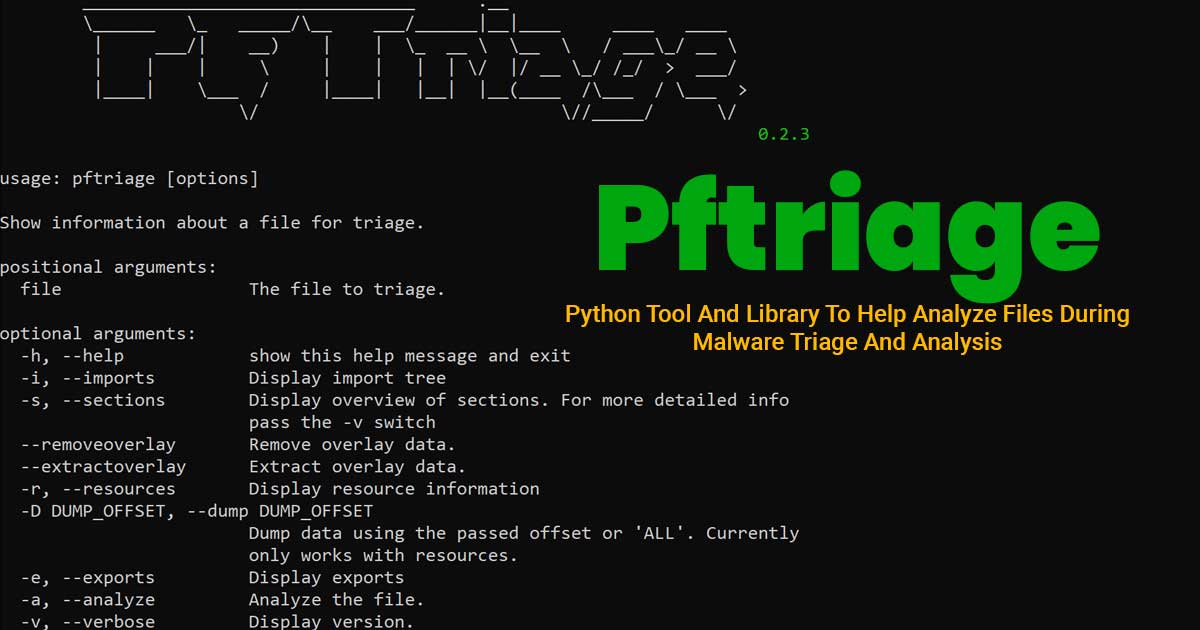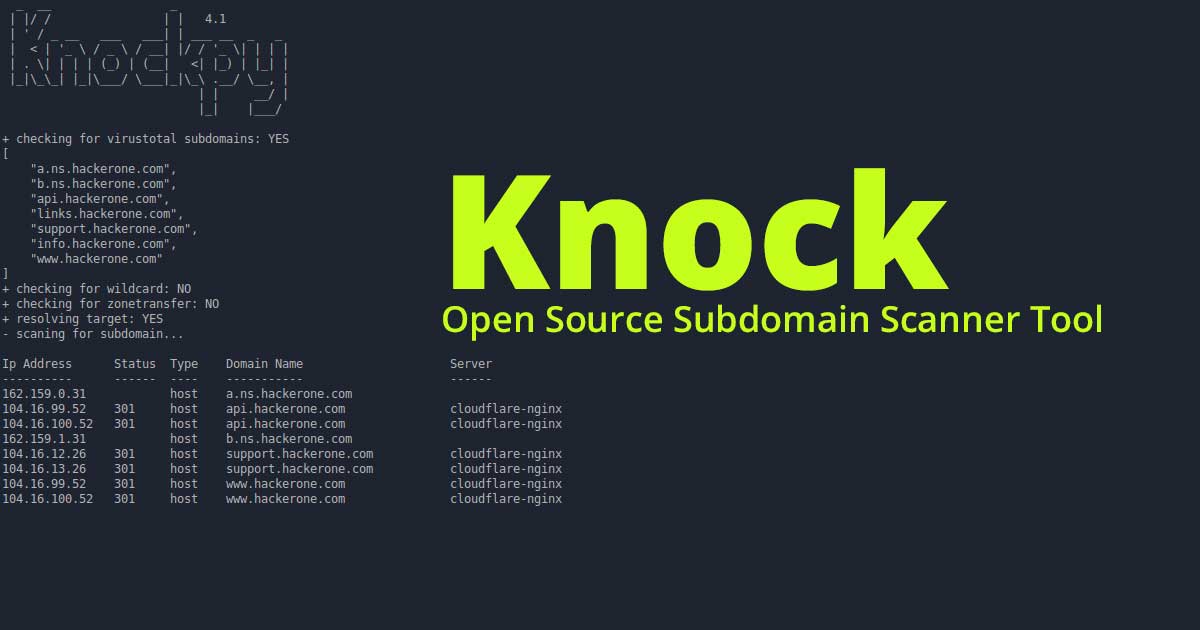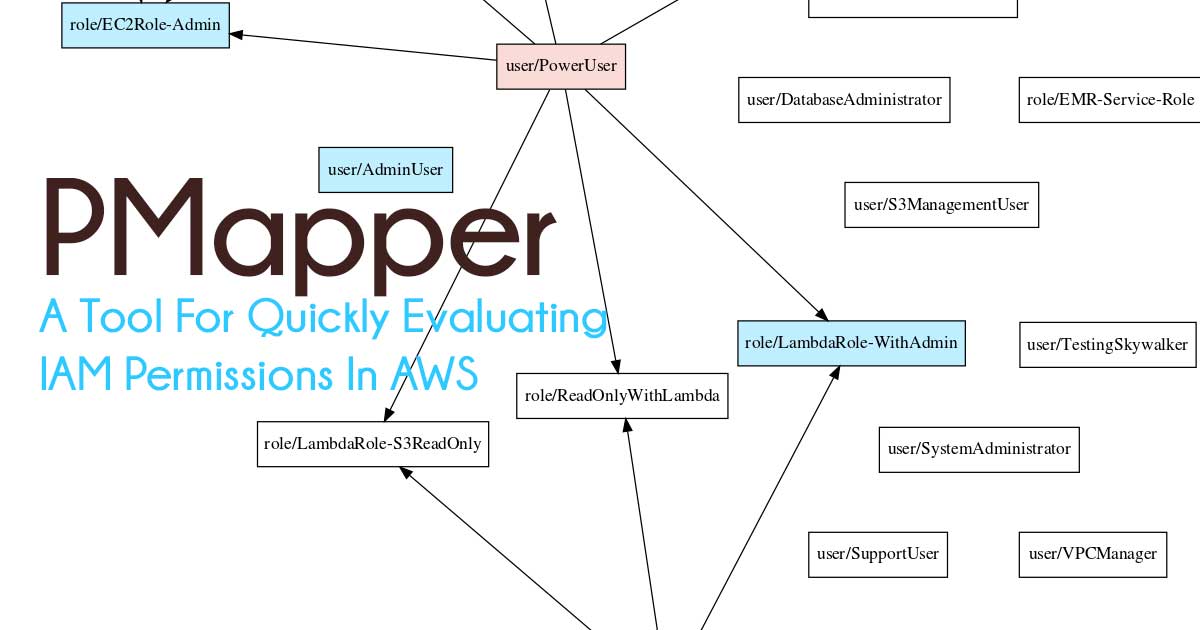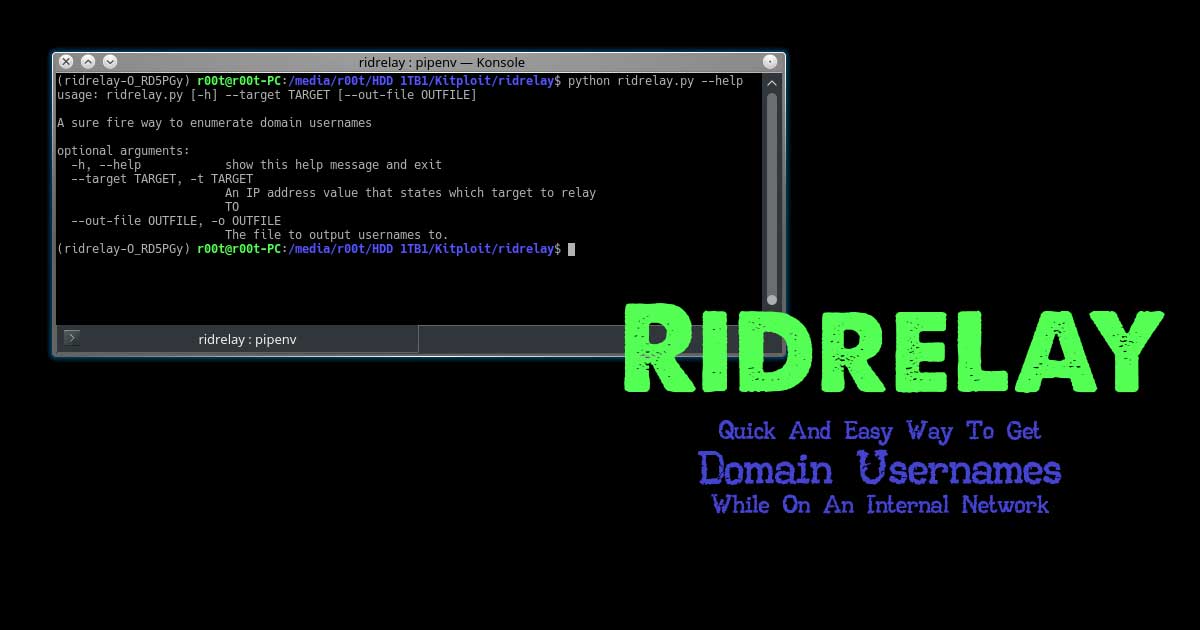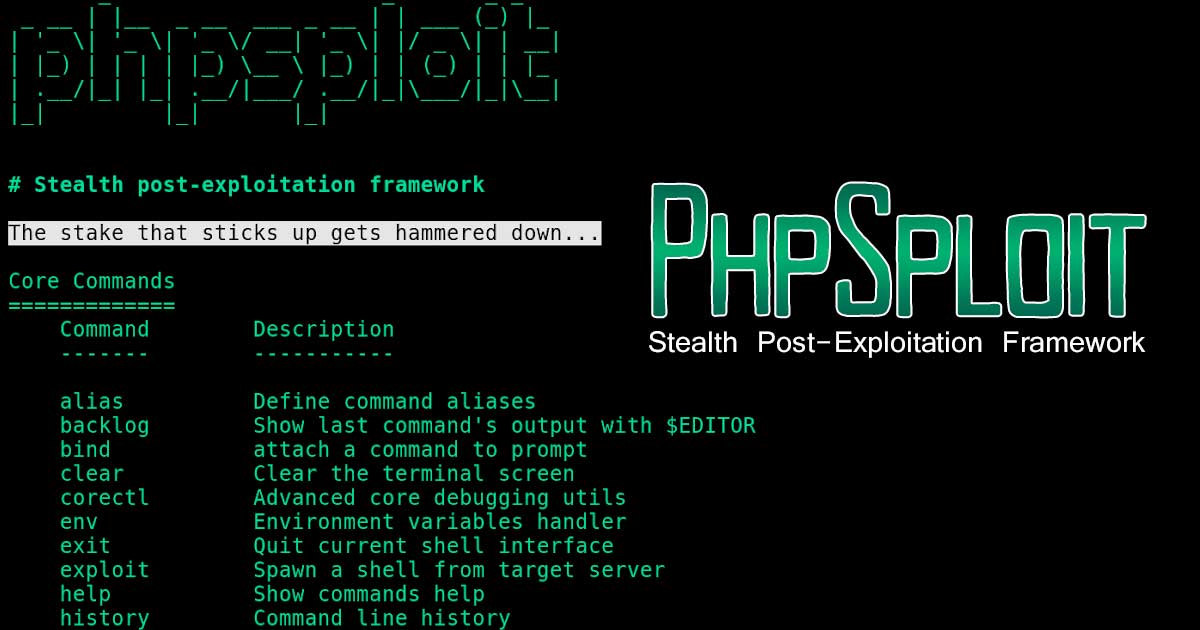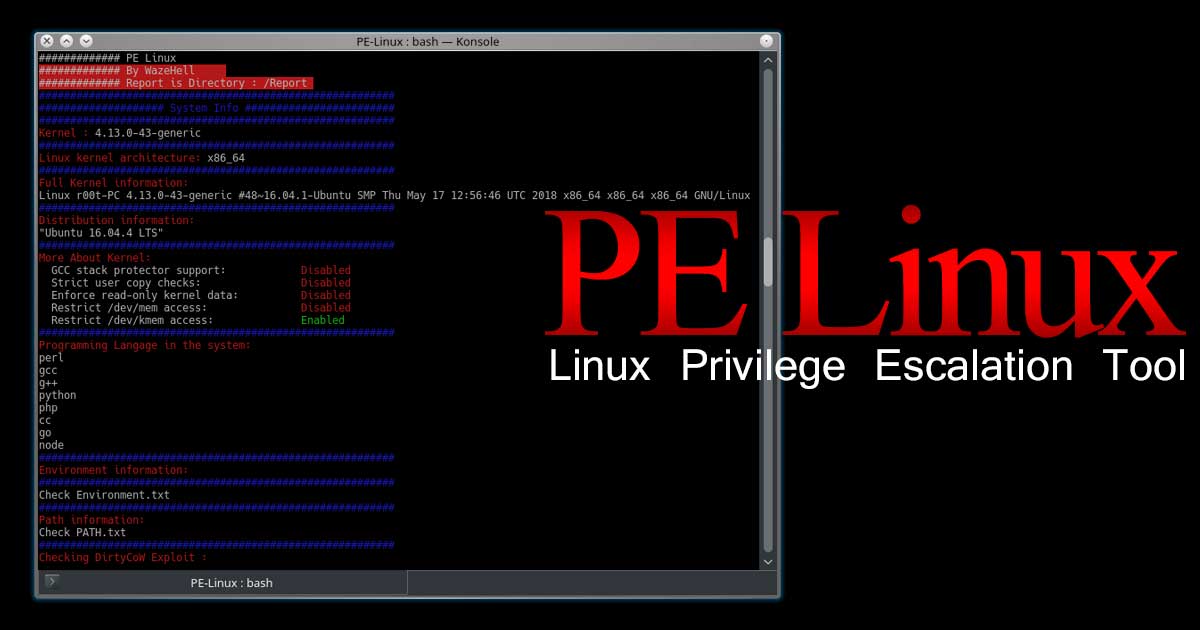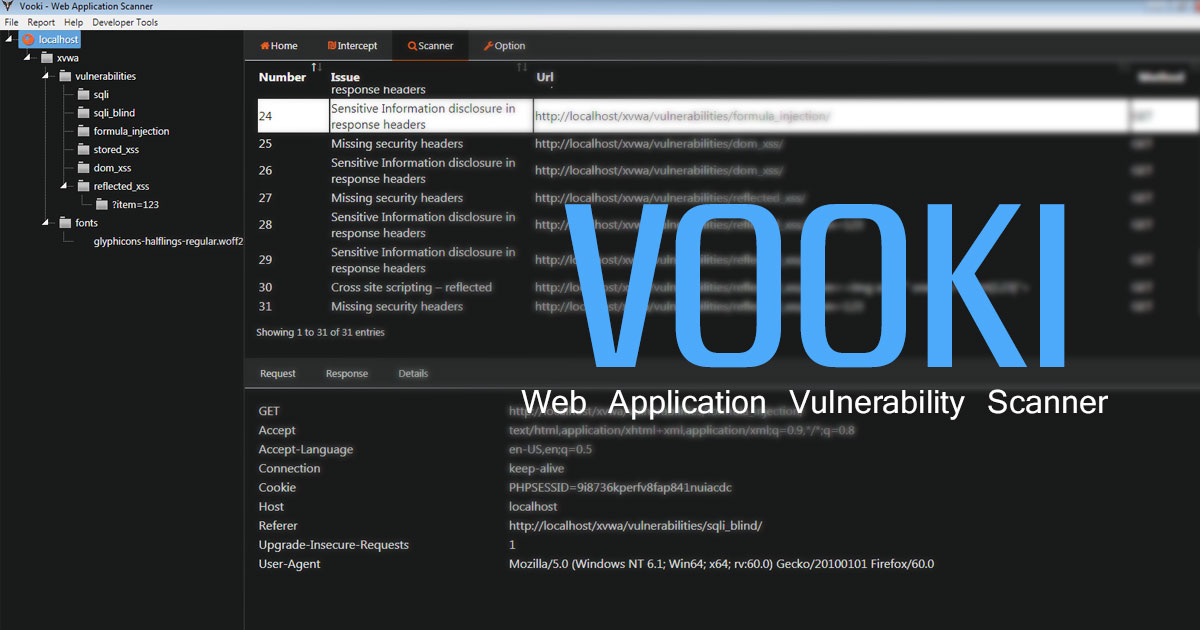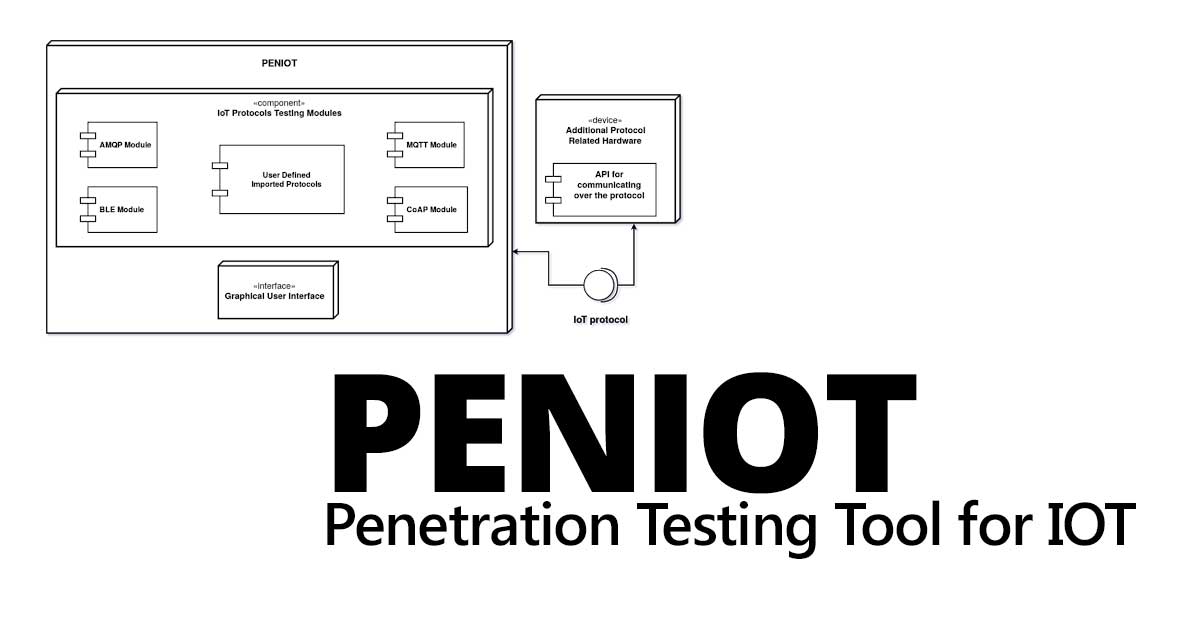
PENIOT is a penetration testing tool for internet of things (IOT) devices. It helps you to penetrate your devices by targeting their internet connectivity with different types of security attacks. In other words you can expose your devices to both active and passive security attacks. After deciding the target