What is C|EH v13?
The CEH v13 introduces a comprehensive 'Learn | Certify | Engage | Compete' framework, designed to equip you with advanced ethical hacking skills. The course integrates the latest tools and technologies to keep you updated with industry trends.
You can achieve the CEH certification through our flexible iLearn platform, featuring guided, self-paced learning with one-on-one instructor support, ensuring thorough understanding and practical experience through extensive labs.
Act Now — Cyber Threats Won't Wait!
Become a Certified Ethical Hacker and secure your place in one of the fastest-growing fields worldwide.
- World's Leading Ethical Hacking Certification
- Master Advanced Cyber Techniques and the 5 Phases of Ethical Hacking
- Globally Recognized—Open Doors to International Cyber Careers
- Get Hands-On with Latest Tools in CyberQ™ Labs
- Flexible Learning Options: Live, Online, or Hybrid
How C|EH v13 Empowers You?
AI-Powered Certification
The first ethical hacking certification utilizing AI technology
Hands-On Labs
Real-world scenarios to master advanced hacking tools
Boost Efficiency by 40%
AI-driven techniques streamline cyber defence
Updated Curriculum
Learn the latest attack techniques, trends, and countermeasures
Real-World Mastery
Global hacking competitions to showcase your skills
What's New in C|EH v13?
Our exclusive learning program will give you the ultimate hands-on hacking experience with our new Learn | Practice | Certify | Compete framework. CEH v13 brings you cutting-edge commercial hacking tools, techniques, and methodologies used by top professionals. Don't miss out on mastering 220+ immersive labs and staying ahead of the curve with the latest hacking trends.
Learn
Gain Skills
- 20 modules
- 2500+ pages of student manual
- 2000 pages of lab manual
- Over 221 hands-on labs to practice attack vectors and hacking tools
- AI integrated skills in the 5 phases of the ethical hacking framework
- Hacking AI system, based on the Top 10 OWASP vulnerabilities
- Over 4000 hacking and security tools
- Learn how to hack multiple operating systems (Windows 11, Windows servers, Linux, Ubuntu, Android)
- More than 50% of training time is dedicated to labs
Certify
Gain Experience
Knowledge-Based Exam
(ANAB ISO 17024 and US DoD 8140)
- 4 hours
- 125 multiple-choice questions
Practical Exam
(ANAB ISO 17024 and US DoD 8140)
- 6 hours
- 20 real scenario based questions
Engage
Gain Recognition
- 4000 hacking tools
- 550 attack techniques
- Conduct a real-world ethical hacking assignment
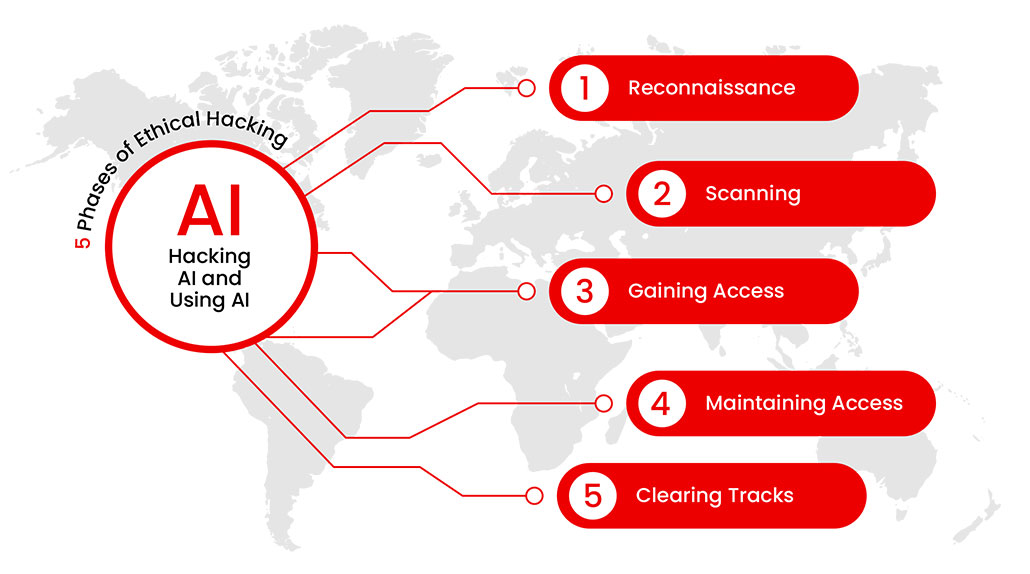
- Apply the 5 phases
- Reconnaissance
- Scanning
- Gaining access
- Maintaining access
- Covering your tracks
Compete
Gain Respect
- New challenges every month
- 4-hour CTF competition
- Compete with your peers worldwide
- Hack your way to the top of the leaderboard
- Focus on new attack vectors
- Exploit emerging vulnerabilities
- Challenges include:
- Ransomware
