
Cyber War also termed cyber warfare is a form of war conducted on the platforms of computer systems and the networks connecting them, executed by states or their proxies against other states. Cyberwar is usually prosecuted against government and military networks in order to disrupt, destroy, or deny their use.In recent years, the media has been creating a sensation about the prospects of cyber warfare between nations. It gives usgood interesting stories. In the imagined scenario, most of the national governments are assembling and training elite teams of computer hackers prepared to infiltrate or take down the computer network of an enemy nation. Every nation has the armaments– computers, and software - to be a crucial threat without owning a superpower.
The Real Start of Cyber War:
The notable incident that alluredmedia attention was a three-week sway of distributed denial of service (DDoS) attacks on numerous Estonian websitescommencing on April 27, 2007. At this time, Estonia and Russia were engaged in a debate over the removal of the Bronze Soldier of Tallinn, a Soviet war memorial in Estonia. Estonia moved the statue on April 27, which results in vigorous protests by traditional Russians (1300 were arrested). Since the DDoS attacks started after the relocation of the statue, the conflict was understood to be the reason for the attacks. Uncertainty about the assassin of the DDoS attacks straight away fell on Russia. The Estonian foreign minister and defense minister publicly accused Russia of synchronizing the DDoS attacks, even though they claimed that they had no proof. They brought the charge to the notice of NATO, and the Estonian president discussed it with U.S. President Bush in a June 25, 2007 meeting.
The DDoS attacks on Estonia may not have been a real "cyberwar," but many governments are taking the possibility of nation-sponsored cyber-attacks seriously. For example, the United States set a Cyber Command (Cybercom) at Fort Meade, Maryland, in May 2010 to protectthe American military framework. The United Kingdom has established a cybersecurity functioning center at Government Communications Headquarters (GCHQ) based in Cheltenham.
Most Powerful Countries in Cyberspace:
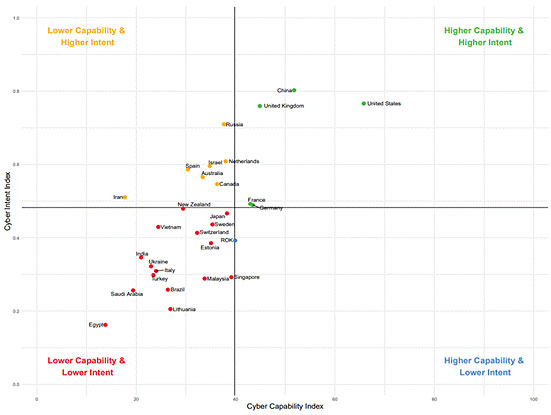
According to recent research by the National Cyber Power Index 2020 below are the most powerful cyber countries in the world are as follows:
- United States
- China
- United Kingdom
- Russia
- Netherlands
- France
- Germany
- Canada
- Japan
- Australia
In determining the National Cyber Power Index (NCPI), the research team follows an "all of country approach" to calculate and rank cyber power countries.
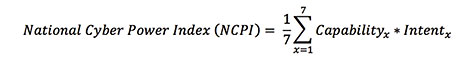
Also, the research group identifies seven objectives on the basis of the index calculation. They are:
- Monitoring and surveillance of Domestic Groups;
- Enhancing and reinforcing National Cyber Defences;
- Controlling and influencing the Information Environment;
- Foreign Intelligence Collection for National Security;
- Commercial Gain or Enhancing Domestic Industry Growth;
- Destroying or Disabling an Adversary's Infrastructure and Capabilities; and,
- Defining International Cyber Norms and Technical Standards.
 Source: https://www.secureworld.io/industry-news/top-10-most-powerful-countries-in-cyberspace
Source: https://www.secureworld.io/industry-news/top-10-most-powerful-countries-in-cyberspace
The types of cyber warfare attacks:
There are several examples of reputedly cyber warfare in recent history, but there is no universal, formal, definition for how a cyber-attack may account for an act of war.Researchers have identified, seven types of Cyberwarfare attacks. They are:

Espionage:
Espionage refers to spying or monitoring other countries to steal secrets and confidential information. In cyber warfare, this can involve using botnets or spear phishing attacks to compromise sensitive computer systems before withdrawing sensitive information.
Sabotage:
All Government organizations have sensitive information stored in their databases and the major riskis compromising those. Hostile governments or terrorists may lootsensitive information, destroy it, or leverage the information and blackmail the concerned person.
Denial-of-service (DoS) Attacks:
DoS attacks prevent authorized users from using a website by overflowing it with false requests and the website is forced to handle these requests. This type of attack can be used to derange critical operations and systems and block access to sensitive websites by civilians, military and security personnel, or research bodies.
Electrical Power Grid:
Attacking the power grid allows assailants to disable critical systems, derange infrastructure, and supposedly result in bodily harm. Attacks on the power grid can also disrupt communications and disable services like text messages and communications.
Propaganda Attacks:
This is a type of attack where the attacker attempts to control the minds and thinking of people living in or fighting for a target country. Propaganda can be used to expose embarrassing truths, spread lies to make citizens lose trust in their country, or make them take sides of the enemies.
Economic Disruption:
Nowadays modern economic systems operate using computers. Cyber fraudstersaim to target computer networks of economic and financial institutions such as stock markets, payment systems, and banks to loot money or block users from accessing their own funds.
Surprise Attacks:
These are the cyber identical of attacks like Pearl Harbor and 9/11. The aim of this kind of attack is to carry out a massive attack that the enemy isn’t expecting, which resultsin a defense break-down. This isperformed to set the ground for a physical attack in the context of hybrid warfare.
Examples of some well-publicized examples of cyber warfare in recent times:
Stuxnet Virus:
Stuxnet was a type of digital worm that attacked the Iranian nuclear program. It is one of the most polished cyber-attacks in history. The malware spread through infected Universal Serial Bus devices and earmark data acquisition and supervisory control systems. According to most research and media reports, this attack seriously damaged Iran’s ability to manufacture nuclear weapons.
Sony Pictures Hack:
An attack on Sony Pictures after the release of the film "The Interview", portrays the negative role of Kim Jong Un. The attack is accredited to North Korean government hackers. The FBI found a likeness to former malware attacks by North Koreans, which includes code, encryption algorithms, and data deletion mechanisms.
Bronze Soldier:
In 2007, Estonia moves a statue associated with the Soviet Union, the Bronze Soldier, from the center of its capital Tallinn to a military cemetery near the city. Estonia faced a number of notable cyber-attacks in the following months. Estonian government websites, media outlets, and banks were in excess with traffic in massive denial of service (DoS) attacks and subsequently were taken offline.
Fancy Bear:
CrowdStrike affirms that the Russian marshal cybercrime group Fancy Bear targeted Ukrainian rocket forces and artillery between 2014 and 2016. The malware was spread through an infected Android application used by the D-30 Howitzer artillery unit to manage targeting data. Ukrainian officers vastly use the app, which contained the X-Agent spyware. This is considered one of the most highly successful attacks, destructing over 80% of Ukraine’s D-30 Howitzers.
Enemies of Qatar:
Elliott Broidy, an American Republican fundraiser, sued the government of Qatar in 2018, blaming it for stealing and leaking his emails in an attempt to discredit him. The Qataris supposedlysaw him as ahurdle to improving their standing in Washington.According to the lawsuit, the brother of the Qatari Emir was supposed to have organized a cyber warfare campaign, along with others in Qatari leadership. 1,200 citizens were targeted by the same cybercriminals, with many of these being known "enemies of Qatar", which includes senior officials from Egypt, Saudi Arabia, the United Arab Emirates, and Bahrain.
How to combat cyber warfare threat:
The Cooperative Cyber Defense Center of Excellence (CCD COE) has published the Tallinn Manual, a textbook that states rare but serious cyber threats. This manual explains when cyberattacksbreach international law and how countries may respond to such breaches.The best possible way to evaluate a nation’s preparedness for cyber warfare is to organize a real-life exercise or simulation, also known as a cyber wargame.A wargame can test how governments and private organizations react to a cyber warfare scenario, reveal gaps in the defense, and revamp cooperation between entities. Significantly, a wargame can facilitate the defenders to learn how to act quickly to protect vital infrastructure and save lives.
Cyber wargames can support cities, states, or countries improve preparedness for cyber warfare by:
- Testing different situations: For exampledigging out attacks in early stages, or mitigating risks after the critical framework has already been compromised.
- Testing unusual scenarios: Attacks never occurred "by the book". By establishing a red team that reacts as the attackers and tries to find innovative ways to breach a target system, the defenders can learn how to mitigate real threats.
- Division of labor and cooperation mechanisms: Cyberwarfare requires many smart brains from different organizations and government units to collaborate. A cyber wargame can bring together those intelligent minds, who may not know each other, but help them decide how to work as a team in the event of a crisis.
- Improving policies: Governments may initiate cyber warfare policies, but need to test them in practice. A cyber wargame can test the efficacy of policies and provide an opportunity for improving them.
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















