Hacking an Android APK file involves that we decompile, hack it, and recompile, essentially reverse engineering an apk file. Very few people actually explore the possibility of android hacking. Here's a brief overview on this-
APK format
Apps in Android have an extension of .apk format - which is basically a special .zip container that is signed with a certificate. The signer could be somebody like Google Apps Store. The idea is that modifying the .apk file means the signature is invalidated, to prevent installation of modified apps.
Modifications
Modifying an APK file is somewhat difficult, depending on the quality of the app. The Dalvik (Android's virtual machine), prevents code obfuscation – which is the deliberate act of creating hard to understand code. Since the Dalvik supports reflection, and the virtual machine has to be able to interpret the byte code, no obfuscation can ever hope to compete.
Reflection is the ability of a computer program to examine and modify the structure and behavior – specifically the values, meta-data, properties and functions of an object at runtime. Obfuscation products like ProGuard may become more advanced with time but intense obfuscation will likely have a very negative impact on performance.
ProGuard is a free Java class file shrinker, optimizer, obfuscator, and preverifier. It detects and removes unused classes, fields, methods, and attributes. It optimizes bytecode and removes unused instructions. It renames the remaining classes, fields, and methods using short meaningless names. Finally, it pre verifies the processed code for Java 6 or for Java Micro Edition.
Suppose an APK file is present, we want to decompile it into something like assembly language. We can do that using the APK Tool, which turns decompiles it into a folder with small files.
Then we dig through the small code and make change to get our desired results.
We recompile the small file into APK file, install and test it on the emulator and then convert it back to ap form.
Tools required
- Eclipse, to code your own apps
http://www.eclipse.org/downloads/ - Java SDK
http://www.oracle.com/technetwork/java/javase/downloads/index.html - Android SDK, for the Android emulator
http://developer.android.com/sdk/index.html - APK Tool, to reverse engineer APK files and create smali files
http://code.google.com/p/android-apktool/ - Notepad++, a great program that has syntax highlighting addon pack for small observations and inspections
http://notepad-plus-plus.org/ - Amon_RA's Testsign tool, for signing the recompiled APK file
https://sites.google.com/site/chall32/general/testsign.jar
Usage
To run the Android emulator, use their Android Virtual Devices Manager. Make a choice in what you want your device to be; just keep in mind the higher the resolution the slower it’ll be. Expect the emulator to run with heavy lag.
In this terminal, there are some commands you want to be familiar with.
Command
Effect
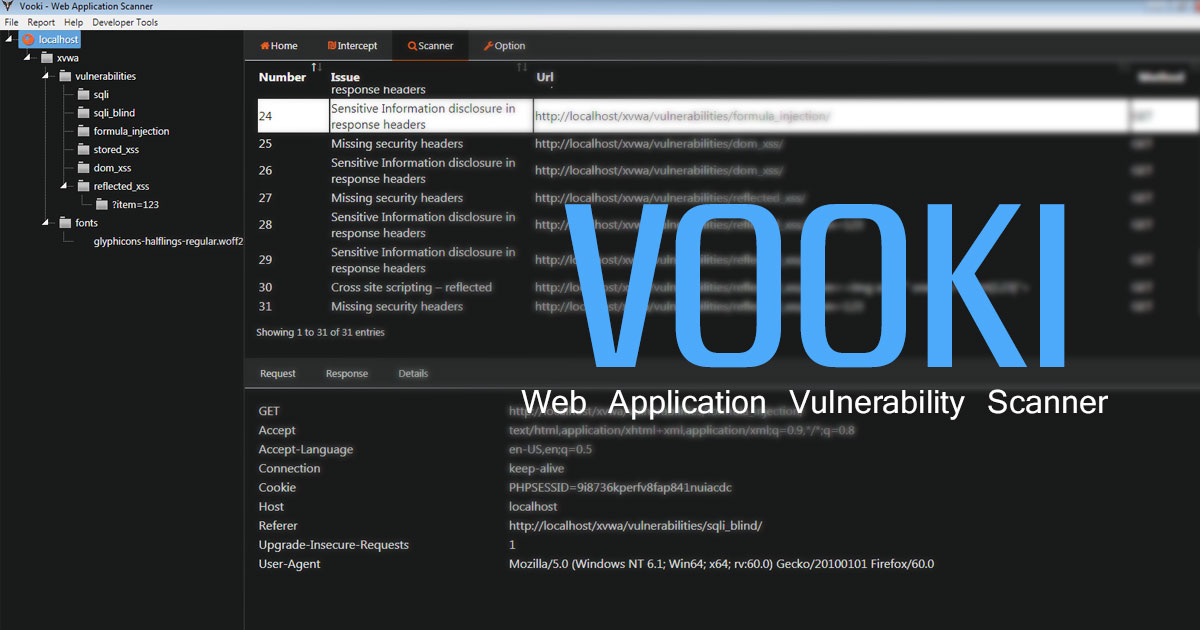
abd install [..\location\someapp.apk]Installs to emulator. Make sure emulator is on!adb uninstall [com.someapp]Exactly what to type requires a bit of work, it's basically the path the android uses. I'll describe it more later.apktool.bat d someapp.apk dump-someapp Decompiles your APK to smali filesapktool.bat b dump- someapp someapp-new.apkRebuild the edited smali filesjava –classpath testsign.jar testsign someapp-new.apkFake sign the file with some certificate, so that when we install, emulator goes "oh ok here's the signature, and it matches the file, we can proceed."
Digging decompilation
Start at a point, such an error message, and work backwards. Say the message "Invalid serial key entered!" – trace that back to where the key gets checked.
When bypassing things like serial key checks, look for check conditions:
If-eqIf-neIf-nezIf-eqz
Since applications don't have a console to print to, you could have it print to logs!
Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details