CCNA or Cisco Certified Network Associate is an Information Technology certification from CISCO, the American multinational and leader in IT, networking and cyber security solutions. CCNA certification is an associate level Cisco Career Certification.
The content of the exams is propriety.
The CCNA certification is valid for a period of 3 years. Renewal of the certification requires the present holders to register and pass the same or higher level Cisco re certification exam every 3 years.
The topics include connecting to a WAN, implementing network security, network types, network media, routing and switching fundamentals, the TCP/IP and OSI models, IP addressing, WAN technologies, operating and configuring IOS devices, extending switched networks with VLANs, determining IP routes, managing IP traffic with access lists, and establishing point-to-point connections.
Why learn CCNA Essentials?
Imparts in depth knowledge of
Networking.
Provides essential
Networking Knowledge
for
Ethical Hacking.
Duration
40 hours - 2 classes per week
Eligibility
10+2 along with a basic aptitude and understanding of computer hardware knowledge.
Course Fees
Class Room Training
Rs.13,000/-
Inclusive of all taxes
Online Training
Rs.23,000/-
Rs.13,000/-
Inclusive of all taxes
What You Will Get?
40 Hours
in-depth training by Cisco Certified Trainer
Study Materials
CCNA Essentials
Certificate of Completion after examination and alumni status
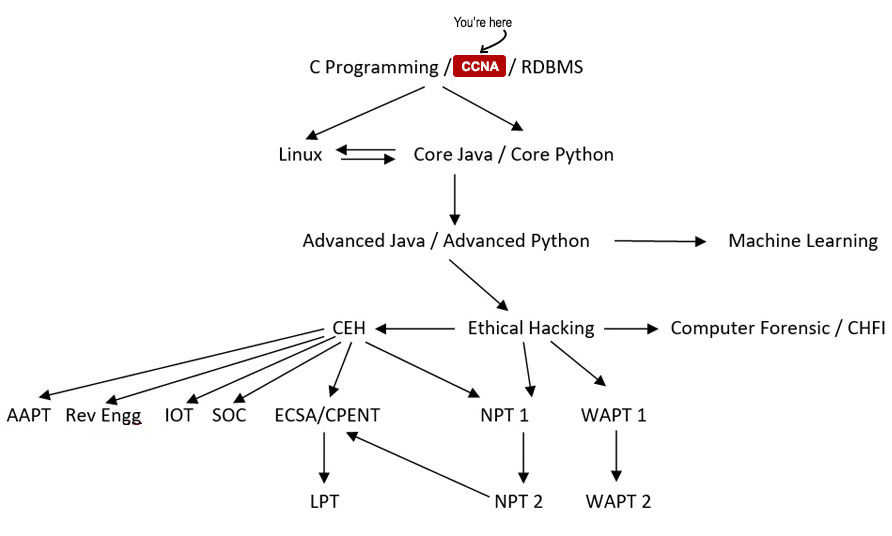
Your Course Path
Course Details
- Essential to understand ethical hacking
- Prerequisite for CEH
- What is Networking? (Day 1)
- What is Internet? (Day 1)
- LAN, MAN, WAN, Topology (Day 1)
- Bits,Bytes and Octets (Day 1)
- What is Packet Tracer? (Day 1)
- Packet Tracer Installation (Day 1)
- What is OSI Layer (Day 2)
- Explain 7 layers (Day 2)
- Brief explaination for TCP Header (Day 2)
- Brief explaination for 3 way Handshake (Day 2)
- Comparison between OSI and TCP/IP Model (Day 2)
- Introduction to IP and MAC Address (Day 3)
- Use of IP and MAC Address (Day 3)
- What is OUI and DI? (Day 3)
- IANA, ICANN (Day 3)
- IPv4(Classful Addressing) (Day 3)
- Class A,B,C,D,E (Day 3)
- Public IP Private IP (Day 3)
- Loopback Address and APIPA (Day 3)
- Default Subnet Mask (Day 3)
- What is Subnetting? (Day 4)
- What is FLSM and VLSM? (Day 4)
- What is Subnet Mask? (Day 4)
- What is CIDR? (Day 4)
- Calculate FLSM for Class C Address (Day 4)
- Calculate VLSM for 4-6 Network Requirement with variable Host (Day 4)
- How to use Packet Tracer? (Day 5)
- Network setup using 2 pc and switch (Day 5)
- Router Components and Different Modes (also talk about router memory and how router saves configurations) (Day 5)
- Router Configuration (including Router password set and bypass) (Day 5)
- Network setup using 2 pc, switch and router (Day 5)
- DHCP Configuration using 4pcs(Classful & Classless) (Day 5)
- What is Telnet, ssh, ftp/tftp (Day 5)
- Configure SSH with security in Router (Day 5)
- What is Switching? (Explain ARP as well) (Day 6)
- What is VLAN? (Day 6)
- Different Modes(Access, Dynamic and Trunk) (Day 6)
- Configure VLAN (2-3 VLANS) (Day 6)
- Configure Intervlan Routing(Using Router with 2 interfaces, Router on Stick) (Day 6)
- What is VTP? (Day 7)