- Web app hardening
- Unpatched software
- System hacking
- Service exploitation
- Incident response
- Forensic analysis
- Web app hacking and pen testing
- Reverse engineering
- Cryptography
- Encryption
- Hacking cloud networks
- ICS/SCADA
Enter the Hackerverse™ With the C|EH v13 Enhance Your Ethical Hacking Career
Step 1: Learn
CEH offers a balanced blend of knowledge-based training and hands-on labs using real-world scenarios and is powered by AI.
What’s covered
- 100% virtualization with full access to pre-configured targets, networks, and attack tools
- Pre-configured vulnerable websites
- Vulnerable, unpatched operating systems
- Fully networked environments
- Wide range of target platforms to hone your skills
- 550 attack techniques covered
- Objective-oriented flags for critical thinking and applied knowledge assessment
- Cloud-based cyber range
- Practice every course objective on live machines and vulnerable targets.
- With access to over 4,000 hacking tools and various operating systems, you’ll gain practical experience with industry-standard security tools, the latest vulnerabilities, and common operating systems.
- Our web-accessible range allows you to learn and practice from anywhere.
Step 2: Certify
Upon completing the training, you can attempt both of our exams to demonstrate your skills and earn the CEH Master certification:
- Take the knowledge exam
- Complete the practical exam
The knowledge exam
This 4-hour exam with 125 multiple-choice questions will test your skills in:
- Information security threats and attack vectors
- Attack detection
- Attack prevention
- Procedures
- Methodologies and more!
The practical exam
In 6 hours you’ll complete 20 real-world challenges to test your proficiency. You’ll do this by incorporating a live corporate network of VMs and applications with ethical hacking solutions to uncover any vulnerabilities.
Step 3: Engage
CEH helps you develop real-world experience in ethical hacking through hands-on practice in a Cyber Range.
This 4-phase engagement requires critical thinking and tests the knowledge and skills you’ve gained through capturing a series of flags in each phase, demonstrating the live application of abilities in a consequence-free environment via EC-Council’s Cyber Range.
Step 4: Compete
Get a year-long access to 12 CTF challenges. Each month presents a different theme and challenge with capture-the-flag style competitions focusing on ethical hackers’ core skills and abilities.
Gain exposure to new tools, focus on new attack vectors, and try to exploit emerging vulnerabilities while gaining continuing education credits and keeping your skills and certifications current.
Climb the leaderboard
These 4-hour challenges are open all month long, allowing you to compete whenever you’re ready. All you need is an internet connection and your hacking expertise – we provide the attack platform, targets, and all the necessary tools and training.

Duration
40 hours - 2 classes per week
Eligibility
- Basic Knowledge of Software, Database and Networking
- If you do not have the above knowledge, please complete our "INDUSTRY READY" Courses to be eligible -
Industry Ready C Programming
Industry Ready Data Structure
Industry Ready RDBMS
What You Will Get?
- Training videos (Guided Video Learning): C|EH is comprehensive. The package comes with over 25 hours of videos from one of our top instructors to guide you through the entire program.
- E-Courseware (Course Material): You will have one-year access to the official e-courseware, containing 4,900+ pages of lab material.
- ILabs (Hands-On Labs): You will also have six months of access to over 220 real-world labs in our online lab environment, EC Council Labs.
- Exam Voucher (Certification): The package includes an EC-Council Certification Exam Voucher with one-year validity, allowing you to take the exam at your own pace.
- Exam Insurance: One exam retake
- Practice Cyber Range
- Entry into Global Competition via CEH Compete
- Ethical Hacking Library
- CEH Practical# Exam Voucher
Important Notice for International Students: The EC-Council global course fee and Exam Voucher fee will depend on the candidate's location and foreign currency exchange rate.
Stay Ahead of Emerging Threats: New Focus Areas and Trends in C|EH v13
Trained to think outside the box with a hacker’s mindset, individuals who pursue the Certified Ethical Hacker (C|EH) v13 thoroughly explore top OWASP attacks, active directory breaches, the vulnerability of traditional encryption to quantum computing, the growing ransomware threat, and other emerging risks, equipping learners with strategies to implement zero trust architecture and other cybersecurity measures. C|EH v13 is comprehensive with the latest knowledge, providing cybersecurity professionals with the skills, tools, techniques, and strategies to defend against trending, modern, and complex cyber threats effectively and efficiently.
- Active Directory Attacks
- Ransomware Attacks and Mitigation
- AI and Machine Learning in Cybersecurity
- Critical Infrastructure Vulnerabilities
- Extended Detection and Response (XDR)
- Quantum Computing Risks and Attacks
- Post-Quantum Cryptography
- Deepfake Threats
- Zero Trust Architecture
- Cloud Security
- IoT Security Challenges
- Critical Infrastructure Vulnerabilities
Who is CEH for?
Cybersecurity professionals
Drive your cybersecurity career forward with CEH, enhanced by the power of AI.
Teams and organizations
Turbocharge your team’s knowledge with certified ethical hacking powered by AI.
Government and military
CEH is trusted and highly valued globally by government departments and defense bodies.
Educators
Create and grow your own cybersecurity courses and programs
Course Details
This course is designed as per latest EC-Council's CEH exam syllabus (CEH v13).
C|EH v13 Exam Information
Certification is awarded when the knowledge exam is passed. In order to achieve CEH Master Level certification, an additional practical exam needs to be taken. This practical exam is optional.
CEH Knowledge-Based Exam
The Knowledge Exam will test your skills in:
- Information security threats and attack vectors
- Attack detention
- Attack prevention
- Procedures Methodologies
Duration: 4 hours
Questions: 125
Delivery: Online via the ECC exam portal
Passing score: In order to maintain the high integrity of our certification exams, EC-Council Exams are provided in multiple forms (i.e., different question banks). Each form is carefully analyzed through beta testing with an appropriate sample group under the purview of a committee of subject matter experts that ensure that each of our exams not only have academic rigor but also have “real world” applicability. We also have a process to determine the difficulty rating of each question. The individual rating then contributes to an overall “Cut Score” for each exam form. To ensure each form has equal assessment standards, cut scores are set on a “per exam form” basis. Depending on which exam form is challenged, cut scores can range from 60% to 85%.
CEH Practical Exam
The practical exam is optional but will reward you with a higher level of certification. It will test your practical skills with:
- Port scanning tools (eg, Nmap, Hping)
- Vulnerability detection
- Attacks on a system (eg, DoS, DDoS, session hijacking, web server and web application attacks, SQL injection, and wireless threats)
- SQL injection methodology and evasion techniques
- Web application security tools (eg, Acunetix WVS)
- SQL injection detection tools (eg, IBM Security AppScan)
- Communication protocols
Duration: 6 hours
Questions: 20 challenges
Delivery: iLabs Cyber Range
Passing score: In order to maintain the high integrity of our certification exams, EC-Council Exams are provided in multiple forms (i.e., different question banks). Each form is carefully analyzed through beta testing with an appropriate sample group under the purview of a committee of subject matter experts that ensure that each of our exams not only have academic rigor but also have “real world” applicability. We also have a process to determine the difficulty rating of each question. The individual rating then contributes to an overall “Cut Score” for each exam form. To ensure each form has equal assessment standards, cut scores are set on a “per exam form” basis. Depending on which exam form is challenged, cut scores can range from 60% to 85%.
