
Note: This article has been updated to include some of the latest ransomware attack information for attacks that occurred in Q3 and Q4 2020
"Foxconn electronics giant hit by ransomware, $34 million ransom"
"Web hosting giant Netgain forced offline after ransomware attack"
"Ransomware Attack on Carnival May Have Been Its Second Compromise This Year"
"University of Utah pays more than $450,000 in ransomware attack on its computers"
These are just a few headlines of the recent ransomware attacks that have been making waves in the news. Ransomware attacks are a cause for concern for governments, healthcare providers, educational institutions, and other organizations and businesses worldwide. They're also a major issue for their customers and employees, whose data is frequently the collateral damage of these types of attacks.
In addition to the growing rates of phishing scams, ransomware attacks have been on the rise in 2020. Check Point reports that the daily average of ransomware attacks in Q3 2020 alone increased 50% when compared to the previous six months. And what makes matters worse is that organizations that are the unlucky targets of such attacks are more likely to pay ransoms than they were in recent years. In their 2020 Cyberthreat Defense Report, CyberEdge Group shares that more than half of surveyed ransomware victims reported paying the ransom demands in 2019.
Ransomware attacks against 966 U.S. government, healthcare and educational entities cost those organizations $7.5 billion in 2019 alone, Emsisoft's Q1 and Q2 2020 research shows. Data from NinjaRMM's 2020 Ransomware Resiliency Report also shows that ransomware incidents resulted in damages of between $1 million and $5 million for 35% of the organizations whose IT pros they surveyed. That's a lot of money flowing through the prospering cybercrime market and a lot of opportunities for those organizations to sustain reputational damage.
In this article, we'll share 24 of the most recent ransomware attacks that we've seen (so far) in 2020.
Let's hash it out.
The 24 Most Recent Ransomware Attacks (to Date) in 2020
Ransomware attacks are those that use malicious software (malware) to encrypt the data and files of targets. I say this to differentiate ransomware attacks from brute force attacks (like those that have affected SQL servers globally throughout 2020) or extortion campaigns that use distributed denial of service (DDoS) attacks to overwhelm targets with traffic with the promise of stopping their onslaught in exchange for payment).
Unfortunately, there are a lot of recent ransomware attacks to choose from that we can cover in this article. So, we've decided to limit ourselves to talking about the most recent ransomware attacks that are malware-based and have made headlines in 2020.
Of course, this list is far from being complete list. Unfortunately, there are many other recent ransomware attacks that have occurred this year (way more than I have time to write about individually). However, this list at least gives you an idea of what some of the most notable ransomware attacks have been so far in 2020 and what we know about them.
How the Latest Ransomware Attack List Is Organized
For this article, we've decided to organize the content chronologically — starting with listing the most recent ransomware attacks before making our way back to the earliest attacks of the year. The reason why we're not going to list them in terms of the largest ransom payments or demands is because, frankly (as you'll soon see), many companies don't disclose the attackers' demands. (Heck, some companies don't even want to disclose that the "cyber incidents" they've experienced were actually ransomware attacks in the first place!) Furthermore, some ransomware targets choose to pay the ransom demands while others do not.
So, without further ado, let's get right to it. Here's the list of the latest ransomware attacks we've seen (so far) this year:
1. Habana Labs (December 2020)
First up on our list of recent ransomware attacks in 2020 is Habana Labs. On Dec. 13, BleepingComputer reported that the Habana Labs, which develops AI processors, allegedly suffered a cyber attack involving the Pay2Key ransomware. The attack resulted in stolen data that the attackers then leaked online — sensitive data that includes everything from code to various business documents.
So far, there's been no official statement about the incident from Habana Labs or its parent company Intel, which bought the AI firm in 2016. But this attack is just one of multiple examples in a growing trend of Israeli-based companies being targeted by ransomware operations in 2020, Check Point's research shows. According to their report:
"Pay2Key is only the last wave in a series of Iranian based targeted ransomware attacks deployed against Israeli organizations throughout recent months, in what appears to be a growing trend."
2. Randstad N.V. (December 2020)
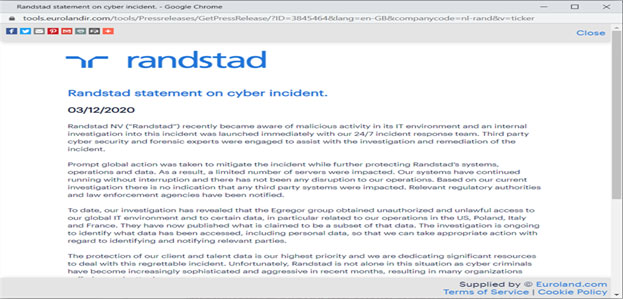
A screenshot of Randstad's official statement on their website about the recent ransomware attack. If the date looks incorrect to our U.S. readers, just remember that in the Netherlands, they write the date day/month/year.
Randstad, the world's largest global staffing agency and owner of Monster.com, was one of the most recent ransomware attack targets. This month, they announced that they were the target of an attack using the Egregor ransomware. Although it seems that the attackers haven't demanded a ransom amount, the company acknowledges that the hackers have published sensitive information.
The Netherlands-based company released the following official statement about the incident:
"To date, our investigation has revealed that the Egregor group obtained unauthorized and unlawful access to our global IT environment and to certain data, in particular related to our operations in the US, Poland, Italy and France. They have now published what is claimed to be a subset of that data. The investigation is ongoing to identify what data has been accessed, including personal data, so that we can take appropriate action with regard to identifying and notifying relevant parties."
3. Shirbit (November 2020)
Next on our list of recent ransomware attacks brings us back to the Middle East. On Dec. 1, the Israel National Cyber Directorate (INCD) and Capital Market Authority announced that Shirbit Insurance, an Israeli insurance provider that serves many government employees, was the victim of a vaguely described "data breach event" that they'd started investigating on Nov. 30. The statement says the event targeted the company's servers and websites.
From other reports that have been published since the attack first became known, it's apparently an ongoing ransomware campaign that's gone from bad to worse. Initially, the hackers, who identify themselves only by the name Black Shadow, initially demanded 50 Bitcoin in exchange for not publishing the company's sensitive client information. But after Shirbit missed the first payment deadline, that rate increased to 100 BTC and, later, 200 BTC.
Of course, Bitcoin values continually fluctuate. But just to give you an idea of what 200 BTC equates to… Consider that as of Dec. 15, coinmarketcap.com reports that one Bitcoin is worth $19,364.71. That means 200 BTC would equal more than $3.8 million U.S. dollars as of today.
Because Shirbit's representatives are refusing to play ball, the hackers have since released not one but three large batches of information via their Telegram channel. The Times of Israel reports that the attackers may have sold at least some of the stolen data to an unknown third party.
4. Foxconn (November 2020)
Now, if you thought a 200 BTC ransom demand was bad, then you're really going to cringe at this next item on our list of recent ransomware attacks. Foxconn, a global electronics giant, was the target of a ransomware attack by the DoppelPaymer ransomware operation at its facility in Juarez, Mexico on Nov. 29. BleepingComputer reports that the attackers demanded more than 1,804 BTC — or what equates to well over $34 million (USD) — in exchange for access to their decryption tool.
But just what exactly has been impacted by the ransomware attack? According to the BleepingComputer article:
"As part of this attack, the threat actors claim to have encrypted about 1,200 servers, stole 100 GB of unencrypted files, and deleted 20-30 TB Of backups."
Yes, you read that correctly: they said they deleted backup data. That's actually a growing trend that we'll talk more about later in the article. But one last thing to note on the topic of Foxconn is that because the company chose to not pay either all or even part of the ransom, the attackers published some of the company's files online on Dec. 7.
5. Barnes & Noble (October 2020)
The bookstore company Barnes & Noble is among the most notable companies to fall prey to the Egregor ransomware attacks so far. (Yes, I know we're near the end of 2020, but with how this year has been going, I'm going to add the "so far" just in case.) Although I never saw any statement from the company's main Twitter account, their NOOK account confirmed that there was an ongoing systems issue.
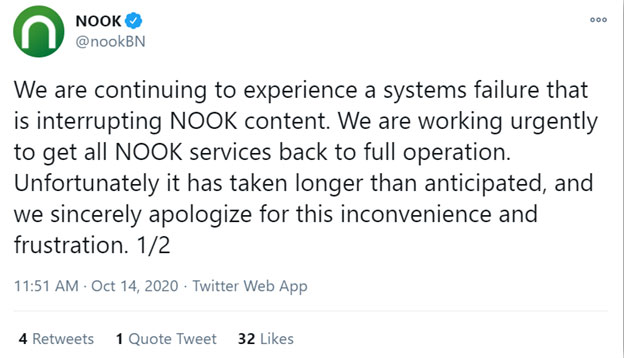
The first of a two-part tweet from the Barnes & Noble official Nook Twitter account relating to the effects of the October 2020 Barnes & Noble ransomware attack.
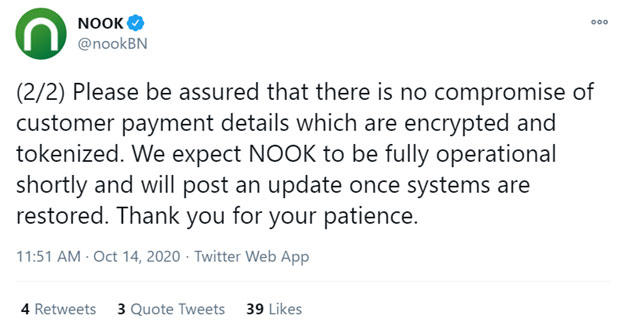
The second tweet regarding the recent ransomware attack that targeted Barnes & Nobile in October 2020.
The ransomware infection affected a variety of different corporate systems, ZDNet reports. The attacks also appear to have affected customers' B&N accounts as well as their NOOK virtual libraries, according to FastCompany.
Egregor is a ransomware gang that's been gaining notoriety over the past several months. Many of its affiliates are thought to have come from the cybercrime group Maze, which ceased operations in October. I guess cybercriminals look at their activities from the perspective that "when one door closes, another one opens."
6. United Health Services (September 2020)
United Health Services, a major healthcare provider in the U.S., announced that they were the target of "an information technology security incident" on Sept. 27. Although they state
If you're wondering why I'm talking about this in an article on recent ransomware attacks, there's a good reason. Although UHS never officially stated that the incident was ransomware related, BleepingComputer reports that two characteristics of the attack are commonly associated with Ryuk ransomware attacks:
- A note displaying a phrase common to Ryuk ransom notes, and
- Impacted file extensions being renamed to .ryk.
This would also fit considering that the FBI, CISA, and Department of Health and Human Services (HHS) issued a joint advisory stating that cybercriminals were using ransomware to attack hospitals and other healthcare providers. If it looks like a duck and quacks like one…
7. US Fertility (September 2020)
This next highlight spells bad news for patients of the US Fertility, LLC (USF), which is a large network of fertility service providers whose offices span 10 states. US Fertility delivered the bad news that someone accessed sensitive patient data without authorization between Aug. 12 and Sept. 14.
On Nov. 25, US Fertility released an official statement regarding the incident:
"On September 14, 2020, USF experienced an IT security event (the "Incident") that involved the inaccessibility of certain computer systems on our network as a result of a malware infection. We responded to the Incident immediately and retained third-party computer forensic specialists to assist in our investigation. Through our immediate investigation and response, we determined that data on a number of servers and workstations connected to our domain had been encrypted by ransomware. We proactively removed a number of systems from our network upon discovering the Incident. With the assistance of our third-party computer forensic specialists, we remediated the malware identified, ensured the security of our environment, and reconnected systems on September 20, 2020. We also notified federal law enforcement authorities of the Incident and continue to cooperate with their investigation."
The list of sensitive data that was accessed includes any or all of the following information:
- Names
- Birth dates
- Addresses
- Social security numbers
- Medical record numbers
8. Argentina's Immigration Agency (August 2020)
Let's head down south for the next item on our recent ransomware attacks list. Border checkpoints in Argentina experienced a series of technical issues after being infected by the Netwalker ransomware on Aug. 27, BleepingComputer reports. To prevent the ransomware from spreading any further, the government decided to shut down affected systems and servers for several hours. The result? Temporary suspension of border crossings.