information of that device you can perform active security attacks like consuming system resources, replaying valid communication units and so on. One of the most important features Of PENIOT Is being extensible. By default, it has several common IOT protocols and numerous security attacks related to those protocols. But it can be extended further via exporting the basic structure of internally used components so that you can develop your attacks in harmony with the internal structure of the PENIOT.
Why is it required?
The IOT paradigm has experienced immense growth in the past decade, with billions of devices connected to the internet. Most of the devices lack even basic security measures due to their capacity constraints and made designs without security in mind due to the shortness of the time in the market. Due to the high connectivity in IOT, attacks that have devastating effects in extended networks can be easily launched by hackers through vulnerable devices. The main aim of PENIOT is to accelerate the process of security testing. It enables you to figure out security flaws on your IOT devices by automating the time of consuming penetration phase.
What does this tool provides?
Since the number of IOT devices is increasing rapidly, IOT has become a more common tool in our daily life. Smart homes, smart bicycles, smart locks all are the example of IOT products. We need to choose some of the most commonly used IOT protocols to plant into PENIOT default. It is one of the first examples of penetration testing tools on IOT fields. There are only one or two similar tools which are specialized on IOT but they are still in the development phase. These IOT protocols are tested with various types of security attacks such as DoS, sniffing, and replay attacks.
Following protocols are currently supported:
- Advanced Message Queuing Protocol
- Bluetooth Low Energy
- Constraint Application Tool
Installation:
First you need to have the Python setup tools module installed in your machine. Also you need to install Python-tk and bluepy before installation and build.
In short you need the following before running the installation script.
- Setup tools.
- Python-tk.
- Bluepy.
You can build project in your local by executing the following codes:
$ git clone [email protected]: yazuka8
$ cd Peniot
$ python setup . py install
Download the tool here: https://github.com/yakuza8/peniot
For more popular tools click here: https://www.isoeh.com/tools.html
Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details