Get the AI edge with 20 Power-packed Modules of the CEH v13
Learn the fundamentals and key issues in information security, including the basics of ethical hacking, information security controls, relevant laws, and standard procedures.
Learn how to use the latest techniques and tools for footprinting and reconnaissance, a critical pre-attack phase of ethical hacking.
Learn different network scanning techniques and countermeasures.
Learn various enumeration techniques, including Border Gateway Protocol (BGP) and Network File Sharing (NFS) exploits and associated countermeasures.
Learn how to identify security loopholes in a target organization’s network, communication infrastructure, and end systems. Different types of vulnerability assessment and vulnerability assessment tools are also included.
Learn about the various system hacking methodologies used to discover system and network vulnerabilities, including steganography, steganalysis attacks, and how to cover tracks.
Learn about different types of malware (Trojan, viruses, worms, etc.), APT and fileless malware, malware analysis procedures, and malware countermeasures.
Learn about packet sniffing techniques and their uses for discovering network vulnerabilities, plus countermeasures to defend against sniffing attacks.
Learn social engineering concepts and techniques, including how to identify theft attempts, audit human-level vulnerabilities, and suggest social engineering countermeasures.
Learn about different Denial of Service (DoS) and Distributed DoS (DDoS) attack techniques, plus the tools used to audit a target and devise DoS and DDoS countermeasures and protections.
Learn the various session-hijacking techniques used to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Learn about firewalls, intrusion detection systems (IDS), and honeypot evasion techniques; the tools used to audit a network perimeter for weaknesses; and countermeasures.
Learn about web server attacks, including a comprehensive attack methodology used to audit vulnerabilities in web server infrastructures and countermeasures.
Learn about web application attacks, including a comprehensive hacking methodology for auditing vulnerabilities in web applications and countermeasures.
Learn about SQL injection attack techniques, evasion techniques, and SQL injection countermeasures.
Learn about different types of encryption, threats, hacking methodologies, hacking tools, security tools, and countermeasures for wireless networks.
Learn mobile platform attack vectors, Android and iOS hacking, mobile device management, mobile security guidelines, and security tools.
Learn different types of Internet of Things (IoT) and operational technology (OT) attacks, hacking methodologies, hacking tools, and countermeasures.
Learn different cloud computing concepts, such as container technologies and serverless computing, various cloud computing threats, attacks, hacking methodologies, and cloud security techniques and tools.
Learn about encryption algorithms, cryptography tools, Public Key Infrastructure (PKI), email encryption, disk encryption, cryptography attacks, and cryptanalysis tools.
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensic - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
The following are the career prospects of CEH enumerated.
Cyber security is a blooming field
Cyber security is a blooming field with excellent potential in the IT market, and is a very important aspect of any company.
The rising demands for cyber security
The demands for cyber security is rising exponentially both in Indian market as well as abroad.
United States faced a shortfall of cyber security professionals
According to Cyber Seek, an initiative funded by the National Initiative for Cyber Security Education (NICE), the United States faced a shortfall of almost 314,000 cyber security professionals as of January 2019. Same can be said for India as well.
Course designed for cybercrime department or any Government organization
This course is not only for IT sector but also for professionals who are in the cybercrime department or any Government organization dealing with cybercrimes, espionage or cyber security as a whole.
According to NASSCOM India requires 77,000 ethical hackers
As according to a study by NASSCOM India requires 77,000 ethical hackers every year out of which the job market can only provide 15000. The demand being way more than the supply Ethical Hacking is one of the most sought after and promising professions at the moment.
CEH Skills Mapped To 49 Cybersecurity Job Roles
| 1. Mid-Level Information Security Auditor | 2. Cybersecurity Auditor |
| 3. Security Administrator | 4. IT Security Administrator |
| 5. Information Security Analyst 1 | 6. Infosec Security Administrator |
| 7. Cybersecurity Analyst (Level 1, Level 2, & Level 3) | 8. Network Security Engineer |
| 9. SOC Security Analyst | 10. Network Engineer |
| 11. Senior Security Consultant | 12. Information Security Manager |
| 13. Senior SOC Analyst | 14. Solution Architect |
| 15. Cybersecurity Consultant | 16. Cyber Defense Analyst |
| 17. Vulnerability Assessment Analyst | 18. Warning Analyst |
| 19. All-Source Analyst | 20. Cyber Defense Incident Responder |
| 21. Research & Development Specialist | 22. Senior Cloud Security Analyst |
| 23. Third Party Risk Management | 24. Threat Hunting Analyst |
| 25. Penetration Ttester | 26. Cyber Delivery Manager |
| 27. Application Security Risk | 28. Threat Modelling Specialist |
| 29. Web Application Penetration Testing | 30. SAP Vulnerability Management - Solution Delivery Advisor |
| 31. Ethical Hacker | 32. SIEM Threat Responder |
| 33. Product Security Engineer / Manager | 34. Endpoint Security Engineer |
| 35. Cybersecurity Instructor | 36. Red Team Specialist |
| 37. Data Protection & Privacy Officer | 38. SOAR Engineer |
| 39. AI Security Engineer | 40. Sr. IAM Engineer |
| 41. PCI Security Advisor | 42. Exploitation Analyst (EA) |
| 43. Zero Trust Solutions Engineer / Analyst | 44. Cryptographic Engineer |
| 45. AI/ML Security Engineer | 46. Machine Learning Security Specialist |
| 47. AI Penetration Tester | 48. AI/ ML Security Consultant |
| 49. Crypto Security Consultant |
Average earning of a Certified Ethical Hacker
Financially also this profession is paying and secure enough. In India on an average a certified ethical hacker earns an average salary of Rs 367,249 per year which increases with experience cumulatively upto more than 15 lakh per year.
| Designation | Salary in Rs. |
|---|---|
| Security Analyst | 3.7 lakhs |
| Information Security Analyst | 4.3 lakhs |
| Certified Ethical Hacker (CEH) | 3.5 lakhs |
| Security Consultant (Computing / Networking / Information Technology) | 5.5 lakhs |
| Information Security Manager | 12 lakhs |
| Experience | Salary in Rs. |
|---|---|
| Less than 1 year | 3 lakhs |
| 1-4 years | 3.8 lakhs |
| 5-9 years | 7.7 lakhs |
| 10-19 years | 5.5 lakhs |
| 20 years and more | 14.4 lakhs |
| Employers | Salary in Rs. |
|---|---|
| Tata Consultancy Services Limited | 1.5 to 9 lakhs |
| Wipro Technologies Limited | 2.5 to 14.5 lakhs |
| International Business Machines (IBM) Corp. | 3 to 6 lakhs |
| EY (Ernst & Young) | 2.4 to 6 lakhs |
| HCL Technologies Ltd. | 2 to 7 lakhs |
FAQs
C|EH v13 Program
CEH v13 is a fantastic starting point for those entering the cybersecurity field. However, it’s ideal if you have at least 2 years of IT security experience before diving into the course. If you're a complete beginner, it's recommended to first explore foundational certifications, like our other Cybersecurity Essentials courses, which will equip you with the necessary knowledge to pursue more advanced certifications like CEH, CND, or CHFI. These courses lay the groundwork for tackling CEH v13 and other specialized fields in cybersecurity.
While there are no strict prerequisites for CEH v13, it's highly recommended that candidates have at least 2 years of IT security experience. CEH training involves hands-on tasks like scanning and testing systems, so a basic understanding of IT systems is crucial. For example, you’ll learn to use tools like Nmap for enumerating vulnerabilities, but prior knowledge of networking fundamentals like ports is expected. If you're new to IT, starting with foundational courses, like our Cybersecurity Essentials Series, is recommended before taking CEH v13.
Certified Ethical Hackers (CEH) are cybersecurity professionals hired to identify, evaluate, and fix security vulnerabilities in systems and networks. They use advanced tools and methodologies to ethically hack applications, infrastructures, and organizations to strengthen their defences. With CEH v13, ethical hackers now also leverage AI-driven tools to enhance their abilities in identifying, exploiting, and securing vulnerabilities. This certification equips professionals with the skills to perform both offensive and defensive cyber operations, including threat detection and rapid incident response in real time.
Absolutely! Earning the CEH v13 certification signals to employers that you have the essential knowledge and skills to be a key member of their security team. With cybersecurity job growth projected at 33%, there's a global shortage of qualified professionals, making CEH v13 a highly valuable certification. In fact, 1 in 2 professionals report promotions after obtaining CEH, and 97% say the skills gained in the program helped safeguard their organizations. Additionally, 92% of hiring managers prefer candidates with CEH for ethical hacking roles.
CEH v13 offers over 20 years of proven expertise in ethical hacking, providing an AI-enhanced curriculum to boost efficiency and skills. The program focuses on real-world job roles, using an ANAB-accredited, hands-on approach to deliver industry-relevant content. It’s recognized by governments globally, including the US Department of Defence. EC-Council continually updates the course every 12-18 months to stay ahead of industry trends, ensuring students always have access to the latest tools and techniques.
On average, Certified Ethical Hackers (CEH) in the US earn about $110,757 annually as of September 2024, with top earners making over $137,000. This represents an increase compared to previous years, highlighting the growing demand for cybersecurity professionals. Factors like experience, education, and additional certifications can significantly increase earning potential, with many professionals starting at six-figure salaries. CEH has consistently ranked among the top 5 most in-demand cybersecurity certifications globally, offering lucrative opportunities in the field.
Yes, CEH v13 is one of the most recognized certifications in the cybersecurity field. As of September 2024, over 22,000 job postings on LinkedIn specifically seek candidates with CEH certification. Mapped to 49 job roles across various industries, CEH v13 is highly demanded, far surpassing the popularity of other certifications like SANS GPEN, OSCP, and Pentest+. The CEH certification is a trusted credential for professionals looking to secure roles in cybersecurity.
Yes, CEH v13 is one of the most in-demand cybersecurity certifications globally. It is recognized by employers for its comprehensive ethical hacking skills and is a baseline requirement for many roles, including within the US Department of Defence. CEH v13 is integrated into over 1,200 universities worldwide and maps to 49 job roles across 25+ industries. It is also the first certification to include AI-driven cybersecurity skills, ensuring that professionals are equipped with cutting-edge knowledge for today’s cyber threats.
Obtaining CEHv13 equips you with comprehensive skills across core cybersecurity domains, proving to employers that you’re ready for the job. The ANAB-accredited certification is globally recognized and showcases your expertise in ethical hacking and applying AI to cybersecurity. CEH v13 opens doors to diverse career opportunities, with a strong foundation in ethical hacking that leads to specialized roles. With accessible, affordable training and long-term career value, CEH v13 is a smart investment for anyone serious about advancing in cybersecurity.
The cost of CEH v13 varies based on your preferred training format—whether online self-paced, live online, or in-person training. Pricing can also differ depending on your location and available funding options. To get the most accurate pricing that fits your budget and schedule, it's best to speak with a career advisor, who can also guide you through the available funding plans. CEH v13 offers flexible options to ensure you can pursue the certification that suits your learning needs and financial situation.
CEH v13 training is offered globally in various formats, such as online self-paced, live online, and in-person at Authorized Training Centers (ATCs). The cost varies based on your region, training format, and institution. CEH v13 is designed to be affordable with flexible options, making it accessible to learners worldwide. You can contact an advisor to confirm the pricing for your preferred format or reach out to a local ATC for details on in-person training. Fill out the contact form for immediate assistance.
Certification Questions
To take the CEH Examination, you must first be deemed eligible.
We offer two paths to eligibility:
- Attend official training
- Online learning: Provided by iClass.
- Authorized Training Center (ATC): Located in over 140 countries worldwide.
- College or university: Institutions that are official EC-Council Academia Partners.
- Eligibility application
- Experience-based: If you possess the experience and don’t require training in the exam domains, you can skip the training and go straight to the exam.
- Application process: If you do not attend official training, you will need to apply for exam eligibility.
- After approval: Once your application is processed and approved, EC-Council will work with you to determine the best delivery method for the exam. You may then take the 4-hour certification exam as scheduled.
All candidates attending official training at an EC-Council partner will have direct access to the examination, if they’re deemed eligible.
The exam can be proctored at the training center, online using EC-Council’s remote proctoring service, or at over 4,500 VUE testing centers worldwide.
The CEH exam is a 4-hour, knowledge-based examination with multiple-choice questions. Each question is carefully weighted according to the domain and objective and carries its own cut score.
The CEH exam has multiple forms, each with a rotating set of questions. Because the questions and forms rotate, each exam has a cumulative cut score that is calculated as the aggregate of all question cut scores.
In order to maintain the high integrity of our certification exams, EC-Council Exams are provided in multiple forms (i.e., different question banks). Each form is carefully analyzed through beta testing with an appropriate sample group under the purview of a committee of subject matter experts that ensure that each of our exams not only have academic rigor but also have “real world” applicability. We also have a process to determine the difficulty rating of each question. The individual rating then contributes to an overall “Cut Score” for each exam form. To ensure each form has equal assessment standards, cut scores are set on a “per exam form” basis. Depending on which exam form is challenged, cut scores can range from 60% to 85%.
CEH also offers a 6-hour, 100% practical exam in which students face 20 real-world scenarios.
Candidates can attempt both these exams to get a CEH (Master) credential. Both the above exams are US DoD 8140 approved and ANAB accredited.
Your cut scores and achieved scores will be shown on your exam transcript, which is available immediately after you complete the examination.
EC-Council’s official exam retake policy is available.
Yes, candidates who wish to bypass the official training and jump straight to the exam may apply for eligibility. If granted, you can take the examination directly.
Refer to the question ‘How do I get certified?’ in the FAQs above for the eligibility guidelines and application process.
While we recognize that there are some great resources on YouTube, EC-Council does not publish its official training on YouTube, nor do our authorized partners.
There are many self-published videos that claim to prepare you for the CEH exam. While they may provide valuable information, they are not a substitute for official CEH training and will not be accepted as a valid method of study when applying for exam eligibility.
The most common path students take to prepare for CEH is official training. Certified EC-Council instructors use official EC-Council training materials designed to take you through the various domains covered in the exam.
CEH also includes over 50% hands-on activities in a live Cyber Range, where you practice and apply the knowledge and skills learned in the course against live virtual systems in a controlled environment.
Students receive official exam prep test banks with mock exam questions broken down by domain to assess their level of readiness for the certification. We strongly recommend using these resources to prepare.
However, if you choose the direct eligibility route, review the domains covered in the exam and the exam blueprint based on your own knowledge and experience levels. You can self-assess your competency in each area and decide if you’re ready to attempt the exam.
Students in official CEH v13 training receive free retakes based on the package they enroll in. Retake exams are also available to others for a fee, if required.
Yes, all legitimate professional certifications have a recertification and maintenance process. The requirements are published under our EC-Council Continuing Education (ECE) Policy. Read the ECE Policy
Your options vary depending on your program, but we’re here to help.
EC-Council University: Log in to your MyECCU account and connect with your counselor.
EC-Council Academia Partner: Speak with your instructor to see if the university has included certification in the student resources. If not, you can write to [email protected] to connect with our student services team.
Training Questions
The total time it takes to become a certified ethical hacker can vary by student, but the typical answer is 5 days.
CEH official training is structured as a 5-day boot camp, with testing typically delivered at the end of the 5th day as a 4-hour exam.
Students who choose an on-demand or self-paced course through iClass or decide to defer their testing date may take longer to achieve the certification.
The CEH program and exam cover a variety of topics that center around the tactics and procedures required to be a tactical cybersecurity professional. Spanning the entire kill-chain process, CEH includes topics such as foot printing and reconnaissance, scanning, gaining access, maintaining access, and covering tracks.
This 5-phase ethical hacking process applies to a variety of scenarios, including traditional on-premises networks, cloud, hybrid, and IoT systems, and stretches across a variety of topologies and application environments.
Students learn a variety of tools and techniques throughout this process, as well as how hackers will utilize the same TTPs to hack into organizations.
While CEH covers the core domains of cybersecurity, it also includes AI cybersecurity skills, empowering students to master AI-driven cybersecurity skills and learn to hack AI systems based on the OWASP TOP 10.
CEH addresses the latest emerging attack vectors and security strategies, enabling students to stay current.
Security professionals attending this program will learn ethical hacking, including the Cyber Kill Chain, vulnerability assessment, and social engineering. You’ll explore how hackers operate, identify weaknesses in target systems, and apply remediation strategies to protect your organization from cyberattacks.
You’ll learn the core domains of cybersecurity, master the 5 phases of the ethical hacking framework, and automate all tasks using AI tools. So, you’ll learn not only how to use AI skills but also how to hack AI systems.
Ethical hacking is crucial to cybersecurity and offers extensive growth opportunities. If you want to learn ethical hacking on your own, it may seem easy, but it requires a lot of experience and knowledge.
You need to stay up-to-date with the latest hacking trends and resources in order to combat the escalating cyber threats. In addition to technical skills, you should also be familiar with basic hacking tools, penetration testing, and other aspects of ethical hacking, including the use of AI in cybersecurity.
The ethical hacking phases require extensive training and practical experience in areas such as attack vectors and penetration testing, SQL injection attacks, denial of service attacks, firewall attacks, password cracking, enumeration, and cloud computing.
There are many online resources available for learning ethical hacking, but it can be difficult to choose the right one. Therefore, it is important to have a structured learning method from a reliable source.
An accredited program like the EC-Council’s CEH (Certified Ethical Hacker) is considered the gold standard in ethical hacking and is recognized worldwide. If you’re passionate about this field and enjoy thinking outside the box, then you can build a successful career in this field.
While the CEH program and certification stand on their own and are not required to be taken as part of a track sequence, many students choose to focus on specific specializations, such as digital forensics, threat intelligence, penetration testing, or executive leadership.
To support those specializations, EC-Council offers a series of certification tracks that focus on stacking the competencies required to excel in those fields.
Discover the available tracks and types of careers they lead into.
Students attending official training for CEH, either through our online division iClass or in person at an Authorized Training Center, will receive the most comprehensive ethical hacking program on the market, enhanced with AI-driven skills.
The training resources stretch well beyond what you may be used to in a typical boot camp style course, as CEH not only supports you in the training program but also supports you after training and well into your career as a certified ethical hacker.
The unique framework in CEH – Learn, Certify, Engage, Compete – provides the following:
- Courseware: One-year access to all course materials, including cheat sheets.
- Hands-on labs: Six months of access to hands-on labs hosted in our Cyber Range to complement the 5 days of training.
- Exam vouchers: Vouchers with one-year validity and free retakes (available in selected CEH packages) if you are not successful on your first attempt.
- Exam prep: Practice in a mock exam environment to assess your readiness.
Post-certification support:
- Engage practice range:Participate in a mock ethical hacking engagement within a simulated organization – on your own time and at your own pace. Start with scanning and reconnaissance, identify vulnerabilities, and follow the CEH process to assess the target organization, leading all the way up to exploitation of the targets, including web servers, IoT devices, and IT/OT systems.
- Compete: After you complete your first engagement against the target organization, you’ll move on to Compete, where you can take part in monthly global hacking competitions available exclusively to certified ethical hackers. Face new scenarios each month, like malware analysis, ransomware, SCADA/ICS environments, hacking into power grids, web applications, and more.
Continuous Learning:
- Ethical hacking video libraries: To further support your continuous learning and skill development, you’ll also receive access to our curated Ethical Hacking Video Libraries through CodeRed, featuring 2 to 4-hour online courses on topics such as Python for Pen testers, Opensource intelligence, Wireshark for Ethical Hackers, Ethical Hacking with Nmap, Windows Penetration Testing Essentials, Next Gen Firewalls, Applied Secure Smart City, Burp Suite: Web App Pen Testing, and more.
Yes, every concept taught in CEH is supported by hands-on labs hosted in our Cyber Range. The training itself is split roughly 50/50 between lectures and discussions (50%) and hands-on labs (50%).
Additional hands-on practice is available in our 221 labs, featuring objective-based, CTF-style flags to challenge your critical thinking and applied knowledge. You’ll reinforce your ethical skills in our practice range, where you can hack, attack, and practice in live networks.
This is followed by 12 months of live competitions, all executed in our Cyber Range, ensuring 100% hands-on and applied learning experience.
We strongly believe you can’t really learn to hack just by reading a book. You must practice. If you are considering CEH, be prepared for an intensive hands-on program where you will practice and refine your skills as an ethical hacker.
Training is available globally through EC-Council iClass as well as through the world’s largest network of Authorized Training Centers (ATCs). EC-Council has over 900 ATCs across 145 countries.
If you are seeking credit-bearing programs at a college or university, EC-Council University offers bachelor’s and master’s programs in cybersecurity that incorporate CEH into the curriculum. Additionally, over 1,200 colleges and universities include CEH as part of their degree programs using our official Academia Courseware and Labs.
When selecting your training location, look for the Authorized Training Center Logo or the Official Academia Partner Logo to ensure you receive recognized and quality instruction.
Batches
Weekend Batches for Bhubaneswar Center:
Mar, 2026
Mar, 2026
May, 2026
Weekend Batches for Kolkata Center:
Mar, 2026
Mar, 2026
May, 2026
Apr, 2026
Apr, 2026
Jun, 2026
Weekday Batches for Siliguri Center:
Mar, 2026
Mar, 2026
May, 2026
Select Your Course Kit
While all CEH course kits have complete access to eCourseware and include an exam voucher, a few additional features and learning materials can be added to build deeper expertise and gain practical experience. This means that there is a CEH package to suit everyone’s learning requirements.

Learn, Certify, Engage & Compete
eCourseware

Exam Voucher

10 Ethical Hacking Video Library

6 Months of Official Labs

CEH Engage

Annual CEH Challenge Pass (12 CTF’s)

CEH Practical Exam

1 Exam Retake*

Rs. 76,999/-
Inclusive of all taxes

Learn & Certify
eCourseware

Exam Voucher

10 Ethical Hacking Video Library

6 Months of Official Labs

CEH Engage

Annual CEH Challenge Pass (12 CTF’s)

CEH Practical Exam

1 Exam Retake*

Rs. 51,999/-
Inclusive of all taxes
*Exam Retakes: This benefit provides candidates with the respective exam voucher on the ECC EXAM portal but excludes proctor administration fees which will apply for each attempt of the examination. Applicable to CEH Exam only. Please contact your training provider for details.
Member of: