A Certified Ethical Hacker is a skilled professional with a global certification from EC-Council, who understands and knows how to look for weaknesses and vulnerabilities in target systems (firewall, server, network, software, mobile app, etc); and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). Being accredited to the International Council of Electronic Commerce Consultants, popularly known as the EC Council, which is the owner and creator of the Certified Ethical Hacker or the CEH along with many cyber security credentials, it is one of the most sought after GLOBAL certification among security professionals all over the world. The CEH certifies individuals in the specific network security discipline of Ethical Hacking from a vendor-neutral point of view.
Certified Ethical Hacker CEH v11 will teach you the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organization.
What's new in CEH v11?
With the CEH v11 we've taken all that the CEH already is and added more to it, to make it even better, more advanced, more detailed, and yet succinct.
- Cloud: Container Technology, Docker, Kubernetes
- Parrot Os: WifiPhisher, AnonSurf
- Operation Technology: ICS, SCADA, PLC; HML based attacks, Side-Channel attacks
- WPA3: WP3 Encryption and cracking
- Malware Reverse Engineering: Static and Dynamic Malware Analysis
- Emerging Attack Vectors: Fileless malware, targeted ransomware, Web API threats and Web Shell
- Hacking Challenges On Steroids
Why Become A Certified Ethical Hacker (CEH)?
The EC-Council Certified Ethical Hacker (CEH) course helps you to earn
Advanced Security
Skill-sets
in the worldwide information security domain.
The CEH training & certification course is one of the
Most Trusted &
Popular
ethical hacking training program.
Nowadays IT departments have made
CEH Certification
a compulsory qualification for security-related posts.
CEH-certified professionals typically earn
Higher Salaries
than their non-certified colleagues.
Highlights of some of what sets CEH v11 apart from the rest:

Duration
40 hours - 2 classes per week
Eligibility
- Basic Knowledge of Software, Database and Networking
- If you do not have the above knowledge, please complete our "INDUSTRY READY" Courses to be eligible -
Industry Ready C Programming
Industry Ready Data Structure
Industry Ready RDBMS
Course Fees
Class Room Training
Rs.34,000/-
Inclusive of all taxes
Online Training
Rs.44,000/-Rs.34,000/-
Inclusive of all taxes
What You Will Get?
40 Hours
in-depth training by best faculties from cyber security industry
Study Materials
and examination voucher
CEH Certificate
of completetion after examination and alumni status
Introducing The Break-The-Code Challenge With CEH v11
24 incredible hacking challenges across 4 levels of complexity that cover 18 attack vectors, including the OWASP Top 10 as a part of our Gamification Platform are now included as part of CEH v11!
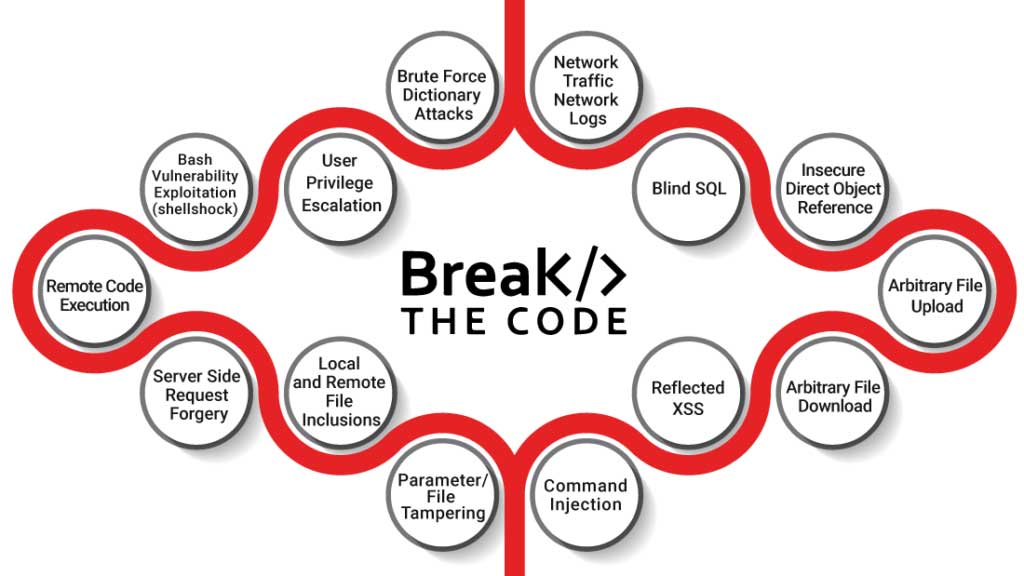
Course Benefits:
- The certification is provided by EC-Council, one of leading certification authorities in the field of cyber security. The certificate is valid in India and abroad as well.
- This course introduces you to all the techniques and different kind of attacks as well as how to defend these attacks to make your website/network more secure.
- Compared to other courses in cyber security EC-Council’s CEH is a course which provides vast in-depth understanding of how things are happening with numerous labs and is mainly focused on practical knowledge rather than just being theoretical. To know more about the course please click www.eccouncil.org/programs/certified-ethical-hacker-ceh/
- After completing this course, you will be able to successfully identify, stop and prevent latest cyber attacks.
Additional Benefits Included With CEH v11 Worth $1319
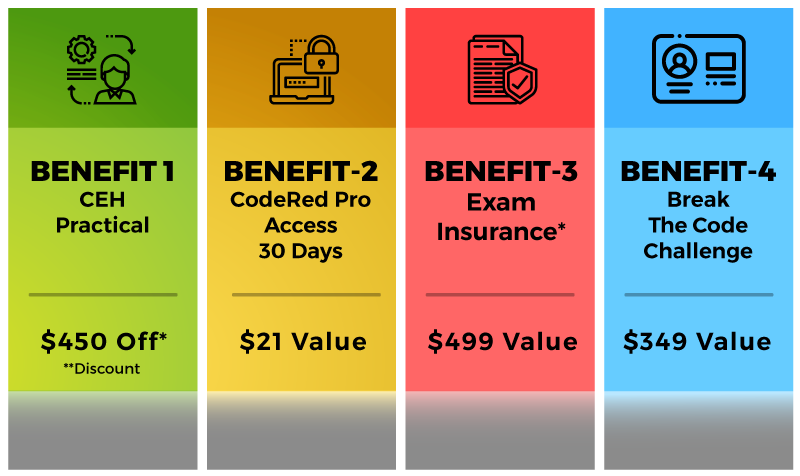
*For promo Terms and Conditions contact an Authorized Training Center/Re-seller/Distributor
**Discount – This represents the discount that will be provided from the list price on the EC-Council Store
***Offer valid from September 16 to October 31, 2020
Course Details
- This course is designed as per latest EC-Council’s CEH exam syllabus (CEH v11).
- The code for the CEH exam is 312-50 (ECC EXAM), 312-50 (VUE).
- It is a multiple choice examination at the end of the course.
- Course duration is 40 hours.
- Main focus will be on both theoretical and practical parts, with hands on experience of most of the attacks.
- Information Security Overview (Day 1)
- Information Security Threats and Attack Vectors (Day 1)
- Hacking Concepts (Day 1)
- Ethical Hacking Concepts (Day 1)
- Information Security Controls (Day 1)
- Penetration Testing Concepts (Day 1)
- Information Security Laws and Standards (Day 1)
- Footprinting Concepts (Day 2)
- Footprinting through Search Engines (Day 2)
- Footprinting through Web Services (Day 2)
- Footprinting through Social Networking Sites (Day 2)
- Website Footprinting (Day 2)
- Email Footprinting (Day 2)
- Competitive Intelligence (Day 2)
- Whois Footprinting (Day 2)
- DNS Footprinting (Day 2)
- Network Footprinting (Day 2)
- Footprinting Through Social Engineering (Day 2)
- Footprinting Tools (Day 2)
- Footprinting Countermeasures (Day 2)
- Footprinting Penetration Testing (Day 2)
- Network Scanning Concepts (Day 3)
- Scanning Tools (Day 3)
- Scanning Techniques (Day 3)
- Scanning Beyond IDS and Firewall (Day 3)
- Banner Grabbing (Day 3)
- Draw Network Diagrams (Day 3)
- Scanning Pen Testing (Day 3)
- Enumeration Concepts (Day 4)
- NetBIOS Enumeration (Day 4)
- SANP Enumeration (Day 4)
- LDP Enumeration (Day 4)
- SMTP and DNS Enumeration (Day 4)
- Other Enumeration Techniques (Day 4)
- Enumeration Countermeasures (Day 4)
- Enumeration Pen Testing (Day 4)
- Vulnerability Assessment Concepts (Day 5)
- Vulnerability Assessment Solutions (Day 5)
- Vulnerability Scoring Systems (Day 5)
- Vulnerability Assessment Tools (Day 5)
- Vulnerability Assessment Reports (Day 5)
- System Hacking Concepts (Day 6)
- Cracking Passwords (Day 6)
- Escalating Privileges (Day 6)
- Executing Applications (Day 6)
- Hiding Files (Day 6)
- Covering Tracks (Day 6)
- Penetration Testing (Day 6)
- Malware Concepts (Day 7)
- Trojan Concepts (Day 7)
- Virus and Worm Concepts (Day 7)
- Malware Analysis (Day 7)
- Countermeasures (Day 7)
- Anti-Malware Software (Day 7)
- Malware Penetration testing (Day 7)
- Sniffing Concepts (Day 8)
- Sniffing Technique: MAC Attacks (Day 8)
- Sniffing Technique: DHCP Attacks (Day 8)
- Sniffing Technique: ARP Poisoning (Day 8)
- Sniffing Technique: Spoofing Attacks (Day 8)
- Sniffing Technique: DNS Poisoning (Day 8)
- Sniffing Tools (Day 8)
- Countermeasures (Day 8)
- Sniffing Detection Techniques (Day 8)
- Sniffing Pen Testing (Day 8)
- Social Engineering Concepts (Day 9)
- Social Engineering Techniques (Day 9)
- Insider Threats (Day 9)
- Impersonation on Social Networking Sites (Day 9)
- Identity Theft (Day 9)
- Countermeasures (Day 9)
- Social Engineering Pen Testing (Day 9)
- DoS/DDos Concepts (Day 10)
- DoS/DDos Attack Techniques (Day 10)
- Botnets (Day 10)
- DDoS Case Study (Day 10)
- DoS/DDos Attack Tools (Day 10)
- Countermeasures (Day 10)
- DoS/DDos Protection Tools (Day 10)
- DoS/DDos Penetration Testing (Day 10)
- Session Hijacking Concepts (Day 11)
- Application Level Session Hijacking (Day 11)
- Network Level Session Hijacking (Day 11)
- Session Hijacking Tools (Day 11)
- Countermeasures (Day 11)
- Penetration Testing (Day 11)
- IDS, Firewall and Honeypot Concepts (Day 12)
- IDS, Firewall and Honeypot Solutions (Day 12)
- Evading IDS (Day 12)
- Evading Firewalls (Day 12)
- IDS/Firewall Evading Tools (Day 12)
- Detecting Honeypots (Day 12)
- IDS/Firewall Evasion Countermeasures (Day 12)
- Penetration Testing (Day 12)
- Web Server Concepts (Day 13)
- Web Server Attacks (Day 13)
- Web Server Attacks Methodology (Day 13)
- Web Server Attack Tools (Day 13)
- Countermeasures (Day 13)
- Patch Management (Day 13)
- Web Server Security Tools (Day 13)
- Web Server Pen Testing (Day 13)
- Web App Concepts (Day 14)
- Web App Threats (Day 14)
- Hacking Methodology (Day 14)
- Web App Hacking Tools (Day 14)
- Countermeasures (Day 14)
- Web App Security Testing Tools (Day 14)
- Web App Pen Testing (Day 14)
- SQL Injection Concepts (Day 15)
- Types of SQL Injection (Day 15)
- SQL Injection Methodology (Day 15)
- SQL Injection Tools (Day 15)
- Evasion Techniques (Day 15)
- Countermeasures (Day 15)
- Wireless Concepts (Day 16)
- Wireless Encryption (Day 16)
- Wireless Threats (Day 16)
- Wireless Hacking Methodology (Day 16)
- Wireless Hacking Tools (Day 16)
- Bluetooth Hacking (Day 16)
- Countermeasures (Day 16)
- Wireless Security Tools (Day 16)
- Wireless Pen Testing (Day 16)
- Mobile Platform Attack Vectors (Day 17)
- Hacking Android OS (Day 17)
- Hacking iOS (Day 17)
- Mobile Spyware (Day 17)
- Mobile Device Management (Day 17)
- Mobile Security Guidelines and Tools (Day 17)
- Mobile Pen Testing (Day 17)
- IoT Concepts (Day 18)
- IoT Attacks (Day 18)
- IoT Hacking Methodology (Day 18)
- IoT Hacking Tools (Day 18)
- Countermeasures (Day 18)
- IoT Pen Testing (Day 18)
- Cloud Computing Concepts (Day 19)
- Cloud Computing Threats (Day 19)
- Cloud Computing Attacks (Day 19)
- Cloud Security (Day 19)
- Cloud Security Tools (Day 19)
- Cloud Penetration Testing (Day 19)
- Cryptography Concepts (Day 20)
- Encryption Algorithms (Day 20)
- Cryptography Tools (Day 20)
- Public Key Infrastructure (PKI) (Day 20)
- Email Encryption (Day 20)
- Disk Encryption (Day 20)
- Cryptanalysis (Day 20)
- Countermeasures (Day 20)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensics - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »CEH Exams
Prove Your Skills and Abilities With Online, Practical Examinations.

Certified Ethical Hacker (CEH) Certification
The CEH exam is a 4-hour exam with 125 multiple choice questions. This knowledge based exam will text your skills in Information Security Threats and Attack Vectors, Attack Detection, Attack Prevention, Procedures, Methodologies and more!
Pay & Book Your Seat »CEH Practical Certification
- Port scanning tools (e.g., Nmap, Hping)
- Vulnerability detection
- Attacks on a system (e.g., DoS, DDoS, session hijacking, webserver and web application attacks, SQL injection, wireless threats)
- SQL injection methodology and evasion techniques
- Web application security tools (e.g., Acunetix WVS)
- SQL injection detection tools (e.g., IBM Security AppScan)
- Communication protocols
- Scanning (e.g., Port scanning, banner grabbing, vulnerability scanning, network discovery, proxy chaining, IP spoofing)
- Cryptography
- Cryptography toolkit (e.g., OpenSSL)
- Web server attack methodology
- Operating environments (e.g., Linux, Windows, Mac)
- Web application hacking methodology
- Encryption algorithms
- System hacking (e.g., password cracking, privilege escalation, executing applications, hiding files, covering tracks)
- Vulnerability scanning
- Exploitation tools
- Application/file server
- Database structures
- Wireless and Bluetooth hacking methodology
- Wireless terminologies
- Wireless encryption
- Network/wireless sniffers (e.g., Wireshark, Airsnort)
- Malware (e.g., Trojan, virus, backdoor, worms)
- Botnet
- Malware analysis
- Network sniffing
- Backups and archiving (e.g., local, network)
- Data analysis
- Log analysis tools
- Cryptanalysis tool (e.g., CrypTool)
This is the next step to become a CEH Master after you have achieved your CEH certification. Within CEH Practical you will have a limited amount of time to complete 20 challenges testing your skills and proficiency in a performance-based cyber range. This exam is NOT a simulation and incorporates a live corporate network of VM’s and applications with solutions to uncover vulnerabilities.
CEH (Practical) »CEH Master
Upon Completing the CEH (Master) program, consisting of CEH and CEH (Practical), the CEH (Master) designation is awarded. Once you have achieved both the CEH and CEH Practical certifications you are now a CEH Master. CEH Masters have shown proficiency at a master level in the Knowledge, Skills, and abilities of Ethical Hacking with a total 6 hours of testing to prove their competency.
CEH (Master) »Ratings & Reviews
Job Prospects & Job Sources
The CEH v11 course opens up numerous career advancement opportunities, it helps to prepare you for different roles in infosec domain like computer network defence analyst, infrastructure support, infosec incident responder, infosec auditor, intrusion analyst, security manager, and other related high-profile roles.
The following are the career prospects of CEH enumerated.
Cyber security is a blooming field
Cyber security is a blooming field with excellent potential in the IT market, and is a very important aspect of any company.
The rising demands for cyber security
The demands for cyber security is rising exponentially both in Indian market as well as abroad.
United States faced a shortfall of cyber security professionals
According to Cyber Seek, an initiative funded by the National Initiative for Cyber Security Education (NICE), the United States faced a shortfall of almost 314,000 cyber security professionals as of January 2019. Same can be said for India as well.
Course designed for cybercrime department or any Government organization
This course is not only for IT sector but also for professionals who are in the cybercrime department or any Government organization dealing with cybercrimes, espionage or cyber security as a whole.
According to NASSCOM India requires 77,000 ethical hackers
As according to a study by NASSCOM India requires 77,000 ethical hackers every year out of which the job market can only provide 15000. The demand being way more than the supply Ethical Hacking is one of the most sought after and promising professions at the moment.
Average earning of a Certified Ethical Hacker
Financially also this profession is paying and secure enough. In India on an average a certified ethical hacker earns an average salary of Rs 367,249 per year which increases with experience cumulatively upto more than 15 lakh per year.
| Designation | Salary in Rs. |
|---|---|
| Security Analyst | 3.7 lakhs |
| Information Security Analyst | 4.3 lakhs |
| Certified Ethical Hacker (CEH) | 3.5 lakhs |
| Security Consultant (Computing / Networking / Information Technology) | 5.5 lakhs |
| Information Security Manager | 12 lakhs |
| Experience | Salary in Rs. |
|---|---|
| Less than 1 year | 3 lakhs |
| 1-4 years | 3.8 lakhs |
| 5-9 years | 7.7 lakhs |
| 10-19 years | 5.5 lakhs |
| 20 years and more | 14.4 lakhs |
| Employers | Salary in Rs. |
|---|---|
| Tata Consultancy Services Limited | 1.5 to 9 lakhs |
| Wipro Technologies Limited | 2.5 to 14.5 lakhs |
| International Business Machines (IBM) Corp. | 3 to 6 lakhs |
| EY (Ernst & Young) | 2.4 to 6 lakhs |
| HCL Technologies Ltd. | 2 to 7 lakhs |
FAQs
The CEH course is the fundamental curriculum on cyber security. It is designed as per latest EC-Council’s CEH exam syllabus (CEH v11). The main focus is on both theoretical and practical parts, with hands on experience of most of the attacks.
40 hours
The main focus of this course will be on both theoretical and practical parts, with hands on experience of most of the attacks, depending upon the particular student.
Complete 12th board exam and basic networking knowledge or CCNA.
After the course you are eligible to apply in the cyber security domain of any corporate house.
After the course you can enroll yourself for customized advanced courses like NPT1, WAPT1, NPT2 and WAPT2 from ISOEH after fulfilling its prerequisites.
Enroll Now
Fields marked with * are mandatory.
Course Fees
Rs.44,000/-Rs.34,000/-
Inclusive of all taxes
Batches
Weekday Batches:
Oct, 2020
Oct, 2020
Dec, 2020
Oct, 2020
Oct, 2020
Dec, 2020
Oct, 2020
Oct, 2020
Dec, 2020
Weekend Batches:
Oct, 2020
Oct, 2020
Dec, 2020
Oct, 2020
Oct, 2020
Jan, 2021
Member of: