
Contents
According to the cyber trend, "The Indian Cybersecurity Services Industry is expected to grow from $4.3 billion USD to $7.6 billion in 2022 and register an overall CAGR of ~21% by 2025 and grow to $13.6 billion."
EC-Council's certifications and degrees always appear as the top priority list for several years and it's a cultivating strategy.
Before narrating why EC-Council feels the need to launch CEH v12, let's introduce a quick brief of CEH or Certified Ethical Hacker. CEH means nothing but getting certification for being a legal hacker who can hack an organization with permission, find vulnerabilities, plug those and defend against it to prevent malicious hackers. Think of it as a stepping stone for robust improvement. Hope you know that proverb "A rolling stone gathers no moss." Can you remember it?
Ethical hackers have a highly intellectual knowledge of computers, networks, and operating systems, and they are also bound to the organization where they work via Non-Disclosure Agreement.
What's New in CEH v12?
The EC Council says, "Cybersecurity incidents are exploding. So are cyber jobs!" The world's Number 1 ethical hacking certification center, continuously evolving a lot of beneficial structured professional courses for cyber aspirants. On 7th September, 2022, EC-Council launched an elite comprehensive course CEH v12. There are a couple of new features added in version 12 with a revolutionary learning framework. CEH v12 is divided into four important phases (LCEC) such as:
- Learn;
- Certify;
- Engage and
- Complete.
Look how these phases are quick-witted by EC.

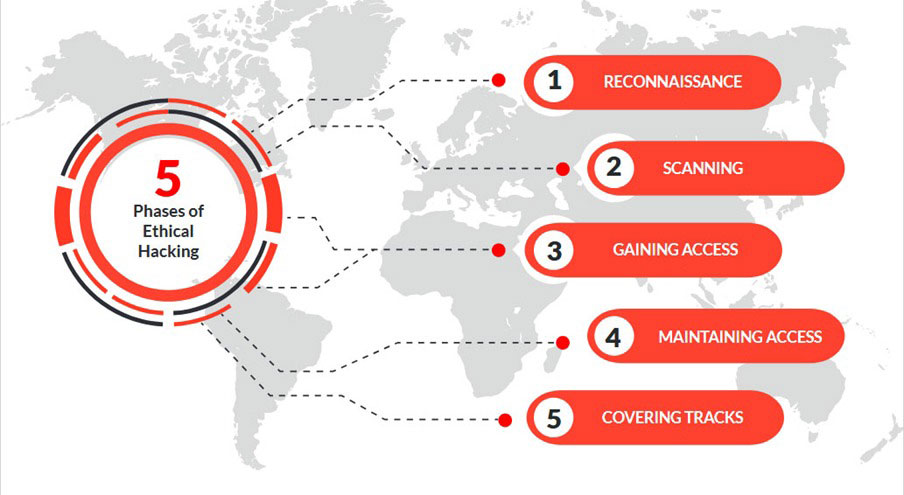
Now, why take CEH v12? This course will teach you the five-step hacking cycle.
- Planning & Reconnaissance – Grasp information about a target prior to launching an attack.
- Scanning – Utilizes different tools to collect information on websites, networks or file systems to detect vulnerabilities.
- Gaining access – An attacker gets access to a system or application that is on a network or computer.
- Maintaining access – Referred to as persistence. This allows an attacker to continue access on a target whether the machine is rebooted or the user is logged off.
- Covering tracks – After gaining access to target systems including mobile devices, IoT, operational technology, and cloud environments are critical to ensure you as an attacker do not leave a trace. This may include deleting logs, and removing tools or applications that were installed on the target.
You will get knowledge of processes, concepts, and usage of tools to accomplish all the five steps of the hacking cycle and also be able to find network polls and vulnerabilities before the strikers do and vandalize. Prepare yourself to start thinking like an ethical hacker.
According to EC-Council, "CEH v12 is a specialized, one-of-a-kind training program to teach you everything you need to know about ethical hacking with hands-on training, labs, assessment, a mock engagement, and a global hacking competition."
How does CEH v12 authorize you?
- Advantages of different learning approaches, huge engagement, certificates, and opportunities to participate in procedures for cyber enthusiasts.
- Learn Ethical Hacking in a structured setting across 20 domains.
- Build skills with over 220 challenge-based, hands-on labs with CyberQTM Labs.
- Obtain experience with over 500 unique techniques.
- Commercial-Grade hacking tools and techniques.
- Get experience to hack a real organization with CEH Elite Program.
- Attain the most recognized credential in the cybersecurity industry.
This course not only talks about teaching Ethical Hacking but also builds augment careers in cyber. Are you interested in attaining the world's no.1 credential of ethical hacking?
Exclusive learning full of in-depth knowledge helps to escalate fathom!
EC-Council delivers a formal assurance, "CEH v12 will teach you the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organization."
Now, I am gonna talk about how this globally recognized course is highlighted. What are its outlines? Let's see!
CEH v12 Tutorial
A complete A-Z module is here to supply nutrients. 20 modules make this course outline absolutely suitable for a student who wants to be a cyber-monster. New challenges every month only to judge your skills. 100% mapped to the NICE 2.0 framework with global CEH community competitions. Based on a comprehensive industry-wide job task analysis. Do you want to know those fundas?
What does EC say about their CEHv12 course learning framework? Let's go deep dive. Here's what you achieve!
The new learning framework covers a comprehensive training program to prepare you for the certification exam and the industry's most robust, in-depth, hands-on-lab and practice range experience.
Module 01: Introduction to Ethical Hacking
You will get here:
- Introduction of ethical hacking
- Segments of Information Security
- Cyber Kill Chain methodology
- MITRE ATT&CK Framework
- Hacker Classes
- Information Assurance (IA)
- Risk Management
- Incident Management
- PCI DSS
- HIPPA
- SOX
- GDPR
Module 02: Footprinting and Reconnaissance
What will you learn?
- Gather information about a potential target which includes passive and active reconnaissance which are all critical to new.
- Ensure your organization does not become a target and susceptible to attacks.
- Web spiders such as web data extractors and parse hubs perform automated searches on the targeted website and collect specific information such as employees' details.
- Analyzing websites for vulnerabilities and loopholes.
Module 03: Scanning Networks
What will you learn?
- Familiarization with different scanning tools.
- Knowing how the tools work and what information you can gather.
- How to detect somebody is scanning your network.
Module 04: Enumeration
What will you learn?
- Enumeration is destructing usernames, machine names, network resources shares and services from a web application, a system or a network.
- Learn various enumeration techniques, such as Border Gateway Protocol (BGP) and Network File Sharing (NFS) exploits, plus associated countermeasures.
Module 05: Vulnerability Analysis
What will you learn?
- Critical to determining where an attacker can tap into a network.
- After scanning the enumeration phases, the attacker uses the information collected to identify vulnerabilities and system security which helps them in exploiting the target system.
Module 06: System Hacking
What will you learn?
The attacker requires information through techniques such as footprinting, scanning, enumeration, and vulnerability analysis and then uses this information to hack the target system.
Module 07: Malware Threats
What will you learn?
- Knowing the differences of trojans, backdoors, viruses and worms are essential.
- Understanding how they work, propagate or spread on the internet are important to prevent data compromise or an attack.
- Achieving the ability to identify their symptoms and consequences is part of malware analysis.
Module 08: Sniffing
What will you learn?
- Monitoring and capturing all data packets passing through a given network using a software application or hardware device.
- How to use them to discover network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Module 09: Social Engineering
What will you learn?
- Learn social engineering concepts and techniques.
- Include how to identify theft attempts, audit human-level vulnerabilities.
- Suggest social engineering countermeasures.
Module 10: Denial-of-Service
What will you learn?
- Learn about DoS and DDoS attack techniques.
- Tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Module 11: Session Hijacking
What will you learn?
Grasp the various session hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Module 12: Evading IDS, Firewalls, and Honeypots
What will you learn?
- To set up cyber-attack countermeasures and defenses.
- How to evade these defenses.
- Learning the tactics which hackers use to bypass controls will prepare you to validate those controls.
Module 13: Hacking Web Servers
What will you learn?
Process of hacking web servers to learn the profile and trails left behind by hackers utilizing this technique.
Module 14: Hacking Web Applications
What will you learn?
- The sophistication of web applications continues to grow. So, here you can learn how to audit vulnerabilities, misconfigurations, and unintended consequences.
- Learn the protecting method of system exploitation.
Module 15: SQL Injection
What will you learn?
- Teaches the TTPS of SQL injection as well as the countermeasures for each type of attack.
- Learn about SQL injection attacks, evasion techniques, SQL injection countermeasures.
Module 16: Hacking Wireless Networks
What will you learn?
- Different types of wireless encryption
- Wireless threats
- Wireless hacking methodologies
- Wireless hacking tools
- Wi-fi security tools
Module 17: Hacking Mobile Platforms
What will you learn?
- Learn mobile platform attack vectors
- Android and IOS hacking
- Mobile device management
- Mobile security guidelines and security tools
Module 18: IoT and OT Hacking
What will you learn?
- Learn different types of IoT and OT attacks
- Hacking methodology
- Hacking tools and countermeasures
Module 19: Cloud Computing
What will you learn?
- Different cloud computing concepts such as container technologies and server less computing
- Various cloud computing threats
- Cloud security techniques and tools
Module 20: Cryptography
What will you learn?
- Learn different types of encryption algorithms
- Cryptography tools, Public Key Infrastructure (PKI)
- Email encryption
- Disk encryption
- Cryptography attacks and cryptanalysis tools.
Over 3,500 Hacking Tools!
EC-Council's Certified Ethical Hacker (CEH) certification ascertains cyber professionals that their groups can secure their systems because the certification exam focuses on the latest tools used by information security latest pros and hackers today. Let's have a quick view on it.
1. OPEN-SOURCE RESEARCH/FOOTPRINTING TOOLS
- Maltego
- Recon-NG
- FOCA
- OSR Framework
- Recon-Dog
- BillCipher
- cewl
- metagoofil
- Censys
2. SCANNING TOOLS
- Nmap
- hping2/3
- Metasploit
- NetScanTools Pro
- Zenmap
3. PROXY TOOLS
- BurpSuite
- Tor
- Proxy Switcher
- CyberGhost VPN
- Tails
- Whonix
4. ENUMERATION TOOLS
- SNMP
- MIB
- LDAP
- NFS
- Dig
5. VULNERABILITY ANALYSIS TOOLS
- CVSS/NVD/CVE/CWE
- Nessus
- GFI LanGuard
- OpenVas
- Nikto
- Qualsys
- Saint
- Network Security Scanner
6. EXPLOITATION TOOLS
- John the Ripper
- Mimikatz
- Hashcat
- pwdump
- L0phtCrack
- PsExec
- LoJax
- Scranos
7. ANTI-ROOTKIT TOOLS
- Stinger
- Rootkit Buster
- Malwarebytes Anti-Rootkit
8. MALWARE/TROJAN GENERATORS
- DarkHorse
- Angler
- Divergent
- Vaporworm
- NLBrute
- PowerShell
9. SNIFFERS/ARP POISONERS
- TCPDump
- Wireshark
- SteelCentral
- Capsa
- Ufasoft
- BetterCAP
- Cain & Abel
- XArp
10. DDOS TOOLS
- High Orbit Cannon
- Low Orbit Cannon
- HULK
- Tor's Hammer
- Slowloris
11. SESSION HIJACKING TOOLS
- OWASP ZAP
- BetterCAP
- WebSploit Framework
- Sslstrip
12. IDS TOOLS
- Snort
13.ANONYMIZERS
- Boomproxy
- Zendproxy
- webproxyserver
- anonymizer
14. HONEYPOTS
- KFSensor
- SPECTER
15. WEB SERVER HACKING/SQL INJECTION TOOLS
- ZAP
- BeEF
- Burp
- THC Hydra
- DVWA
16. WIRELESS ATTACK TOOLS
- Pineapple Tetra/Nano
- Air Suite
- Airgeddon
- NetSurveyor
- Acrylic
- Vistumbler
- WifiManager
- InSSIDerPlus
- Ekahau HeatMapper
- Wifphisher
- Reaver
17. MOBILE DEVICE ATTACK TOOLS
- Agent Smith Attack
- Root Genius
- SuperSU Root
- Z4root
- Yuxigon
- Trimgo
- Yalu
- Spyzie
- Exodus
- KeyRaider
- Spyic
- Frida
- Fing
18. IOT TOOLS
- IoTSeeker
- RIoT
- Foren6
- RFCrack
- Attify Zigbee Framework
- ChipWhisperer
- Thingful
- Suphacap
- CloudShark
- IoTsploit
- BladeRF
- HackRF
- GQrx
- Firmwalker
- KillerBee
19. CLOUD EXPLOIT TOOLS
- Sysdig
- Knative
- Spyse
- S3Scanner
- Pacu
- DumpsterDiver
- CCAT
- GCPBucketBrute
- Dockerscan
- AWS pwn
CEH v12 Certification


Keep in mind what the EC-Council tells!
"When you successfully achieve the C|EH certification, you will be equipped with every skill you need to uncover vulnerabilities and secure the systems, networks, applications, databases, and critical data from malicious hackers."
Lab setup
Build skills with over 220 challenge-based, hands-on labs with CyberQ™ Labs. OS used for labs is – Windows 11, Windows Server 2022, Windows Server 2019, Parrot Security, Android, and Ubuntu Linux.
EC says, "With over 220 hands-on labs, conducted in our cyber range environment, you will have the opportunity to practice every learning objective in the course on live machines and vulnerable targets. Pre-loaded with over 3,500 hacking tools and a variety of operating systems, you will gain unprecedented exposure to and hands-on experience with the most common security tools, the latest vulnerabilities, and widely used operating systems on the market. Our range is web accessible, allowing you to study and practice from anywhere with a connection."
Know about the CEH v12 exam pattern
A knowledge-based exam where you attempt to answer
- No. of questions – 125 MCQs
- Exam duration – 4 hours
- Passing score – 60-85% (based on the difficulty level of the exam)
The CEH Practical is a skill-based exam. Here you need to complete 20 practical challenges in under 6 hours.
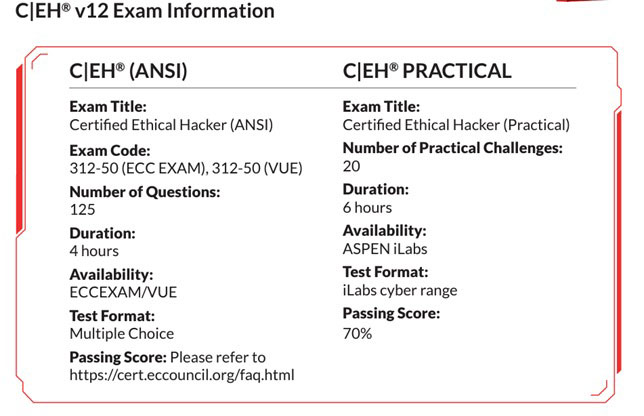
You can only be known as a CEH Master if you pass both of these exams.
"Our ANSI 17024 accredited examination goes through rigorous job task analysis, careful curation of exam domains, extensive work to build world-class training and hands-on components to provide candidates with an intensive hands-on experience throughout the program."
CEH v11 vs v12
Eager to know what makes the difference between them! CEH v12 is a fully licensed and deployed operating system like Windows 11, Parrot security, windows server 2022, windows server 2019, Android, and Ubuntu Linux. It is filled up with recognition, endorsemen,t and mapping.
3000+ pages student manual, 1676 illustrated instructor slides, 3500+ hacking and security tools, 220 hands-on-lab as engagement, extra 33 labs, chances to gain 519 attack techniques, 20 refreshed modules, the addition of new technologies like analysis, persistence establishing techniques, evading NAC, Endpoint security, Fog computing, Edge computing, and Grid computing. CEH v11 is consistent with 1640 slides, 200 labs, and 420 attack techniques.
Now let's get to the insightful chapter: CEH ENGAGE.
This makes CEH's new version 12 amazing. Here, not only students will be able to learn everything about ethical hacking but also be able to test their skills in the exam with the new engaged methodology. Each learner will also achieve a real-life ethical hacking assignment that they complete as part of the program. This exercise provides them with extensive experience on how to perform these tasks in the real world.

The number of cyber-attacks is increasing and along with that, the demand for skilled ethical hackers is also increasing. This modernization required making the key design more subtle to enter into the world of ethical hacking professionals.
Job Prospects
After completing this course, you can see yourself as:
- Mid-Level Information Security Auditor
- Cybersecurity Auditor
- Security Administrator
- IT Security Administrator
- Cyber Defense Analyst
- Vulnerability Assessment Analyst
- Warning Analyst
- Information Security Analyst 1
- Security Analyst L1
- Infosec Security Administrator
- Cybersecurity Analyst level 1, level 2, & level 3
- Network Security Engineer
- SOC Security Analyst
- Security Analyst
- Network Engineer
- Senior Security Consultant
- Information Security Manager
- Senior SOC Analyst
- Solution Architect
- Cyber Security Consultant
Conclusion
Can you estimate your cyber range? Not just a cyber enthusiast, if you prepare yourself to execute core cyber skills by practicing conscientious skills and implementing real-life network topology, you can take part in the competition. CEH v12 course makes a cyber aspirant for cracking the toughest cyber challenges.
EC believes in sharping cyber skills in a safe-purpose built environment with next-generation work infrastructure.
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















