Indian School of Ethical Hacking Kolkata is back with the Android Application Penetration Testing course. This course is intended for students and professionals who are intended to make career in mobile penetration testing domain. This course covers Mobile Application Security and Penetration Testing against a number of real world mobile applications that you can download and play with at any time. Obtain the ISOEH Certification and sharpen your practical skills with our 100% practical oriented course on Mobile Application Security and Penetration Testing. Our admission is open now, so enroll to course asap. For further course details, please call: +91 9830310550.
Duration
50 hours
Eligibility
Knowledge of one server side programming (PHP or ASP.net or JSP), Web Application Penetration testing (WAPT) and an Android device.
Details of WAPT can be obtained here:-
Web Application Penetration Testing
Course Fees
Class Room Training
Rs.30,000/-
Inclusive of all taxes
Online Training
Rs.40,000/-
Rs.30,000/-
Inclusive of all taxes
Your Course Path
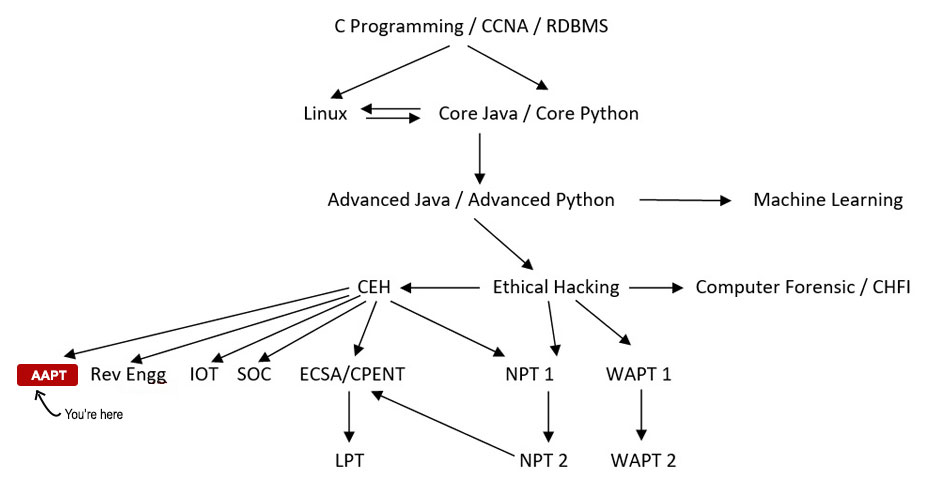
Course Details
- Basics of Android architecture
- Mobile application security models
- Scope of android security & Penetration testing
- Dalvik VM
- Different components of APK
- Android Sandbox
- Get to know Your Arsenals
- Setting up pentesting VM
- Testing through Emulator
- Testing through Mobile
- Fundamental of Android Studio
- APK lifecycle
- Fundamental of Reverse Engineering
- Reversing an APK
- How to root Your Device
- Rooted Device Vs Emulator
- Common Vulnerabilities related to traffic
- Proxies & sniffer
- Traffic analysis and manipulation
- Secure code review
- Understanding common mistakes made by programmer
- Analyze APK at run time
- Common tools & techniques
- Techniques of Android pentest
- Battle time with different APK
- Industries best practices for APT
- Analyze real Malware sample
- Malware battle
- Basic Android Forensic
- Android application penetration Test Report
Enroll Now
Fields marked with * are mandatory.


