Contents
Introduction
In the digital age, cybersecurity is more crucial than ever to protect our sensitive information from cybercriminals and other malicious actors. Hackers never rest, which is why implementing robust cybersecurity practices is essential to safeguarding your business from cyber-attacks.
We have already discussed how the cloud become an on-demand approach in the present day.
What is Cloud Security?
Cloud security refers to the set of policies, technologies, and practices that are designed to protect the confidentiality, integrity, and availability of data and applications that are hosted in the cloud.
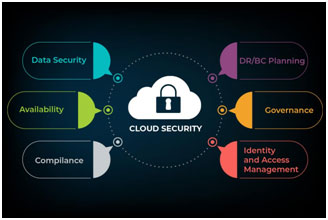 It is critical because cloud computing often involves storing sensitive data and running business-critical applications in a shared infrastructure environment that is accessible over the Internet.
It is critical because cloud computing often involves storing sensitive data and running business-critical applications in a shared infrastructure environment that is accessible over the Internet.
It includes a range of security controls and mechanisms that are implemented to protect cloud-based resources from unauthorized access, data breaches, and other security threats. These may include measures such as encryption, access control, authentication, monitoring, auditing, and disaster recovery.
Effective cloud security requires a shared responsibility model between the cloud service provider and the customer, with each party responsible for implementing appropriate security measures to protect their respective areas of responsibility.
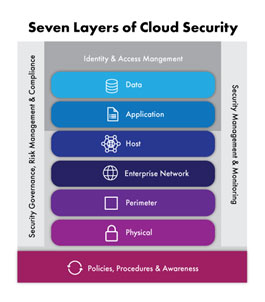
Cloud Security Fundamentals:
This section would cover the basics of cloud security, including what the cloud is and how it works, the types of cloud models available (public, private, hybrid), and common cloud security threats and risks.
Cloud Security Best Practices:
This section would focus on the best practices for securing data and applications in the cloud, including how to properly configure cloud environments, implementing strong access controls, and deploying encryption and other security measures to protect against data breaches.
Cloud Compliance and Regulations:
This chapter would cover the various compliance and regulatory requirements that organizations must adhere to when operating in the cloud, including GDPR, HIPAA, and PCI DSS.
Cloud Security Tools and Technologies:
This section would focus on the various security tools and technologies that can be used to secure cloud environments, including intrusion detection and prevention systems, firewalls, security information and event management (SIEM) systems, and vulnerability scanning tools.
Cloud Incident Response and Disaster Recovery:
This section would cover the steps organizations can take to prepare for and respond to security incidents and disasters in the cloud, including developing incident response plans, conducting regular backups and disaster recovery drills, and implementing business continuity strategies to ensure that critical systems and applications remain available in the event of an outage.
Why You Should Pursue a Career in Cloud Security?
Building a career in cloud security can be a wise decision for several reasons:
 High Demand: With the increasing adoption of cloud computing by businesses, the demand for cloud security professionals is also on the rise. According to various job portals, the demand for cloud security experts is growing at a rate of 37% annually, and this trend is expected to continue in the coming years.
High Demand: With the increasing adoption of cloud computing by businesses, the demand for cloud security professionals is also on the rise. According to various job portals, the demand for cloud security experts is growing at a rate of 37% annually, and this trend is expected to continue in the coming years.- Lucrative Salaries: Due to the high demand for cloud security professionals, organizations are willing to offer competitive salaries to attract and retain top talent. As per the salary data on various job portals, cloud security professionals earn more than the average cybersecurity professional.
- Career Growth: As organizations continue to move their operations to the cloud, the need for cloud security professionals will continue to grow. Therefore, building a career in this field can provide you with long-term career growth opportunities.
- Variety of Roles: The field of cloud security offers a wide range of roles such as cloud security architect, cloud security engineer, cloud security analyst, cloud security consultant, etc. You can choose a role that aligns with your skills and interests.
- Continuous Learning: The field of cloud security is constantly evolving, and there is always something new to learn. Therefore, if you enjoy learning new things and staying updated with the latest technology trends, then building a career in cloud security can be a great choice for you.
What Are We Offering to Cloud Security Aspirants?
Protect your organization's cloud environment like a pro with AWS (Cloud Architecture) certification. Grab now!
Dreaming to become an AWS cloud architecture expert? Book our comprehensive AWS course now!
 This program is designed to equip you with the knowledge and skills necessary to excel in the world of cloud computing. Learn from experienced professionals and gain hands-on experience working with AWS tools and technologies. Internship opportunities are available with 100% placement assistance.
This program is designed to equip you with the knowledge and skills necessary to excel in the world of cloud computing. Learn from experienced professionals and gain hands-on experience working with AWS tools and technologies. Internship opportunities are available with 100% placement assistance.
The Corporate expert-designed course covers everything from cloud infrastructure design to deployment and management, including security and compliance best practices.
Upon completion of the course, you'll be ready to earn your AWS certification and take your career to new heights.
Don't wait to become an AWS cloud architecture expert. Enroll now and take the first step towards your dream career!
What are Your Benefits?
 AWS enables businesses to build a number of sophisticated applications. Organizations of every industry and of every size can run every imaginable use case on AWS. The most common applications of AWS are:
AWS enables businesses to build a number of sophisticated applications. Organizations of every industry and of every size can run every imaginable use case on AWS. The most common applications of AWS are:
- Storage and Backup
- Websites
- Gaming
- Mobile, Web, and Social Applications
- Look at our structured syllabus here
Conclusion
The AWS Cloud Architecture course is a game-changer in the world of technology. With its comprehensive curriculum and hands-on approach, it equips individuals with the skills needed to design and manage scalable, reliable, and cost-effective cloud solutions using AWS services.
The course offers numerous benefits such as increased job opportunities, competitive salaries, and the ability to work on cutting-edge technologies. This course is an investment in your future, and the benefits are immense.
So, don't hesitate to enroll in the course today and take the first step towards an exciting and rewarding career in cloud computing.
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details