For Enquiry, please email us [email protected]
For any complaint, write directly to CEO - [email protected]


Courses
Home
- All Courses
- CompTIA Global Courses
-
EC-Council Global Courses
- Certified Ethical Hacker - CEH v13 - AI Powered
- CEH Master
- Certified Penetration Testing Professional - CPENT
- CHFI v10 - Computer Hacking Forensic Investigator
- Certified SOC Analyst (CSA)
- Certified Cybersecurity Technician - CCT
- Certified Cloud Security Engineer - CCSE
- Web Application Hacking and Security - WAHS
- Certified Network Defender - CND v2
- EC-Council - Cyber Security Programs
- Post Graduation Courses
- Graduation Courses
- PG Diploma Courses
- Diploma Courses
- Vocational Training Courses
-
Skill Development Short Term Courses
- Ethical Hacking
- Computer Forensic
- SOC Analyst Fundamental
- Core Python Programming
- Advanced Python Programming
- CCNA Essentials & Ethical Hacking Combo
- Web Application Penetration Testing Level I
- Web Application Penetration Testing Level II
- Network Penetration Testing Level I
- Network Penetration Testing Level II
- Reverse Engineering & Malware Analysis
- Bug Bounty Hunting
- CCNA Essential
- Firewall Administration
- A-Z Defense in Comp Security - For Corporates
Bhubaneswar: +91 8100442829
Siliguri: +91 9007392360, +91 8100442827
ECSA V10
EC-Council Certified Security Analyst
- You are here:
- Home
- Courses
- ECSA V10 - EC-Council Certified Security Analyst

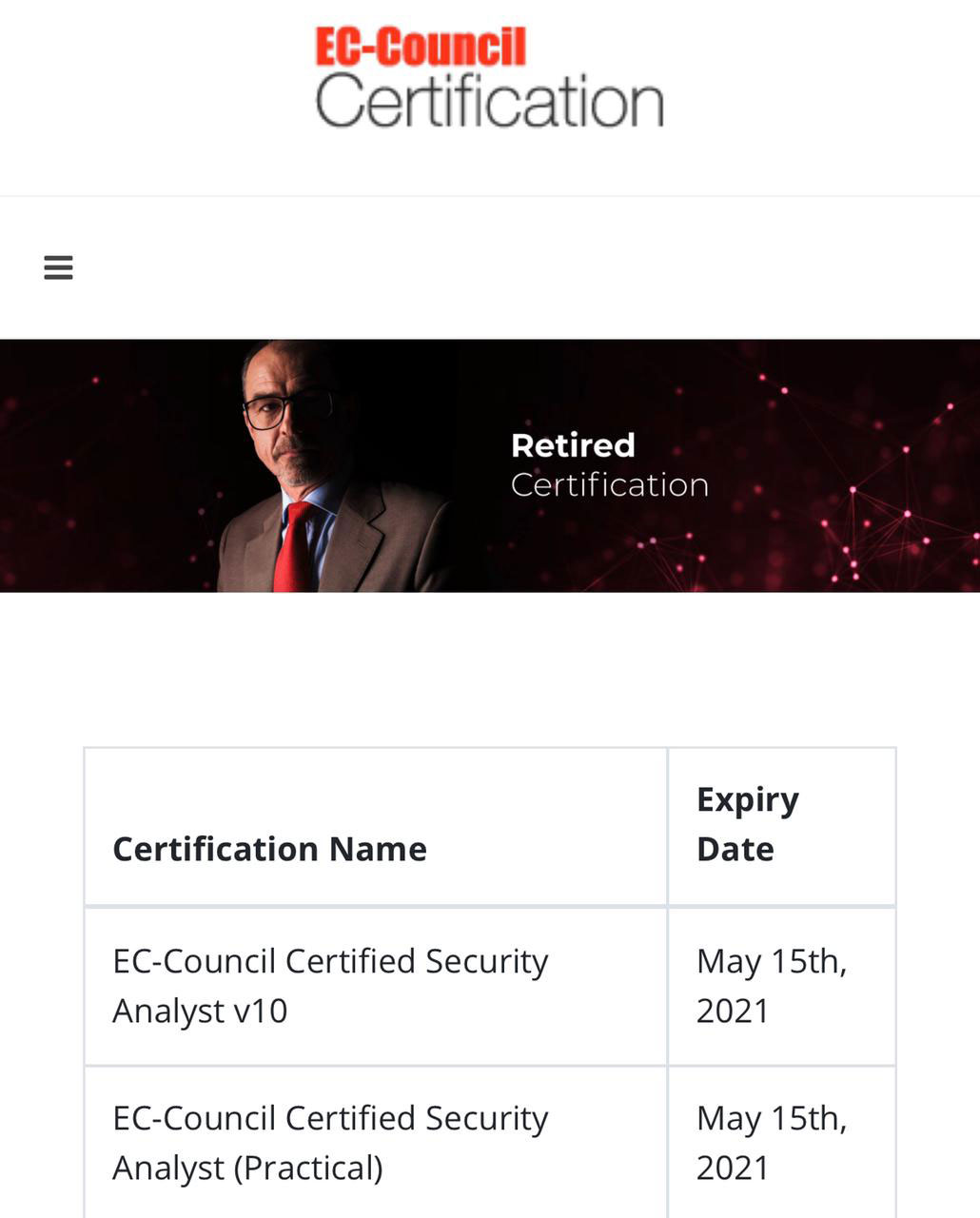
ECSA has been obsolete and the new course replacing ECSA is CPENT.
Enroll To CPENT Now »Subscribe for newsletter
Our Top Courses:
>
<