- Configure VTP(Server, Client, Transparent Mode) with 4 Switches (Day 7)
- What is Port Security? (Day 8)
- Configure Port Security(Restrict, Protect, Shutdown Mode)(Sticky,Dynamic MAC Address, Maximum Address) (Day 8)
- What is DHCP Snooping? (Day 8)
- Configure DHCP Snooping with 2 Servers(DHCP Configured inside) and 4 PCs (Day 8)
- What is Routing? (also discuss CDP, LLDP) (Day 10)
- What is IGP and EGP? (Day 10)
- Explain Different Vectors and Metrics (Day 10)
- Different protocols under IGP and EGP (Day 10)
- What is AS number and AD value? (Day 10)
- STATIC routing, Default Routing (Day 10)
- Dynamic Routing (Intro) (Day 10)
- Configure and verify single area and Multi area OSPFv2 (Day 11)
- Neighbor adjacencies (Day 11)
- Point to point (Day 11)
- DR/BDR selection (Explaination) (Day 11)
- Router ID (Day 11)
- What is and use of ACL? (Day 12)
- What is Standard and Extended ACL? (Day 12)
- Standard(Name,Number) ACL Configuration with 2 Routers blocking/allowing a network/host for hosts/network (Day 12)
- Extended(Name,Number) ACL Configuration with 2 Routers blocking/allowing a network/hosts for ICMP, HTTP, HTTPS, FTP, TELNET (Day 12)
- What is NAT? Different Types of NAT (Day 13)
- Configure Static NAT (Only Inside Rule) with two router (Day 13)
- Configure Dynamic NAT (Only Inside Rule) with two router using Pool and Interface (Day 13)
- What is PAT? (Day 13)
- Configure PAT (Only Inside Rule) with two router using Pool and Interface (Day 13)
- WLAN 4 way handshake (Day 14)
- Describe wireless security protocol (WPA,WPA2, WPA3) (Day 14)
- Configure and verify WLAN within the GUI using WPA2 PSK (Day 14)
- Explain Different WAN Technologies(Leased Line, Circuit Switching, Packet Swtching) (Day 16)
- What is Point to Point and Multiaccess Link? (Day 16)
- Explain and Configure different Point to Point Link encapsulation technology(HDLC, PPP --> PAP, CHAP) (Day 16)
- Why IPv6? (Day 17)
- How to write IPv6 Address? (Day 17)
- Different Types of IPv6 Address(Unicast, Multicast, Anycast) (Day 17)
- Different Types of Unicast Address(Global Unicast, Unique local, link local) (Day 17)
- Configure and Verify IP address on Router with 2PCs (Day 17)
- Configure and Verify Static Autoconfig Address (Day 17)
- Configure and Verify Static Routing with 2 Routers (Day 17)
- Define ICMP, DNS (Day 18)
- Explain AAA and the working (Day 18)
- Discuss the differences between TACACS+ and RADIUS (Day 18)
- What is SNMP? Different SNMP Version (Day 19)
- What is MIB,OID? What is SNMP Agent and Manager? (Day 19)
- Different SNMP Queries (Day 19)
- What is DMZ? Why is used? (Day 19)
- Discuss How DMZ are formed? (Day 19)
- Configure SNMP in Packetracer (Day 19)
- What is Proxy? Why it is used? (Day 20)
- What is VPN? (Day 20)
- Different Types of VPN(Site-to-Site, Remote-access) (Day 20)
- Different VPN Technologies(GRE, DMVPN, IPSEC) (Day 20)
- Configure GRE in Packet tracer (Day 20)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensic - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
In order to maintain ultimate cyber security for corporate networking component is the most important aspect of IT infrastructure. Thus the demand for trained CCNA practitioners is soaring highest in the market for IT jobs.
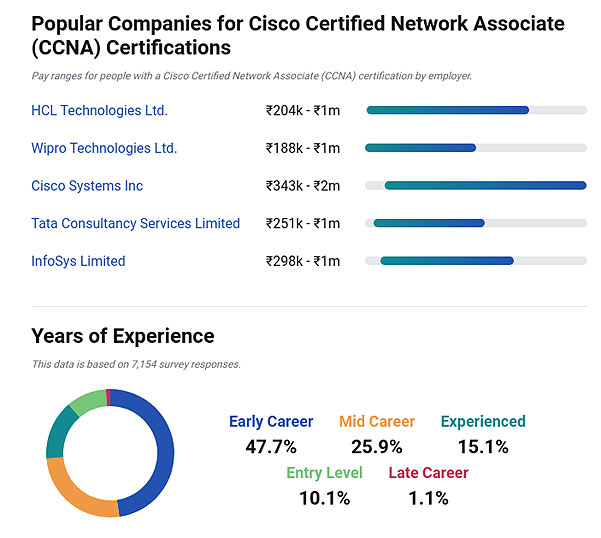
One of those industrial sectors where CCNA is the most sought after IT security service is the Medical. That is because it is important to secure the patient report and associated medical details from being seized by hackers. Cyber Security being a major threat in fields of human activities the demand for CCNA certified security professionals is the highest. However prospects of a CCNA professional depends mainly on two factors namely work experience and job title.
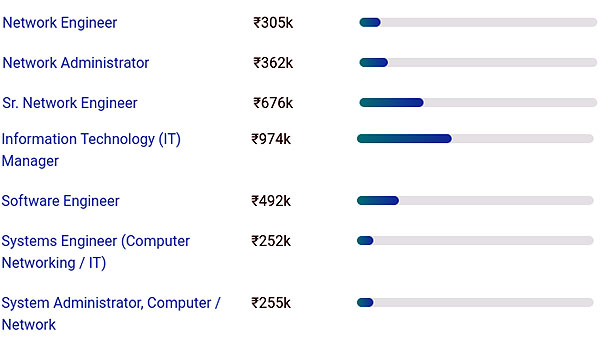
The various titles that a CCNA processional holds are as follows:
| Network Engineer | Senior Network Engineer | Network Administrator |
| IT Manager | Systems Administrator | |
| Mobile Lead Software Engineer | Mobile Developer | IT Director |
| System Engineer |
Out of all the varied titles of CCNA the position which commands the highest financial compensation is the managerial one which CCNA is a confirmed catalyst to reach.
Two important specializations of CCNA is ‘routing’ and ‘switching’. Job opportunities for both are increasing manifold owing to growing network and infrastructural complexities which demand trained individuals who can maintain complicated and critical hardware required to support the same. But these two specializations are at present the most in demand and financially alluring areas of CCNA.
Here is a pictorial representation of a CCNA career in India.
FAQs
The topics include connecting to a WAN, implementing network security, network types, network media, routing and switching fundamentals, the TCP/IP and OSI models, IP addressing, WAN technologies, operating and configuring IOS devices, extending switched networks with VLANs, determining IP routes, managing IP traffic with access lists, and establishing point-to-point connections.
The course lasts for 40 hours with 2 classes per week.
The course is primarily based on practical sessions with an apt degree of theoretical classes.
10+2 along with a basic aptitude and understanding of computer hardware knowledge.
In order to maintain ultimate cyber security for corporate networking component is the most important aspect of IT infrastructure. Thus the demand for trained CCNA practitioners is soaring highest in the market for IT jobs for data security. Hence plush security jobs in IT departments of corporate houses are the alluring future of CCNA aspirants.
You can upgrade yourself in CISCO approved security skill development courses like CCNP, CCIE etc.
Course Fees
Rs.23,000/-Rs.13,000/-
Inclusive of all taxes
Batches
Weekday Batches for Bhubaneswar Center:
Jan, 2026
Jan, 2026
Mar, 2026
Weekend Batches for Kolkata Center:
Jan, 2026
Jan, 2026
Mar, 2026
Member of: