
Suppose, one day while surfing the net, you imagine what this net matters. How is it possible that we find so much information on the web? We can't deny that this WWW (World Wide Web) alone has made a virtual home for people to join and live from different edges of the Earth. Along with that, you are thinking that the activities of such people on this net are also heard in news headlines who have done criminal acts and destruction using the net.
If you got curious about it, then surely again you will sit down to scour the net to solve your thoughts. Let me say friend for your research convenience that this web is spread over a huge area with non-estimated depth.
If you want to guess all unknown information, you have to creep down slowly to that depth. Before that, you need to acquire knowledge about each stair. The deeper you dive into this web ocean, the more you will see the light diminishing. Then at a such stage, you will find everything hidden in the darkness and even you too!
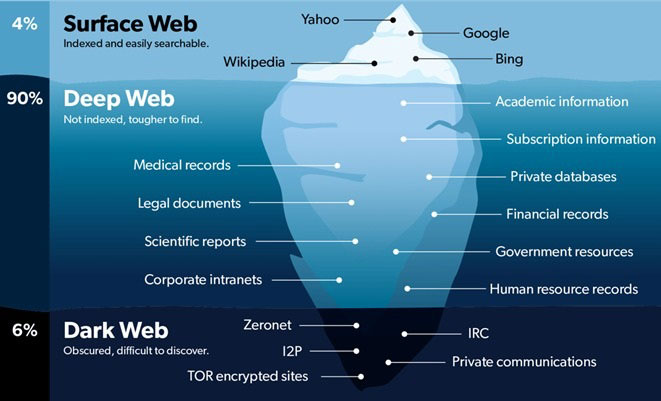
As we have known since childhood that 3 out of 4 parts of the earth are water and 1 part is land, similarly, we also know that this enormous web ocean is divided into three kinds of web.
1. Surface Web
This is the internet or common web we all know and love. Used for our daily activities like social networking, reading news, and many more. Conventional web spiders use sophisticated algorithms to collect data from hyperlinked pages and you browse it from search engines like Google or Yahoo.
It is also known as visible web, indexed web, and Clearnet. Includes a fraction of the entire internet with approximately 19 terabytes of information.
2. Deep Web
People start interpreting it's an illegal zone where criminals, drug users, terrorists, black money markets, sexual deviants, and different kinds of imposters reside. But that's not a fully correct conception.
You should note down that in a sense, an organization's intranet is also known as Deep Web. Nobody outside the company has access to the information in it. The deep web has 7500 terabytes of information approx. which is beyond what we just see on the surface web.
The fact of this kind of web is that it is inaccessible to normal search engines. To use the deep web, you can use the TOR browser. For example, mail and online banking information are contents of the Deep Web. Neither these are publicly accessible nor indexed by search engines. Using the Deep Web, 100 billion dollars worth of illegal activity is conducted worldwide every year.
Now we come down to the level that is our main topic of discussion, the Dark Web. Do you see only darkness around you? Are you frightened? So, let's talk about it for your better understanding.
3. Dark Web
A risky sphere consisting of black hats in a larger number! It is the hidden internet or Deep Web's wicked clone where users can be completely anonymous, work in isolation, and find information that is not publicly available through normal channels.
For some who are fed up with the intrusive marketing policies of companies like Google or Facebook, the Dark Web allows them to keep their search norm entirely private. Now, don't fall into such a type of thought that the Dark Web is good for all.
The unseen side of the Internet
The Internet has been modifying us since it was invented. It is connected with us in such a manner where our information, works, likes, dislikes, and hobbies all are stored. We never imagined it before!
It is not as simple as we see it from above. The unseen side of the internet – The Dark Web! Full of implicit website links which are blocked off, criminals, black hat hackers, predators, hitmen, and many more. Even here you can search for multiple numbers of banned books, scriptures, disturbing footage, VPNs, torture games, and controversial blogs.
It is accessible through a specific browser but it's hidden under a layer of protection. Simply, it can be said that the pool of information is under an umbrella. Is it kind of an observation of actions as it unfolds or is it just like a curiosity?
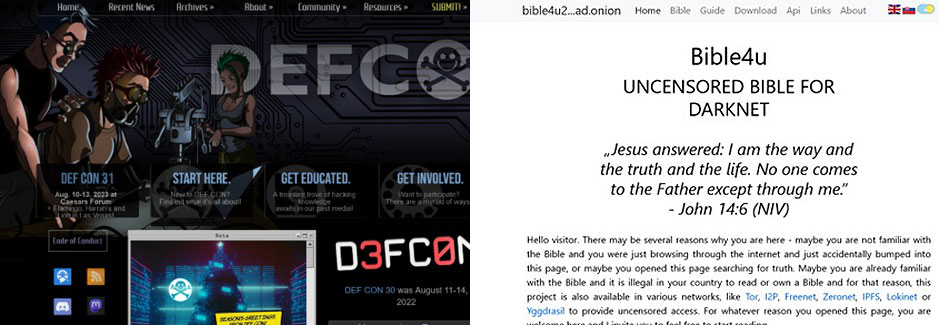
Let's explore the unseen part. Before that, you need to install the Tor browser. https://www.torproject.org/download/
The Tor browser is a software package that enables anonymous communication. The name is derived from an acronym for the original software project name "The Onion Router". This browser anonymizes traffic by bouncing it through a series of servers before reaching its destination.

The US government invented this for their militaries so that communication could not be leaked by third parties.
Tor directs internet traffic through a free, worldwide volunteer network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis.
Using Tor makes it more difficult to locate internet activity along with visiting websites, posts, instant chats, and other communication fields. If you judge from another point of view, then you can find this browser is intended to protect users' details as well as safeguard their privacy. Some websites restrict access to users who use Tor or block requests from Tor relays. The loading time of the webpages in this browser is comparatively slower than Clearnet or regular links as it provides high encrypted security.
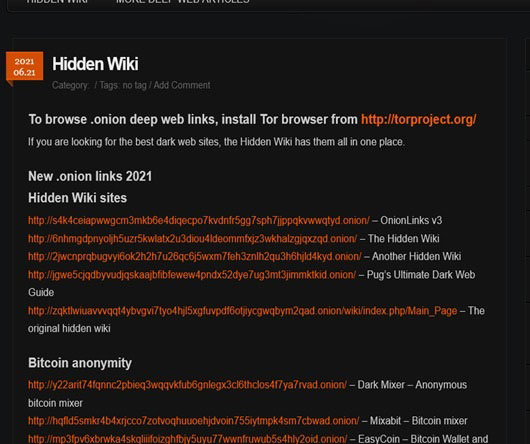
Heard about the Hidden Wiki?
There are the biggest myths about the Dark Web. Some even think that it might be inhabited by ghosts. Break that and come to the main point in a straight way.
Just as there is Wikipedia to know about any information on Google, similarly you have to come to the directory, Hidden Wiki to get active creepy darknet .onion sites. Maybe you are eager to know about those eerie onion sites.
These sites are basically like normal URLs, but they are designed to be only accessible through the Tor network. This means that they are not indexed by search engines like Google or Bing.
When you visit a .onion site, your traffic is routed through the Tor network. This makes it very difficult for anyone to track your activity or figure out who you are.
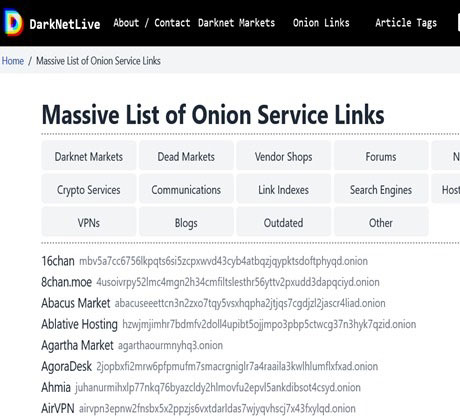
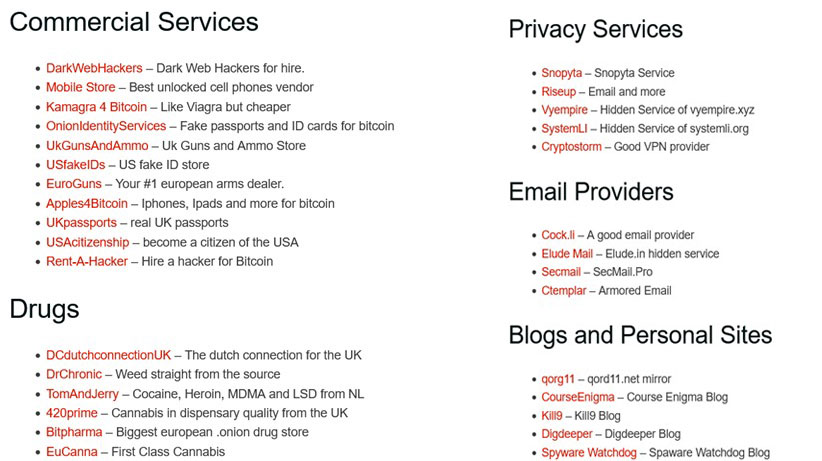
This type of link can be found in the site's source code. Let's see some examples of .onion links in the hidden wiki directory.
Services inside the Dark Web!
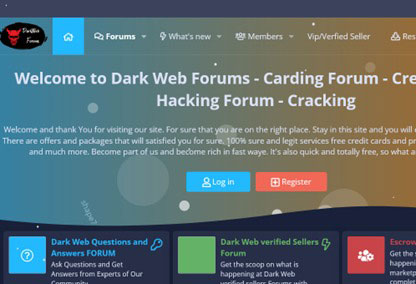
It's also a place where frauds exploit its anonymity to run off with guns, drugs, black money, data breach for sale and even to ruin human life.
It's also true that the government uses it to prevent political breaches and also for spying scammers. Always remember that it is legal to access but any illegal activity can get you arraigned.

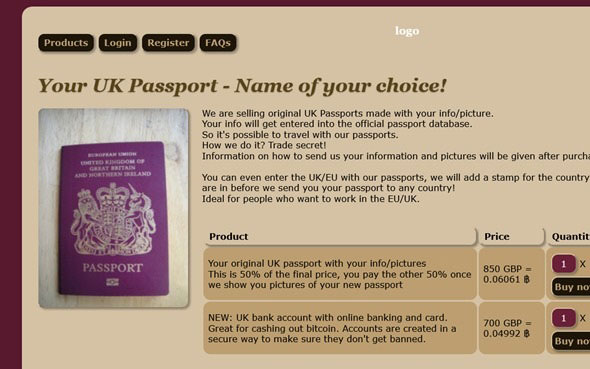
Such things that are taboo in society, are discussed in this forum. You may ask yourself a couple of times who the developers are and how they provide services here! Actually, in this web, mail, and hosting services all are different. Most importantly, the profile IDs you will see here are temporary and fake! There is nothing that is not being sold on the dark web. Vegetables, stolen goods, drugs, pornography, hosting, domains, and credit cards are all being sold and even money laundering.
Dangerous merchants and sellers are there! Though the dark web covers very little space (6%), a huge share is claimed by this incognito marketplace and most of the people are connected here directly or indirectly.
Not only that in darknet markets, but you can also find hitman hiring sites, red rooms, rent-a-killer sites and many more dark sites.
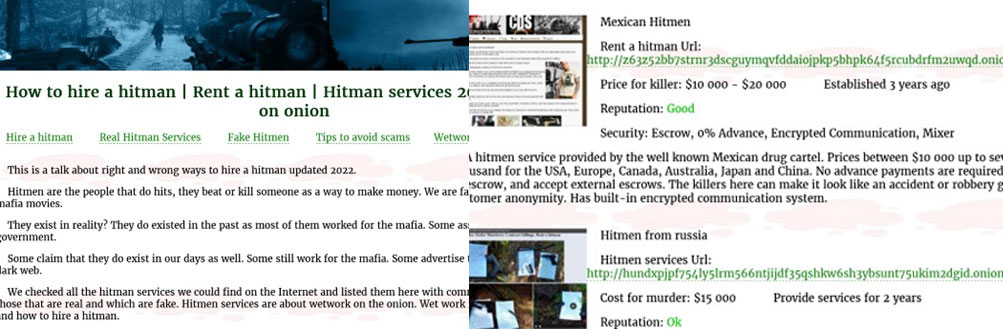
Is it the other Internet?
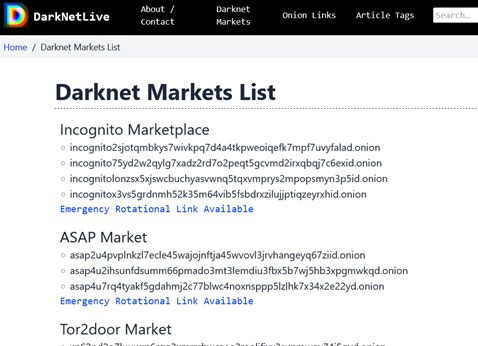
If you enter here once and you too get involved in this corruption, then you can never come back to get rid of it. Do you want to make yourself as dark as this web is?
See another dark part of this for the experience.
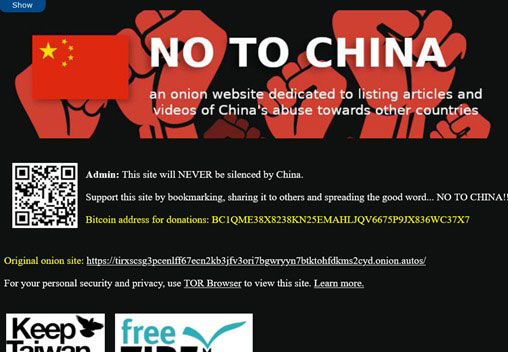
They say that this website was made for capturing China's movement and also giving a 100% guarantee that this site will never be silenced by China.
Are we safe?
It's good to hear that you like to explore the fascinating world of the dark web but don't get inside it.
Some dark web live proofs are here.
The Dark Web is often depicted as a shadowy, underworld marketplace where all manner of illegitimate activities take place. Here you go!
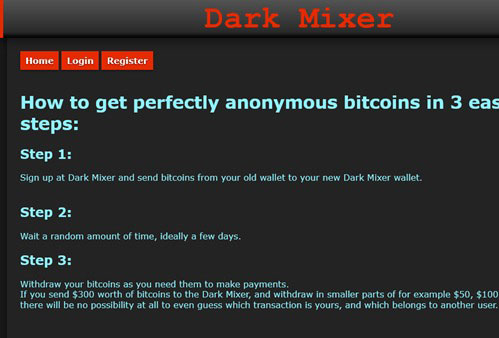
Is it possible to earn money from the Dark Web? Any methods! You may look on social media that 100% Legal earn up to Rs. 50,000 per month, and get rich using Dark Web which motivates you to earn money most easily. Now if your fingers are itching for registration, then I would say stop there right now!
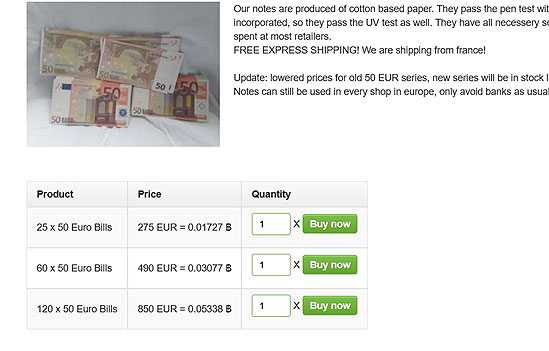
Yes, Bitcoin marketing is booming now. But what is the need to earn money with bitcoins illegally from there? The surface web is sufficient for that. If you need to earn money, then put in the best effort legally. Do not coordinate with the scammers. Here, the possibility of your loss is high. Hey! Have that money and heading aroused your greed? Oh no! have you clicked ‘Buy now' button and gonna register!! Bullshit. Check your account balance at once.
Conclusion
There is no end to it. Peeling the onion one after another, you will get to see finer to the finest high-encrypted sites. Most traps are left there. Its depth is so deep from the Clearnet that you will feel like you have to the Mariana Trench when you come down.
If you come here without strong technical sound and good comprehension of the dark web's each strategy, you will be consumed by it. It's fine that you have curiosity but don't apply it excessively to deplete yourself.

Do you think only scammers and black hat hackers are there on the Dark Web? A big NO in reply. There are even international agencies' mirror sites. For example, the CIA (Central Intelligence Agency)!
Be cautious at each step as long as you dive into the Dark Web. Visiting unknown onion sites is extremely risky. It's dangerous!
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















