Red Hat's last release of its flagship platform- RedHat® Enterprise Linux 8®- renders dramatic improvements in reliability, performance, and scalability. A bevy of new features provides the architect, system administrator, and developer with the resources necessary to innovate and manage more effectively. It is also characterized by Windows interoperability, a new default file system, Docker containerization and guarantees 10 years of support across any future major or minor releases.
Why learn Linux 8.0?
Stability
as opposed to frequent crashes
Adaptable
on any hardware
Duration
30 hours - 2 classes per week
Eligibility
The prerequisite being 10+2 and a general understanding of the computers.
Course Fees
Class Room Training
Rs.14,500/-
Inclusive of all taxes
Online Training
Rs.24,500/-
Rs.14,500/-
Inclusive of all taxes
What You Will Get?
30 Hours
in-depth training by Certified Trainer
Study Materials
Linux 8.0
Certificate of Completion after examination and alumni status
Course Benefits:
- Easy maintenance
- Economical
- Open source
- Customized
Your Course Path
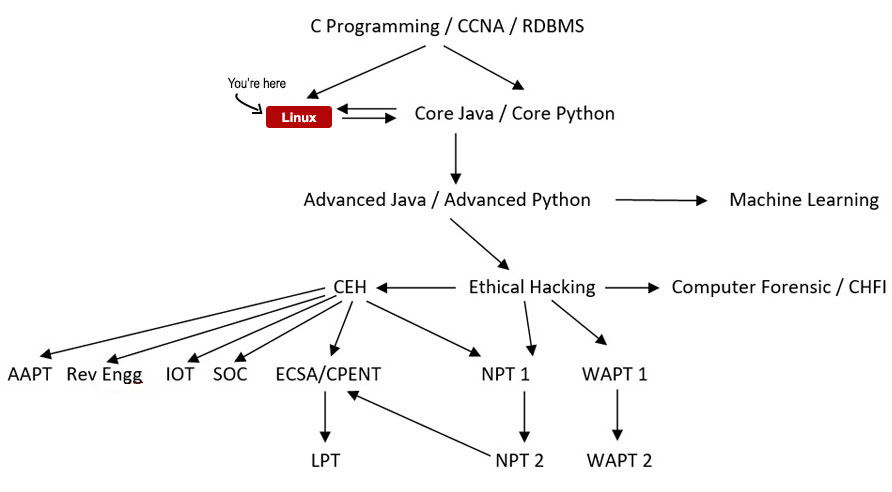
Course Details
- Course fee is Rs.14,500/-
- Duration if the course is 30 hours at 2 classes per week
- The course is basically practice based with an appropriate addition of theory
- Introducing the Linux Operating System(Day 1)
- UIdentifying Linux Architecture (Day 1)
- Initiating and Termination a Linux Sessions (Day 1)
- Installation of Centos7 and Ubuntu LTS 20 (Day 1)
- Archive, compress, unpack, and uncompress files using tar, star, gzip, and bzip2 (Day 1)
- Identifying the Linux File system (Day 2)
- Identifying Directory Command in Linux (Day 2)
- Identifying Common File Commands (Day 2)
- File and Directory Permission (Day 2)
- Identifying Different Types of Test Editors in Linux (Day 3)
- Explaining the VIM Text Editors (Day 3)
- Explaining the Nano command (Day 3)
- How many Types of User accounts and Permission types user? (Day 3)
- Standard Device Files (Day 4)
- Redirecting Input or Output (Day 4)
- Using Filters (Day 4)
- Using Pipes (Day 4)
- What is fdisk Partitions? (Day 5)
- Types of disk partition and file types on Linux machine (Day 5)
- What is LVM Partition? (Day 5)
- 5.6 Configure Hard disk partition and LVM on running Linux machine (Day 5)
- How many types of Remote access service and discuss on it (Day 6)
- What are SSH and Rsync service and configure on machine? (Day 6)
- How to take backup from scp command from one machine to another machine? (Day 6)
- Introducing of the shell (Day 7)
- Identifying Tyes of Shells (Day 7)
- Creating Shell Scripts in Linux (Day 7)
- Using Command Substitutions (Day 8)
- Using Programming Constructs in Shell Scripts (Day 8)
- Handling Parameters in Shell Scripts (Day 8)
- The file Compressions Utilties (Day 9)
- Identifying of chatting Utilities (Day 9)
- Scheduling task (Crontab or cron job (Day 9)
- What is NFS and describe on it? (Day 10)
- Configure NFS file system on machine? (Day 10)
- What is SMB and describe on it? (Day 10)
- Configure SMB on windows and Linux machine? (Day 10)
- Locating file (Day 11)
- Working with multiple files (Day 11)
- Comparing Files in Linux (Day 11)
- Identifying the Linux Process (Day 11)
- What is Apache Server and Discuss on it? (Day 12)
- Configure Apache Server of machine (Day 12)
- Discuss on LAMP server? (Day 12)
- Configure LAMP server of machine? (Day 12)
- What is Docker? (Day 13)
- What is docker container? Discuss on it? (Day 13)
- What is Docker Swarm? Discuss on it? (Day 13)
- Configure Ubuntu Docker Image on Linux machine? (Day 13)
- What is Ansible and discuss on it? (Day 14)
- What are Role, Module, task and Playbook? (Day 14)
- Create playbook through YMAL script? (Day 14)
- What log of Linux? (Day 15)
- Verify the different types of Log Service (Day 15)
- What is Syslog? (Day 15)
- Configure the syslog service on Linux machine (Day 15)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensics - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
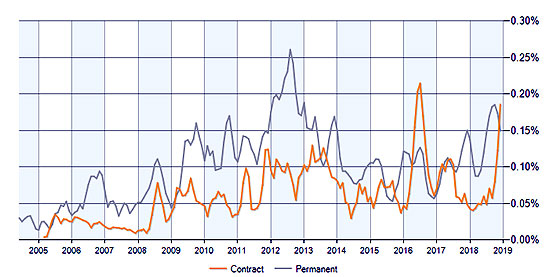
India, over the last few years has become the ultimate IT, outsourcing and MNC hub providing outstanding professional opportunities for IT experts, the Linux environment being no exception. Along with lucrative pay packets it also provides excellent opportunity to explore one’s IT potential to know and exploit the Linux possibilities to the core.
A majority of Fortune 500 companies are presently using Red Hat open source solutions. Hence IT professionals adept in Red Hat Linux technologies are in high corporate regard.
Irrespective of the type of Red Hat technology employed, there is a constant, requirement for IT professionals qualified to serve as administrators, system engineers and architects.
A graphical representation of job opportunities after completing the Red Hat Linux programs
FAQs
The syllabus covers Red Hat System Administration I, II and III.
Duration if the course is 30 hours at 2 classes per week.
The course is basically practice based with an appropriate addition of theory.
The prerequisite being 10+2 and a general understanding of the computers.
India, over the last few years has become the ultimate IT, outsourcing and MNC hub providing outstanding professional opportunities for IT experts, the Linux environment being no exception. Along with lucrative pay packets it also provides excellent opportunity to explore one’s IT potential to know and exploit the Linux possibilities to the core.
This is the ultimate academic course before you can start applying for employment in the Linux environment.
Course Fees
Rs.24,500/-Rs.14,500/-
Inclusive of all taxes
Batches
Weekend Batches For Bhubaneswar Center:
Mar, 2026
Mar, 2026
May, 2026
Weekday Batches For Kolkata Center:
Mar, 2026
Mar, 2026
May, 2026
Member of: