Security Monitoring (Day 10)
- Topic 10C: Summarize the Use of SIEM (Day 10)
- Topic 11A: Implement Secure Network Operations Protocols (Day 11)
- Topic 11B: Implement Secure Application Protocols (Day 11)
- Topic 11C: Implement Secure Remote Access Protocols (Day 11)
- Topic 12A: Implement Secure Firmware (Day 12)
- Topic 12B: Implement Endpoint Security (Day 12)
- Topic 12C: Explain Embedded System Security Implications (Day 12)
- Topic 13A: Implement Mobile Device Management (Day 13)
- Topic 13B: Implement Secure Mobile Device Connections (Day 13)
- Topic 14A: Analyze Indicators of Application Attacks (Day 14)
- Topic 14B: Analyze Indicators of Web Application Attacks (Day 14)
- Topic 14C: Summarize Secure Coding Practices (Day 14)
- Topic 14D: Implement Secure Script Environments (Day 14)
- Topic 14E: Summarize Deployment and Automation Concepts (Day 14)
- Topic 15A: Summarize Secure Cloud and Virtualization Services (Day 15)
- Topic 15B: Apply Cloud Security Solutions (Day 15)
- Topic 15C: Summarize Infrastructure as Code Concepts (Day 15)
- Topic 16A: Explain Privacy and Data Sensitivity Concepts (Day 16)
- Topic 16B: Explain Privacy and Data Protection Controls (Day 16)
- Topic 17A: Summarize Incident Response Procedures (Day 17)
- Topic 17B: Utilize Appropriate Data Sources for Incident Response (Day 17)
- Topic 17C: Apply Mitigation Controls (Day 17)
- Topic 18A: Explain Key Aspects of Digital Forensics Documentation Acquisition (Day 18)
- Topic 18B: Explain Key Aspects of Digital Forensics Evidence Acquisition (Day 18)
- Topic 19A: Explain Risk Management Processes and Concepts (Day 19)
- Topic 19B: Explain Business Impact Analysis Concepts (Day 19)
- Topic 20A: Implement Redundancy Strategies (Day 20)
- Topic 20B: Implement Backup Strategies (Day 20)
- Topic 20C: Implement Cybersecurity Resiliency Strategies (Day 20)
- Topic 21B: Explain the Importance of Physical Host (Day 21)
- Security Controls (Day 21)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensic - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Job Prospects & Job Sources
Jobs You Can Land With CompTIA Security+:
| Business Analyst | Cybersecurity Manager | Software Developer |
| Systems Administrator | MSP Personnel | Security Consultant |
The average salary of CompTIA Security+ in India is Rs 7 lakhs per annually.
FAQs
- Comparing Security Roles and Security Controls
- Explaining Threat Actors and Threat Intelligence
- Performing Security Assessments
- Identifying Social Engineering and Malware
- Summarizing Basic Cryptographic Concepts
- Implementing Public Key Infrastructure
- Implementing Authentication Controls
- Implementing Identity and Account Management Controls
- Implementing Secure Network Designs
- Implementing Network Security Appliances
- Implementing Secure Network Protocols
- Implementing Host Security Solutions
- Implementing Secure Mobile Solutions
- Summarizing Secure Application Concepts
- Implementing Secure Cloud Solutions
- Explaining Data Privacy and Protection Conce
- Performing Incident Response
- Explaining Digital Forensics
- Summarizing Risk Management Concepts
- Implementing Cybersecurity Resilience and Explaining Physical Security
42 hours
CompTIA Network+ and two years of experience in IT administration with a security focus.
CompTIA Network+ and two years of experience working in a security/ systems administrator job role.
CompTIA SECURITY+ gives you an in-depth understanding of security concepts. From here, you can choose either the offensive or defensive part. You can get an entry-level cybersecurity job.
After SECURITY+, you can upgrade yourself by CySA+ and CPENT or PENTEST+.
Member of: