
With the rapid adoption of internet-connected and driver-assist technologies, and the spread of semi-autonomous to self-driving cars on roads worldwide, cybersecurity for smart cars is a timely concern and one worth exploring both in the classroom and in the real world. Highly publicized hacks against production cars, and a relatively small number of crashes involving autonomous vehicles, have brought the issue of securing smart cars to the forefront as a matter of public and individual safety.
Introduction
Automobiles have become increasingly more technologically sophisticated, but the underlying communication system, the controller area network, or CAN bus, has remained either largely unchanged or backwards compatible and also same with the firmware, operating systems, and application softwares.
In addition to autonomous software and hardware advances like self-driving and driver-assist technologies, newer automobiles may include Bluetooth and standard Wi-Fi networking capabilities, and many even include a persistent wireless connection over 4G LTE. Some automobiles can even update their own software and firmware over 4G LTE. These network connections significantly expand the threat surface, bringing new vectors of attack to ever more complex automotive systems.
Car hacking itself is surprisingly similar to hacking other networked devices. We can use a network sniffer like Wireshark to view packets as they move across the controller area network, or CAN bus, in an automobile.
Understanding The CAN Bus
The CAN (controller area network) bus in an automobile is the network that enables communication between the vehicle’s sensors and its various electronic control units. Modern production cars can have as many as 70 or more controlling Units controlling the engine, airbags, anti-lock braking system, tail lights, entertainment system, and more. CAN itself is a message-based protocol. The CAN bus in an automobile could be thought of as a slower version of a traditional LAN (local area network), except that the traffic is mostly UDP (user datagram protocol), a connectionless transport protocol, rather than the TCP (transmission control protocol) traffic that dominates most web and client-server networks.
There are some advantages to using UDP for CAN bus automotive communications. For one, there are fewer communication delays and therefore less variation in communication timing because UDP does not require feedback from the receiver like TCP does. Another advantage is the ability to broadcast to all controllers and sensors in the controller area network, so that a change in an actuator, like the turn signal lever, can be reflected on the dashboard and carried out on the lighting circuit without requiring multiple direct wiring circuits. The CAN bus architecture allows all of these devices to communicate over as little as one pair of shared wires running to each sensor, actuator, etc.
Open-Source Toolkit Required for Car Hacking
- Instrument Cluster Simulator (ICSim Package)
- can-utils package
- cansniffer
- canpalyer
- candump
- cansend
- Other Free Linux Packages
- USB to OBD-II adapter (For Connecting Real Automobiles)
Brief Idea About the Steps & Process of Car Hacking
For Security Reason I will not Demonstrate Individual Steps One by One. But I will give a Brief Idea about How to perform it.
Installing the Dependencies:
First and Foremost, Install all the necessary Tools and the Dependencies Regarding it. Update Your Linux Machine and install the ICSim Packages, can-utils etc. Free Library for IC-Sim Package is Available on GitHub, you can clone the Repository from there.
Prepare a Virtual Environment:
Then another Important Step is to Prepare a Virtual Environment for the CAN Network. You can use the modprobe command to load kernel modules, like the CAN and vCAN network modules from the CAN utilities library, and make sure they are able to communicate using CAN protocols on a virtual controller area network (vCAN) for our car-hacking simulator. And finally create a new network device called vcan0 of type vCAN and then turn the link on.
Run the IC-Sim Software:
Turn on the IC-Sim Package. ICSim includes two components, the car’s dashboard instrument panel, and the controls executable, which gives the user control of the virtual car, including acceleration, steering, door locks, and turn signals.
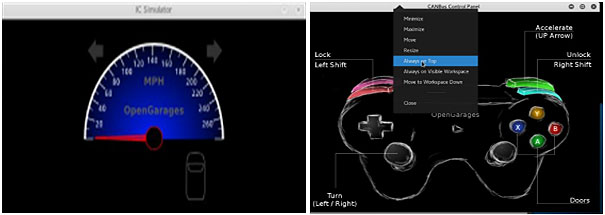
Run the Network Sniffer:
Open a terminal window running a network sniffer to view packets on this new virtual CAN network. Use the cansniffer to perform this operation. It will record all the actions done by virtual car after we give controls to it like accelerating the car etc.
Perform Replay Attack:
We can decipher the Packets Obtain from the Network Traffic but we will not do that. Rather we will effectively use those packets using Replay Attack. In a replay attack, a hacker captures packets from network traffic and attempts to re-inject them into the network later to repeat the functionality. A replay attack can be use in attempting to reverse-engineer a device’s functionality in a network, like our virtual CAN network.
Capture the CAN Bus and Dump it:
Capture the CAN Bus Traffic and use the candump to dump the Network Packets. After Dumping we can see log files containing all the dumped packets.
Replaying the CAN Bus Packets:
We can Replay the IC-Sim with the dumped packets from the candump to identify all the values and access points for further modification of that.
Reverse Engineering the CAN Bus Packets:
Final and the Most Important phase of the attack is to modify the values and re-injecting the packets. We will be using the cansend to send the final packets after modification. We can Reverse Engineer the CAN ID, turn signal etc. After we can Enumerate the CAN Data Values and gain full Control of a CAN System.
This was All about the Process how can one perform the car hacking virtually for practise in their systems.
Want to connect to the Real CAR?
On a computer, we can perform car hacking virtually, but by using an ODB-II to USB cable you can plug into your car’s on-board-diagnostic port (or OBD-II port, usually found under the steering wheel near the driver’s side floorboard) and see the results of CAN messages on your computer.
Author:
Mr. Debraj Basak
Information Security Research Analyst
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















