

- All Courses
- CompTIA Global Courses
-
EC-Council Global Courses
- Certified Ethical Hacker - CEH v13 - AI Powered
- CEH Master
- Certified Penetration Testing Professional - CPENT
- CHFI v10 - Computer Hacking Forensic Investigator
- Certified SOC Analyst (CSA)
- Certified Cybersecurity Technician - CCT
- Certified Cloud Security Engineer - CCSE
- Web Application Hacking and Security - WAHS
- Certified Network Defender - CND v2
- EC-Council - Cyber Security Programs
- Post Graduation Courses
- Graduation Courses
- PG Diploma Courses
- Diploma Courses
- Vocational Training Courses
-
Skill Development Short Term Courses
- Ethical Hacking
- Computer Forensic
- SOC Analyst Fundamental
- Core Python Programming
- Advanced Python Programming
- CCNA Essentials & Ethical Hacking Combo
- Web Application Penetration Testing Level I
- Web Application Penetration Testing Level II
- Network Penetration Testing Level I
- Network Penetration Testing Level II
- Reverse Engineering & Malware Analysis
- Bug Bounty Hunting
- CCNA Essential
- Firewall Administration
- A-Z Defense in Comp Security - For Corporates
Mimic - A Tool For Covert Execution In Linux
Require Further Information
What is "covert execution"?
Covert execution is the art of hiding a process. In this case, mimic hides the process in plain sight. mimic can launch any program and make it look like any other program. Any user can use it. It does not require special permissions. It does not require special binaries. It does not require a root kit.
Can this be detected?!
Of course, but only if you are looking very closely, or running a forensic tool that is looking for this sort of thing. The usefulness behind mimic is that it will prevent someone from becoming suspicious in the first place.
Other Hacking Tools
Explore All Hacking Tools »
Pftriage - Python Tool And Library To Help Analyze Files During Malware Triage And Analysis
Read Details »
ADAPT - Tool That Performs Automated Penetration Testing For WebApps
Read Details »
Stardox - Github Stargazers Information Gathering Tool
Read Details »
Modlishka - The Tool That Can Bypass Two-Factor Authentication Via Phishing
Read Details »
Stretcher - Tool Designed To Help Identify Open Elasticsearch Servers That Are Exposing Sensitive Information
Read Details »
Brosec – An Open Source Interactive Tool to Utilize Payloads and Commands
Read Details »
SpiderFoot - The Most Complete OSINT Collection And Reconnaissance Tool
Read Details »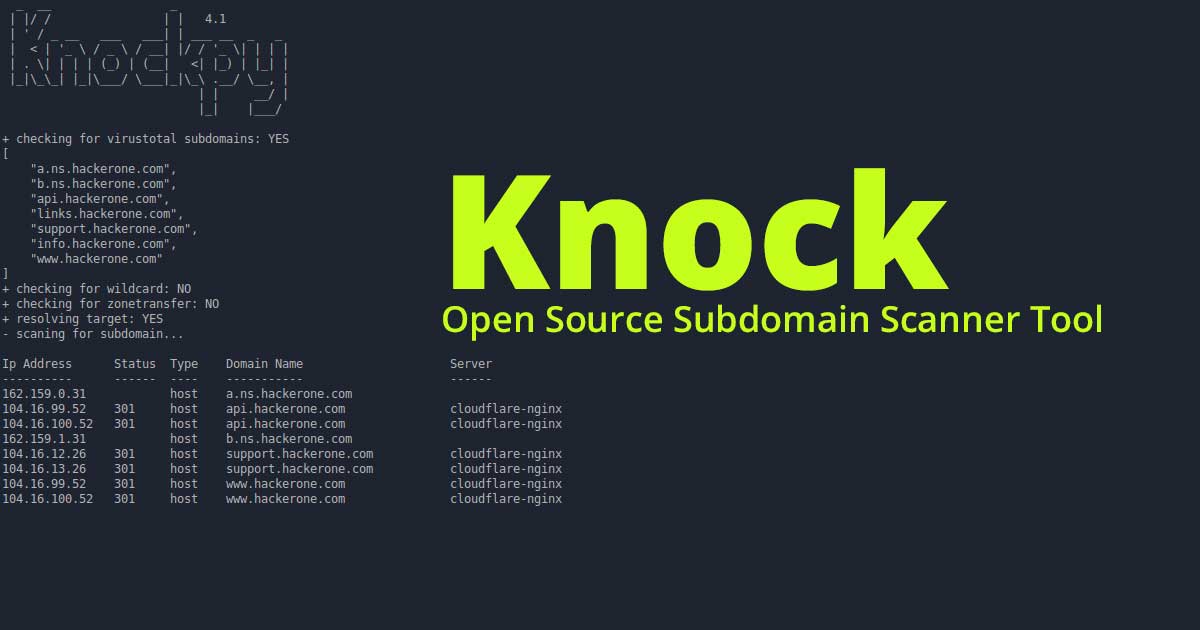
Knock - Open Source Subdomain Scanner Tool
Read Details »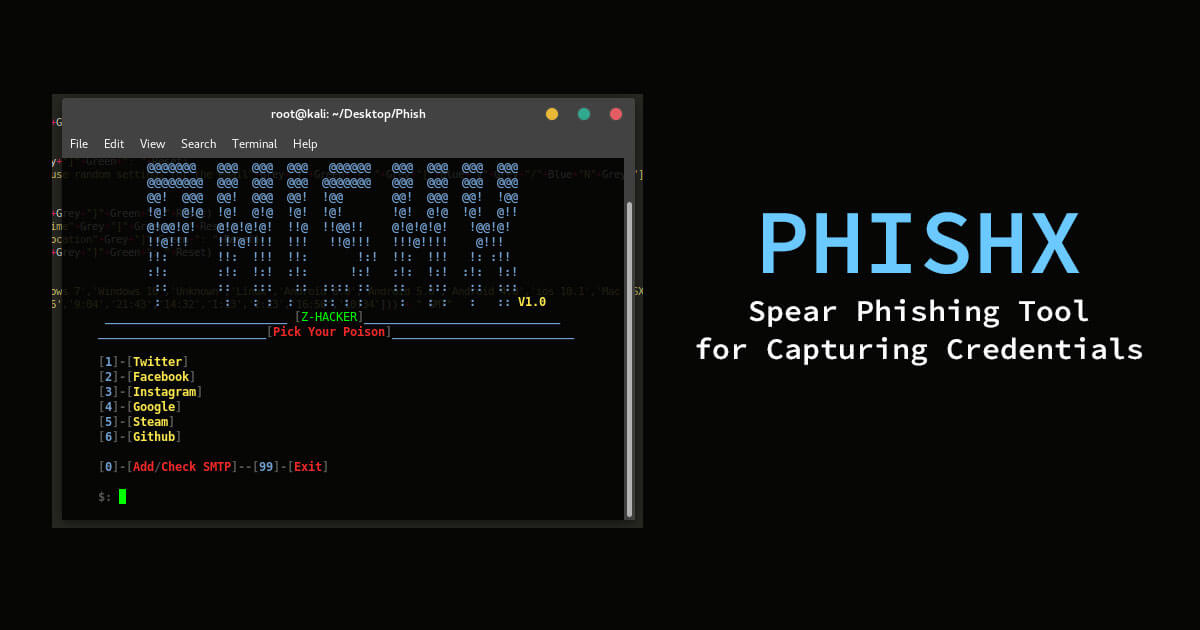
PhishX - Spear Phishing Tool for Capturing Credentials
Read Details »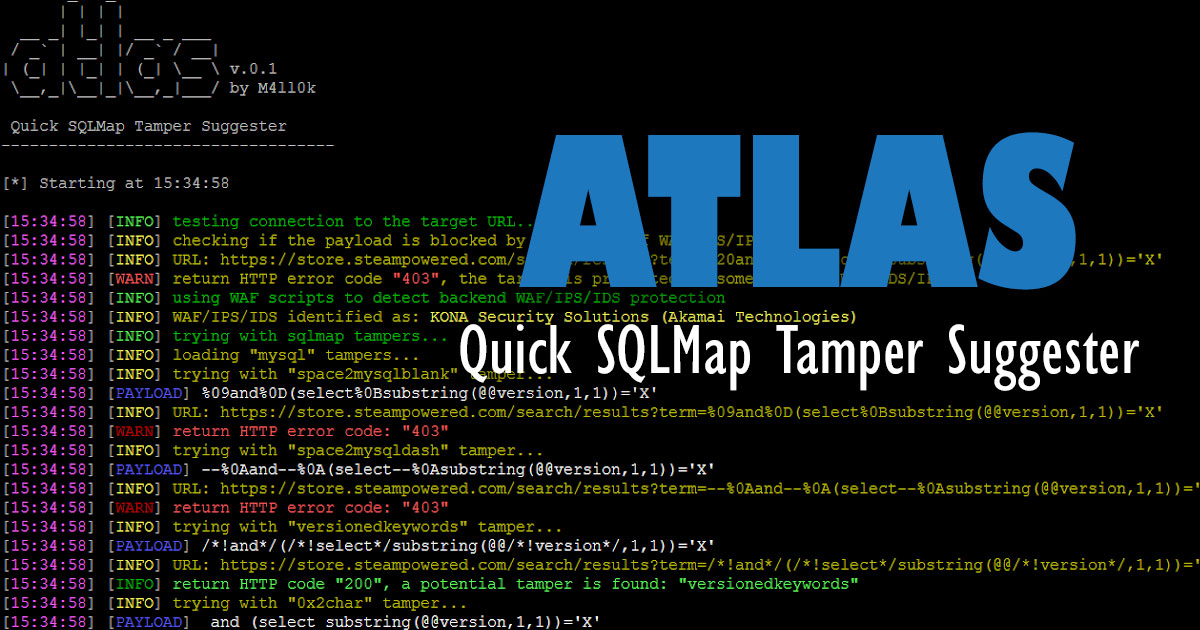
Atlas - Quick SQLMap Tamper Suggester
Read Details »
XenoScan - Open Source Memory Scanner Written In C++
Read Details »
Ettercap - A Comprehensive Suite For Man In The Middle Attacks
Read Details »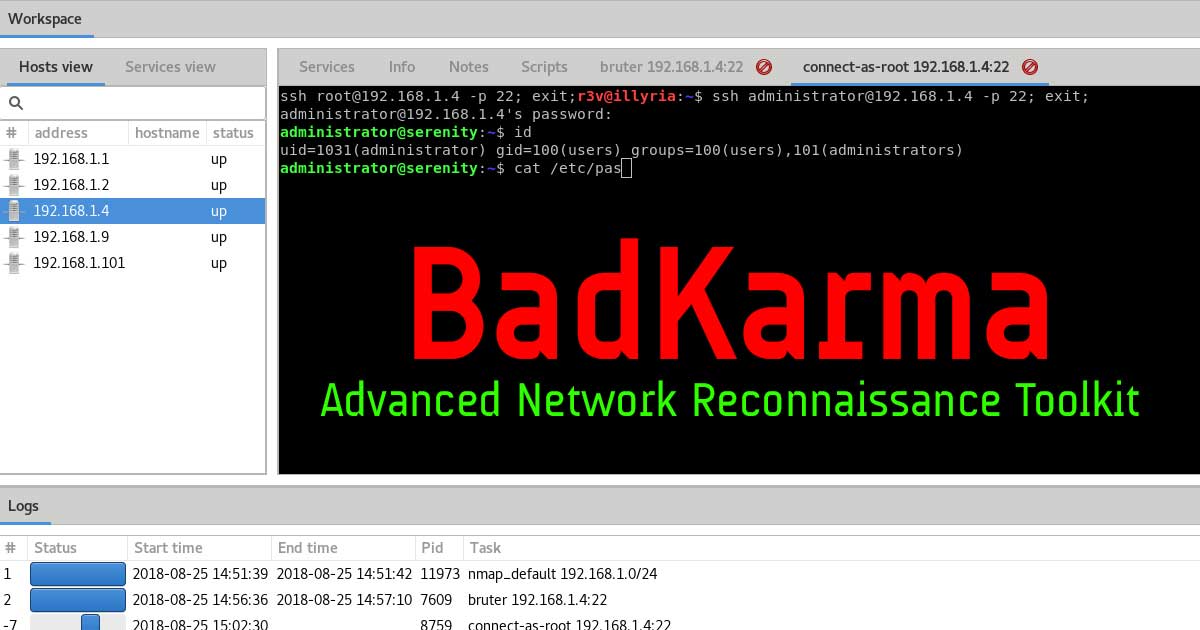
BadKarma - Advanced Network Reconnaissance Toolkit
Read Details »
XAttacker Tool – Scan and Auto Exploit Web Vulnerabilities
Read Details »
PMapper - A Tool For Quickly Evaluating IAM Permissions In AWS
Read Details »
Ridrelay - Quick And Easy Way To Get Domain Usernames While On An Internal Network
Read Details »
PhpSploit - Stealth Post-Exploitation Framework
Read Details »
PE Linux - Linux Privilege Escalation Tool
Read Details »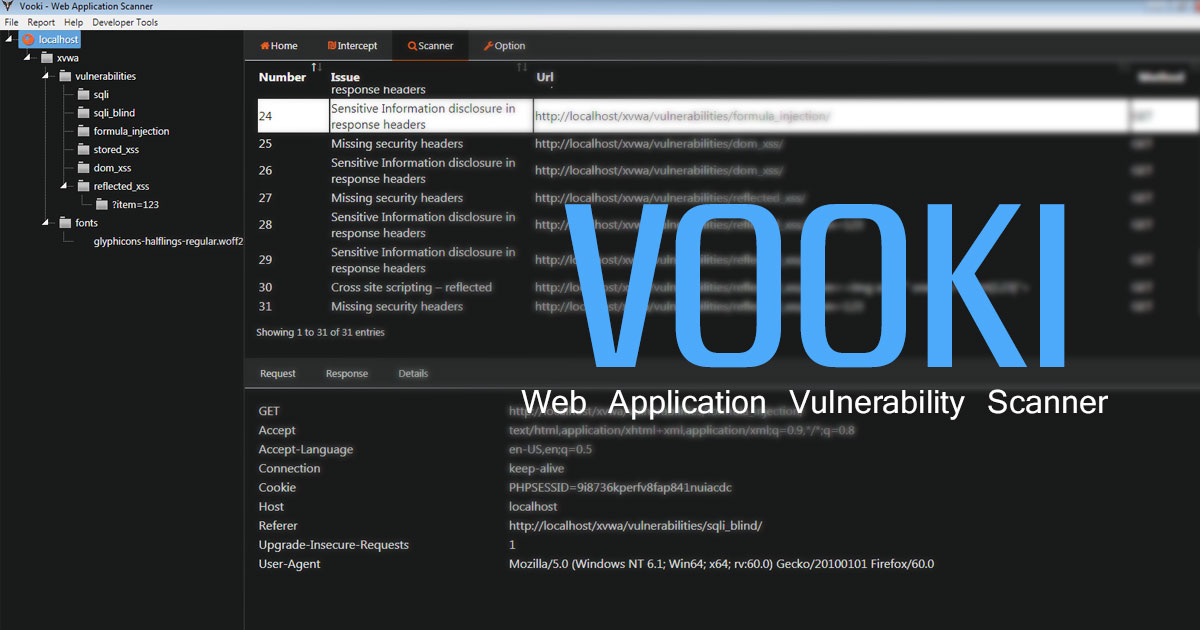
VOOKI - Web Application Vulnerability Scanner
Read Details »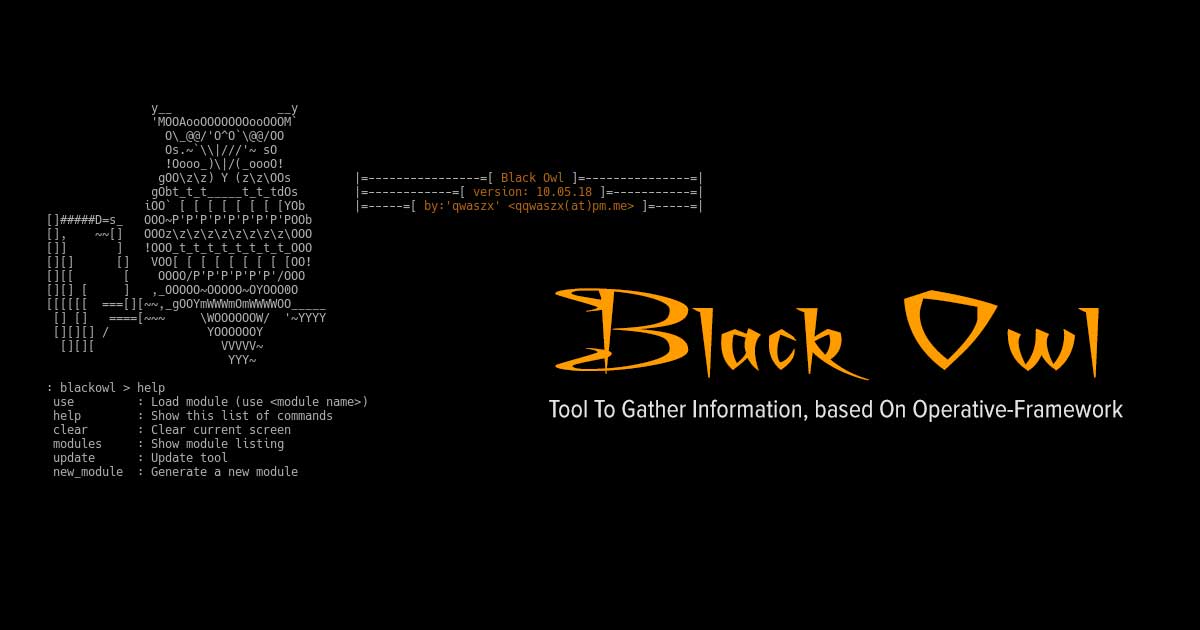
Black Owl - Tool To Gather Information, based On Operative-Framework
Read Details »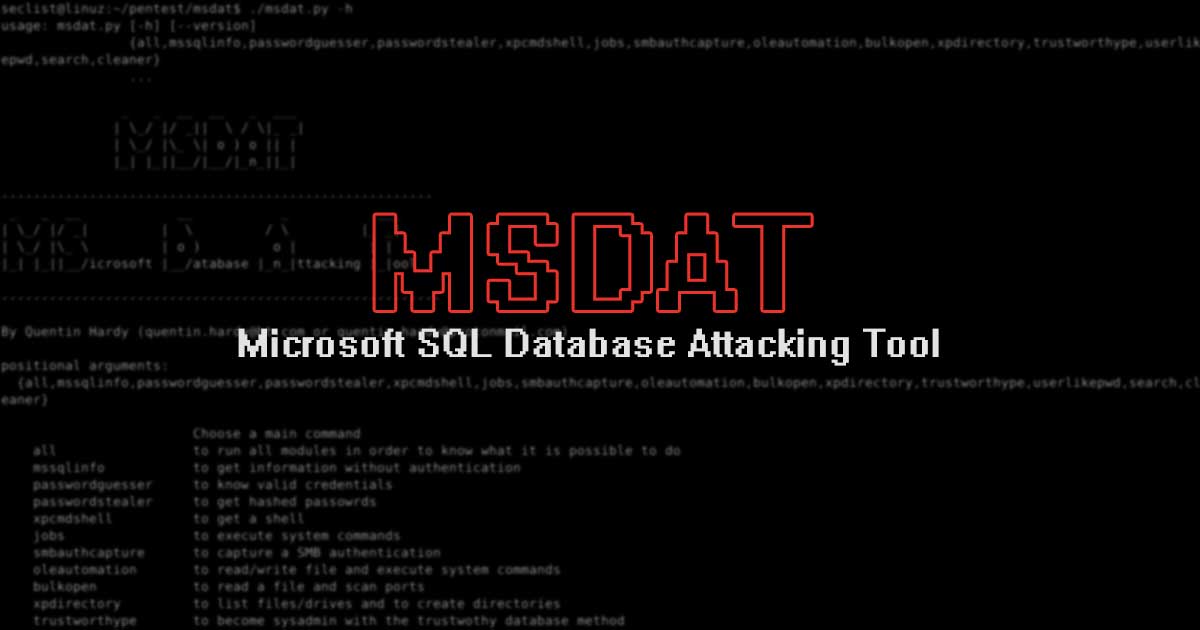
MSDAT - Microsoft SQL Database Attacking Tool
Read Details »
Autopwn v2.0 : Metasploit Automation Tool
Read Details »
GPON - Python Exploit For Remote Code Executuion On GPON Home Routers (CVE-2018-10562)
Read Details »
Mimic - A Tool For Covert Execution In Linux
Read Details »
Aircrack - the password cracking tool
Read Details »
CLOUDKiLL3R - Bypasses Cloudflare Protection Service Via TOR Browser
Read Details »
VoIP Sniffer: UCSniff
Read Details »
OWASP ZSC – Obfuscated Code Generator Tool
Read Details »
Sublist3r – Fast Python Subdomain Enumeration Tool
Read Details »
Acunetix WVS
Read Details »
Wireshark: Web vulnerability scanner
Read Details »
UFTP - UDP based FTP with encryption
Read Details »
Android hacking 'APK'
Read Details »
Executable Compression demystified
Read Details »
BitCracker – Password Cracking Tool
Read Details »
BloodHound – Red / Blue teaming tool for AD attacks
Read Details »Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