This means that in some ways, the migratory operations of an entire country were temporarily shut down due to a ransomware attack. While we've seen devastating ransomware attacks at the city level before (like the ones that affected the U.S. city of Atlanta and the city of Johannesburg in South Africa), we don't know of another ransomware situation that's affected an entire country in such a way.
Argentina's Ministry of Interior released the following statement (as translated with the help of Google Chrome's Google Translate feature):
"The Comprehensive Migration Capture System (SICaM) that operates in the international crossings was particularly affected, which caused delays in entry and exit to the national territory.
It should be noted that the attack did not affect the critical infrastructure of the DNM, nor the sensitive personal or corporate information that the agency manages ."
Infobae.com, which describes itself as Argentina's largest digital news site, reports that the government "will not negotiate with hackers" and aren't worried about regaining access to the compromised data.
This non-payment approach to dealing with ransomware attacks is also something the FBI encourages. The logic here is that even if you choose to pay a ransom, there's no guarantee the hackers will give you access to your files. Furthermore, ponying up money could encourage cybercriminals to increase their attacks (as well as re-attack targets that previously made ransomware payments).
Furthermore, the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) even warns that companies that opt to pay or facilitate ransom payments could violate OFAC regulations and face sanctions.
9. Brookfield (August 2020)
This next item on our list of recent ransomware attacks in 2020 comes to us from the north side of the border. Darkside, a new ransomware group, claims to have carried out a ransomware attack against Brookfield Residential Properties, which is based in Calgary, Canada. ITWorldCanada reports that the company, a division of Brookfield Asset Management Inc., admitted to them that an unspecified data security incident took place. However, it didn't verify whether the attack involved ransomware or DarkSide.
Of course, Darkside themselves have decided to make it known that they were responsible for the attack:
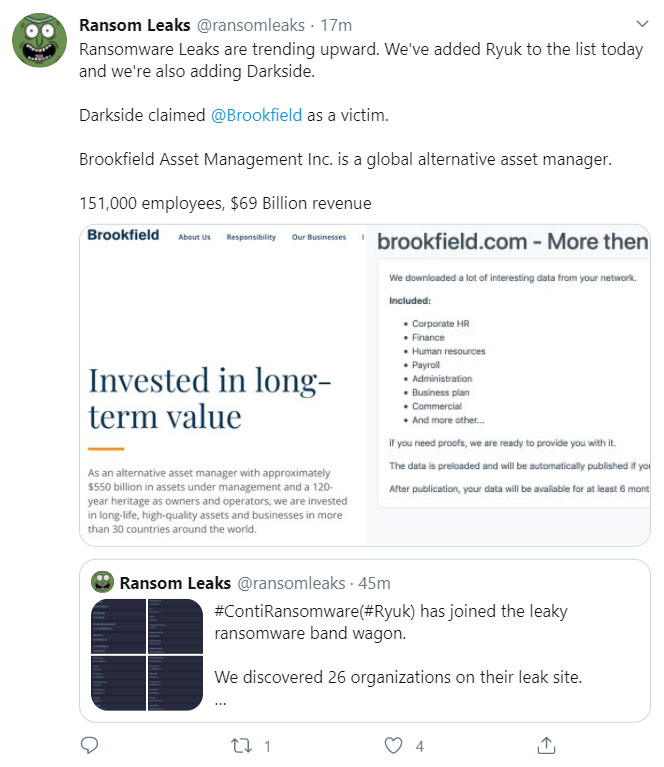
This screenshot is of a tweet from @RansomLeaks, a Twitter page that calls out news about new ransomware leaks.
The second ITWorldCanada article reports that the company was also sure to stress that "Brookfield Residential has its own corporate network that is separate from the parent company, which wasn't hit." Basically, they want to make it clear that the ransomware attack affected only that subsidiary and not the larger parent company.
10. R1 RCM Medical Debt Collections Firm (August 2020)
Next on our list of the most recent ransomware attacks comes from Brian Krebs. In August, KrebsOnSecurity reported that the R1 RCM Inc. was hit by a ransomware attack. The company, formerly Accretive Health Inc., is one of the country's biggest medical debt collection companies. They contract with more than 750 U.S. healthcare organizations and handle the personal and health-related data of tens of millions of patients.
R1 RCM Inc. chose to not disclose the type of ransomware that was used in the attack, nor provide other details about the compromise, including which systems or data may have been compromised. However, KrebsOnSecurity reports that the attack used the Defray ransomware. Trend Micro describes Defray as a type of targeted ransomware that's typically spread via phishing emails.
11. The City of Lafayette, Colorado (July 2020)
The city of Lafayette announced in August that they paid $45,000 to ransomware operators after their devices and data became encrypted via ransomware on July 27. The payment was made to receive a decryption key after the city was unable to restore systems from their backups. They chose to go the ransom payment route because it seemed like a less costly and more convenient solution to minimize lengthy service outages for residents.
Although they didn't specify the type of ransomware that was involved, the city's notice about the outage shared that the ransomware disabled the city's network systems. This impacted everything from online payment systems to email and phone services (but thankfully not the 9-1-1 and emergency dispatch systems, though). The results of their initial investigation points to a phishing scam or potential brute force attack for the cause of the ransomware attack.
So, is there any good news about this situation? Yes, although it still comes with a warning:<.
"Financial data appears to be recoverable from unaffected backups. Personal credit card information was not compromised, as the City uses external PCI-certified payment gateways. There is no evidence to suggest personal data was compromised, but out of an abundance of caution, residents and employees are advised to be vigilant to monitor accounts for suspicious activity."
12. Telecomm Argentina (July 2020)
Next on our list of recent ransomware attacks is Argentina's leading telecom provider, Telecom Argentina. The July 18 attack, which was described as a "0-Day," was detected by the company's cybersecurity team and partners. On July 20, the company released the following statement:
"Around noon on Saturday 07/18, a 0-day [ransomware] based on the Sodinokibi ransomware was detected, affecting approximately 5% of the company's IT equipment. Like all Ransomware, its purpose is to encrypt files and later request a ransom in cryptocurrency.
Our alert systems detected the attempt and as a precautionary measure the affected assets were isolated without delay, which made it possible to contain the incident hours later, without accessing any type of demand from the attacker."
CISO Mag reports that the attackers, who were identified as the REvil ransomware gang, demanded "109345.35 Monero coins (worth approximately $7.53 million)" as payment in exchange for allowing the company to recover their files. The publication also reports that Telecom Argentina also has yet to officially confirm the initial source of the attack.
13. University of Utah (July 2020)
The University of Utah (UofU) recently found itself in the crosshairs of one of the latest ransomware attacks on a higher ed institution. They released a statement about the attack, saying that their computing servers were targeted in an unspecified ransomware attack that affected approximately 0.02% of the data on those servers. Although the university used their data backups to restore some of its services and systems, they still chose to pay the $457,059.24 ransom.
Why would they choose to pay the ransom? According to the university's official statement:
"After careful consideration, the university decided to work with its cyber insurance provider to pay a fee to the ransomware attacker. This was done as a proactive and preventive step to ensure information was not released on the internet."
But UofU isn't alone — several other educational institutions were recent ransomware attack targets as well. We'll talk more about those shortly.
But first, here's one important bit of info that might be of interest to note: A 2020 study by Comparitech shows that since 2005, more than 1,300 data breaches (involving 24.5 million records) have been reported at colleges, universities and K-12 school districts in the U.S. Now, keep in mind, however, that those are just the breaches that we know about and that ransomware wasn't specifically identified as the cause. But it just goes to show that the state of cybersecurity in education has a way to go in terms of better protecting data.
Speaking of which…
14. Columbia College Chicago (June 2020)
This brings us to No. 5 on our list of recent ransomware attacks: Columbia College Chicago. The Illinois institution was targeted by the NetWalker ransomware gang, who threatened to sell students' data on the dark web if no extortion payment was made within six days.
The Columbia Chronicle shared a link to a July 17 collegewide email that indicates that some users personal information was accessed in the attack. However, it's unclear at this time whether Columbia College Chicago decided to pay the ransom or negotiate with the attackers.
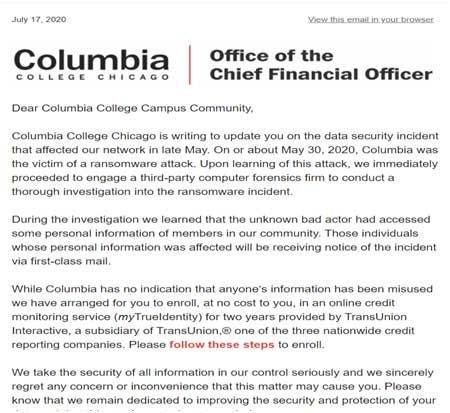
The screenshot above is an excerpt from the ransomware update email that was sent by the Office of the Chief Financial Officer at Columbia College Chicago.
NetWalker, also known as Mailto, is a ransomware strain that's thought to have made its criminal debut in August 2019. ZDNet reports that theNetWalker closed-access ransomware-as-a-service (RaaS) portal — which other hackers can use after undergoing a vetting process — launches specialized attacks against high-value targets. It's thought to have helped the NetWalker ransomware operators rake in $25 million since March 2020 alone.
15. University of California, San Francisco (June 2020)
However, Columbia College Chicago wasn't the NetWalker ransomware's only recent target. Two other institutions — University of California, San Francisco (UCSF) and Michigan State University — were also victimized by the same family of ransomware. (More on MSU shortly.)
On June 1, the university's IT staff spotted and halted unauthorized access of the medical school's IT environment. They began working with a cybersecurity firm and were able to determine that most of the school's IT environment was unaffected. ZDNet reports that UCSF opted to pay the $1.14 million negotiated ransom demand to the attackers to recover data that the attackers encrypted.

This screenshot came from the university's Jun 17 update about the ransomware attack that occurred on June 1, 2020.
According to UCSF's June 26 security update:
"While we stopped the attack as it was occurring, the actors launched malware that encrypted a limited number of servers within the School of Medicine, making them temporarily inaccessible. Since that time, we have been working with a leading cyber-security consultant and other outside experts to investigate the incident and reinforce our IT systems' defenses."
16. Michigan State University (May 2020)
MLive reports that Michigan State University was hit with the NetWalker ransomware. In their demand, the ransomware operators said the university had one week to pay a ransom in exchange for access to their encrypted files. Otherwise, the attackers said they'd leak the personal and banking related data of MSU students.
The attack, which is said to have taken place on Memorial Day, was reportedly limited to affecting systems for the Department of Physics and Astronomy. Unlike UCSF, the Michigan university opted to not pay the ransom, saying that they were heeding the advice of law enforcement.
MSUToday reports the following statement from MSU Police Chief Kelly Roudebush:
"It is important to remember that these are criminal acts being carried out by individuals seeking nothing more than an opportunity to earn a quick buck at any person or entity's expense. Paying cyber-intrusion ransoms perpetuates these crimes and provides an opportunity for the group to live another day and prey upon another victim."
This incident was followed by the discovery of a data breach that involved MSU's online store. MSUToday reports that the names, addresses and credit card numbers of around 2,600 customers was exposed as the result of a website vulnerability. The period of exposure was said to have been between Oct. 19, 2019 and June 26, 2020.
17. Blackbaud (May 2020)
Blackbaud, the major cloud computing provider for many commercial, healthcare, and non-profit entities, was the target of a ransomware attack in May. (UCSF and MSU were among the educational institutions affected by the incident because they use Blackbaud as a vendor for their philanthropic tracking activities.).
This ransomware situation is far-reaching. Even as of December, we're still seeing new reports about previously unknown organizations being identified as having been affected by the Blackbaud ransomware attack earlier in the year.
The good news for Blackbaud is that they were able to discover and disrupt the attack, ultimately blocking them from their systems. However, they weren't able to do so before the attackers successfully removed some data. According to Blackbaud's official statement:
"Prior to our locking the cybercriminal out, the cybercriminal removed a copy of a subset of data from our self-hosted environment. The cybercriminal did not access credit card information, bank account information, or social security numbers. Because protecting our customers' data is our top priority, we paid the cybercriminal's demand with confirmation that the copy they removed had been destroyed. Based on the nature of the incident, our research, and third party (including law enforcement) investigation, we have no reason to believe that any data went beyond the cybercriminal, was or will be misused; or will be disseminated or otherwise made available publicly."
The company disclosed neither the payment amount nor the type of ransomware that was involved in the attack.
18. Grubman, Shire, Meiselas & Sacks Law Firm (May 2020)
Although we've already talked about this situation in our list of the top cyber security statistics for 2020, it's definitely worth including on the list of the latest ransomware attacks. In May, Page Six reported that a hacker group that goes by the name REvil set their sights on the A-list law firm Grubman, Shire, Meiselas & Sacks. REvil used the Sodinokibi ransomware to carry out their attack.
Initially, the attackers demanded a payment of $21 million to prevent the disclosure of 756 GB of confidential client data. However, they doubled the demand to $42 million when the law firm refused to cough up the payment. They've since released data relating to several celebrities, including Madonna and Lady Gaga, and said that they plan to auction off more data.
19. Cognizant (April 2020)
Cognizant, a Fortune 500 company that provides IT services to companies across a variety of industries, shared in April that they were the target of a ransomware attack. The attack, which affected their internal systems and involved the deletion of their internal directory, also disrupted services to their customers:
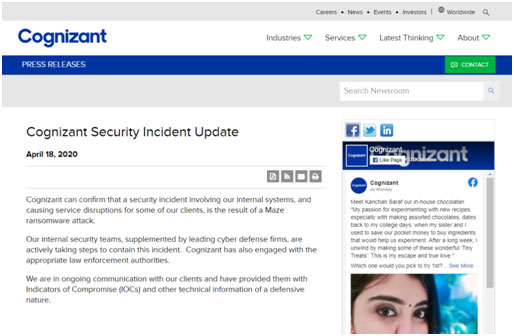
A screenshot of the official statement on the Cognizant website about the Maze ransomware attack.
In their next update on May 7, Cognizant said that they've since contained the attack and are using the experience as an "opportunity to refresh and strengthen our approach to security."
Cognizant shared in their Q2 2020 results report at the end of July that revenue across their business segments was down 3.4% to $4 billion. This was due, in part, to the April ransomware attack. Their Q2 2020 net income was $361 million, whereas their net income from Q2 2019 was $509.
20. Travelex (April 2020)
REvil decided to "help" Travelex ring in an (un)happy new year by slamming the currency exchange service provider with a Sodinokibi ransomware attack on New Year's Eve 2019. However, unlike one of REvil's other targets, the Grubman law firm, Travelex chose to pay the $2.3 million ransom in Bitcoin after their currency exchange services were crippled by the attackers.
Now, as of early August, SC Media reports that Travelex has gone into administration (the U.K.'s equivalent of bankruptcy) and has cut 1,309 jobs to help try to save the company. But I guess the mindset here is that despite the sacrifice, the company will live to see another day.
21. Chinese & Taiwanese Companies and Consumers (April 2020)
Of course, organizations, schools and governments aren't the only targets of this year's recent ransomware attacks. Ransomware attacks also target general internet users and consumers.
In April, tens of thousands of users were the victims of the WannaRen ransomware attacks on their home and company devices. ZDNet reports that a ransomware infection chain included the EternalBlue exploit that devastated hundreds of thousands of devices globally during the WannaCry ransomware attacks in 2017.
Initially the attackers demanded 0.05 Bitcoin in exchange for decrypting a victim's data. However, in an unexpected turn of events, the ZDNet report states that the ransomware authors chose to give the victims their decryption key. They did so at no cost to the victims so they could recover their encrypted data.
22. Unidentified Natural Gas Facility (February 2020)
In February, the U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) reported that an undisclosed natural gas compression facility was the target of a ransomware attack. The attack resulted in the pipeline effectively shutting down operations for two days. But how could this happen? According to the alert:
"The threat actor used commodity ransomware to compromise Windows-based assets on both the IT and OT networks. Assets impacted on the organization's OT network included HMIs, data historians, and polling servers.
Because the attack was limited to Windows-based systems, PLCs responsible for directly reading and manipulating physical processes at the facility were not impacted."
However, something that really caught our attention about this particular alert is this:
"Although they considered a range of physical emergency scenarios, the victim's emergency response plan did not specifically consider the risk posed by cyberattacks. Consequently, emergency response exercises also failed to provide employees with decision-making experience in dealing with cyberattacks.
The victim cited gaps in cybersecurity knowledge and the wide range of possible scenarios as reasons for failing to adequately incorporate cybersecurity into emergency response planning."
This situation serves as a powerful reminder to all organizations, regardless of size and industry, of the importance of cybersecurity incident and response planning and preparations. Planning to prepare your IT infrastructure and employees for these types of scenarios could be the difference between a brief situation and days of downtime.
23. The Pittsburg Unified School District of California (January 2020)
One county in California started off the new year with a ransomware attack. The Pittsburg Unified School District of CA, located in Contra Costa County, had to take its servers offline after it experienced a ransomware attack. The school district didn't disclose the ransom demands of their attackers. According to a report from KTVU, however, the attack affected "every school, office and most services in the school district."
24. Contra Costa County Library System (January 2020)
The school system attack followed closely on the heels of another attack that targeted the Contra Costa County Library System. That attack, which the library system reported on Jan. 3, caused network outages for all 26 of its branches that lasted for several days.
Recent Ransomware Attack Trends to Note (So Far) in 2020
One of the most notable trends in ransomware this year is the increasing attacks on K-12 schools. This trend was called out in a joint alert by the FBI, Cybersecurity and Infrastructure Agency (CISA), and Multi-State Information Sharing and Analysis Center (MS-ISAC). In August and September alone, more than half of the ransomware incidents reported to MS-ISAC (57%) affected K-12, versus the 28% reported January-July. The two most common strains of ransomware affecting this sector are ZeuS and Shlayer.
Recent ransomware attacks are increasingly targeting data backups, SC Media reports. Whether they're the primary or secondary target, backup attacks can be devastating for businesses. In addition to locking or encrypting files, cybercriminals can use these attacks to destroy other sensitive or proprietary data, eliminating their digital safety net.
The aggregate number of ransomware attacks decreased in Q2 2020, according to data from Coveware. However, not all that glitters is gold. Their research also shows that the numbers of recent ransomware attacks might be declining because bad guys are getting more selective about who they target and are increasing how much they charge per attack.
Coveware's Q3 2020 research shows a resurgence of ransomware attacks, including those carried out by the seemingly dormant Ryuk group. Furthermore, ransomware payments continue to grow in size, increasing from $178,254 in Q2 2020 to $233,817 the following quarter.
Furthermore, their Q2 2020 research also indicates that ransomware-as-a-service (RaaS) is also on the rise:
"The availability of free, do it yourself RaaS kits, and cheap attack ingredients pushed the barrier to entry extremely low. Deep technical expertise is no longer needed to participate in the cyber crime economy."
The Q1 and Q2 2020 data from Emsisoft that we referenced earlier shows that while there was a bit of a reprieve in terms of fewer successful attacks on government, healthcare, and educational institutions in the U.S. early this year, it looks like those numbers are going back up. However, these public sector organizations can to something to put an end to poor cybersecurity practices. They must take action to enhance their cybersecurity defenses and to mitigate risks.
Final Thoughts on the List of the Most Recent Ransomware Attacks in 2020
Okay, we've reached the end of our list of recent ransomware attacks for 2020. Needless to say, ransomware attacks suck and are bad for business. While your organization may love free publicity, making headlines as the next victim of a ransomware attack just ain't a good way to do it. However, there are things you can do to help your organization avoid becoming the next ransomware headline.
When we originally published this recent ransomware attacks article several months ago, we outlined 12 steps you can take to make your organization more secure against malware-based threats (including ransomware). It still seems pretty apropos to include it here now.
source link is: https://www.thesslstore.com/blog/recent-ransomware-attacks-latest-ransomware-attack-news/
Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsHacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read Details









